In today’s digital landscape, safeguarding your systems against cyber threats is paramount. A critical component of any robust cybersecurity strategy is vulnerability scanning. Identifying weaknesses, from outdated software to misconfigured settings, is essential to prevent potential breaches. Manually conducting these scans, however, can be incredibly time-consuming and resource-intensive for IT teams. This is where vulnerability scanning tools become indispensable. By automating the vulnerability detection process, these tools empower organizations to proactively address risks and significantly strengthen their security posture without the overwhelming burden of manual work.
Vulnerability scanning tools are transformative, automating the analysis of your IT infrastructure to pinpoint security weaknesses. They can rapidly assess extensive networks and systems, simultaneously identifying vulnerabilities across numerous endpoints. This significant time-saving capability frees up your team’s valuable resources, allowing them to concentrate on strategic initiatives rather than being bogged down by manual scanning processes.
Beyond simple identification, vulnerability scanning tools deliver detailed reports on detected vulnerabilities. These reports not only highlight the weaknesses but also provide clear, actionable recommendations for remediation. This comprehensive guidance enables your IT team to prioritize and address the most critical vulnerabilities based on their severity and potential impact on your organization. This level of insight and control is crucial for effective security management.
This article explores essential features to look for in vulnerability scanning tools and presents a detailed overview of 14 leading solutions in 2024, equipping you with the knowledge to make informed decisions about your cybersecurity defenses. When considering vulnerability scanning solutions, businesses often look to industry benchmarks and analyst reports for guidance. While this article dives into specific tools and their functionalities, it’s worth noting that leading solutions in this space are frequently evaluated and recognized in industry reports such as the Gartner Magic Quadrant for Vulnerability Assessment. These reports offer a landscape view of vendors and their capabilities, helping organizations align their security needs with appropriate technology investments.
Key Features to Look For in an Effective Vulnerability Scanning Tool
Selecting the right vulnerability scanning tool is crucial for maintaining a strong security posture. Here are the advanced features that define an efficient and effective solution:
-
Comprehensive Scanning Capabilities: A superior vulnerability scanning tool should offer extensive scanning capabilities across all facets of your IT infrastructure. This includes networks, applications, and endpoints, both internal and external. Such comprehensive coverage ensures no potential security risk is overlooked, providing a holistic and reassuring sense of security.
-
Accuracy and Low False Positive Rate: Accuracy is paramount. Opt for a tool that excels at identifying genuine vulnerabilities while minimizing false positives. A low false positive rate is crucial for efficient security operations, ensuring your team can focus on real threats and avoid wasting time on false alarms, thereby maximizing productivity.
-
Customizable Scanning Options: Flexibility is key. A robust vulnerability scanning tool should provide customizable scanning options, allowing you to tailor the scanning process to your specific organizational needs. This includes scheduling scans, defining specific scan parameters, and prioritizing vulnerabilities based on severity, providing the adaptability to meet unique security requirements.
-
Integration with Existing Systems: Seamless integration is essential for streamlined operations. Seek a vulnerability scanning tool that integrates effortlessly with your current IT infrastructure and security management systems. Compatibility with tools like SIEM (Security Information and Event Management) solutions and ticketing systems enhances workflow efficiency and reduces manual effort, creating a more cohesive security ecosystem.
-
Comprehensive Reporting and Analytics: Actionable insights are derived from robust reporting. An ideal scanning tool should offer detailed reports on identified vulnerabilities, including severity levels and recommended remediation steps. Furthermore, analytics features are vital for tracking trends over time and prioritizing remediation efforts based on thorough risk assessments, enabling data-driven security decisions.
-
Scalability and Performance: Scalability is crucial for growth. As your organization expands, your attack surface increases. Ensure your chosen vulnerability scanning tool is scalable enough to accommodate your evolving infrastructure needs without compromising performance. It should efficiently handle large-scale scans without disrupting IT operations, maintaining consistent security coverage as you grow.
-
Regular Updates and Support: The threat landscape is dynamic. Cyber threats evolve constantly, so your vulnerability scanning tool must keep pace. Choose a solution that receives regular updates to its vulnerability database and scanning algorithms to ensure it remains effective against the latest threats. Reliable technical support is also essential for prompt troubleshooting and maximizing the tool’s effectiveness, ensuring continuous protection and operational stability.
Before we explore specific vulnerability scanning tools and their features, let’s introduce Zluri. Zluri offers a platform designed to streamline your security operations and empower you to make informed decisions about your organization’s security posture, particularly in the realm of SaaS application security.
0. Zluri: Enhances Your SaaS App Security
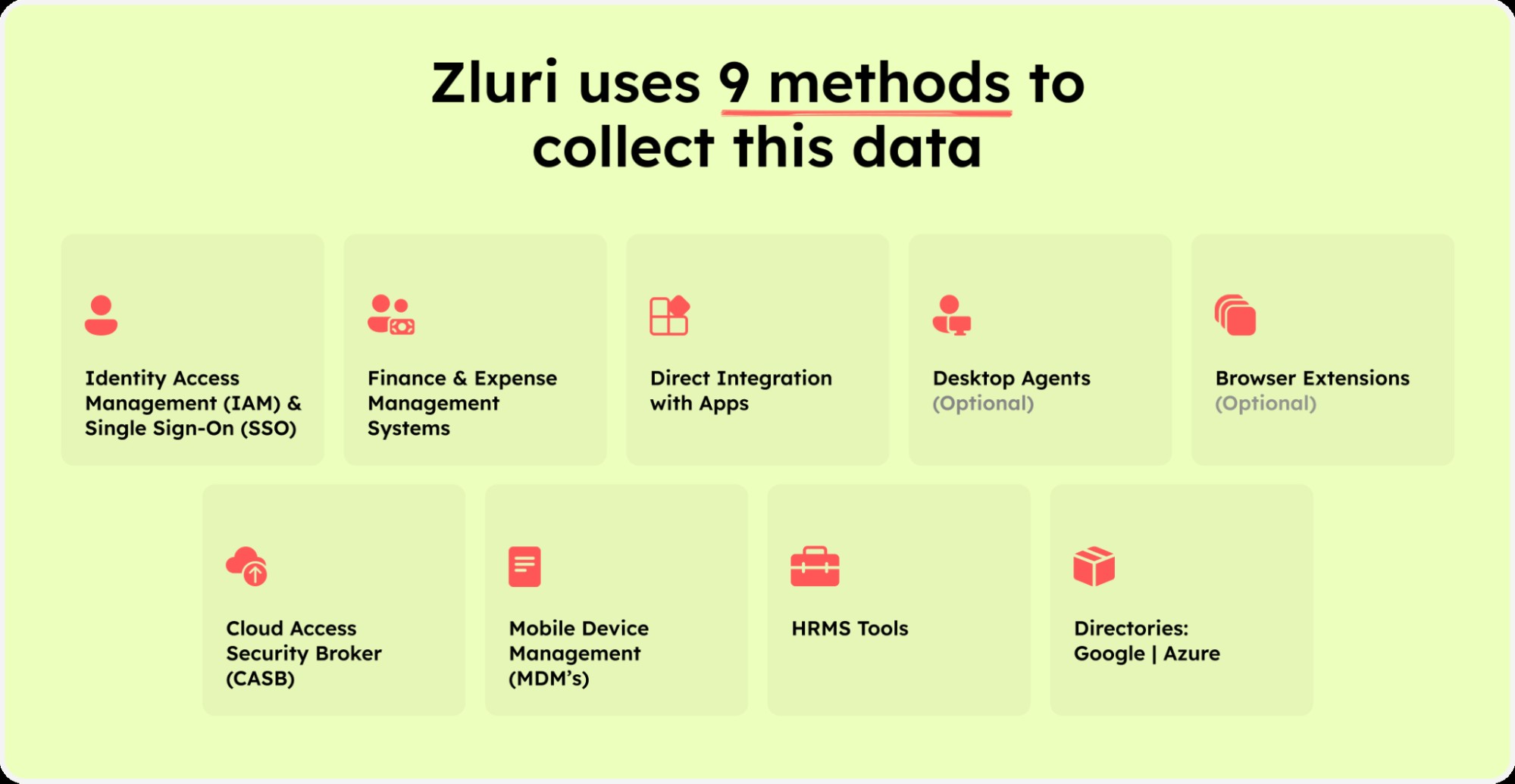
Zluri provides a comprehensive SaaS management platform designed to simplify IT operations and bolster your data security. Zluri empowers your IT team to discover and manage all SaaS applications within your company’s network. The platform employs nine distinct discovery methods, integrating with MDMs, IDPs & SSO, directly with applications, finance & expense management systems, CASBs, HRMS, directories, desktop agents (optional), and browser extensions (optional). This multifaceted approach ensures complete visibility into your SaaS landscape, effectively eliminating shadow IT.
Alt text: Diagram illustrating Zluri’s nine SaaS application discovery methods, including integrations with MDMs, IDPs/SSO, direct app connections, finance and expense systems, CASBs, HRMS, directories, desktop agents, and browser extensions.
Once applications are discovered, Zluri enables in-depth threat analysis, risk assessment, and compliance checks. Let’s examine these capabilities:
Threat & Risk Insights
Zluri aids in identifying potential threats by assigning threat levels to each application. For example, if an application has the capability to modify or delete files in Google Drive, Zluri immediately flags it with a high threat level. This actionable intelligence empowers you to make informed decisions, avoiding applications that pose significant risks to data confidentiality.
Alt text: Screenshot of Zluri’s interface showcasing threat level insights for various SaaS applications, highlighting high, medium, and low threat indicators.
Furthermore, Zluri extends beyond traditional risk assessments by providing dynamic risk scores. By analyzing data flows and single sign-on interactions, Zluri determines a precise risk level for each SaaS application. This precision allows your team to strategically allocate security resources based on real-time insights.
Alt text: Example of Zluri’s dynamic risk scoring system for SaaS applications, displaying numerical risk scores and associated risk levels based on data flow analysis.
Risk Scopes
By defining risk scopes, Zluri clarifies the exact threat potential that each SaaS application introduces to your IT environment. This detailed understanding enables you to tailor risk mitigation strategies specifically to your organization’s unique needs.
Alt text: Visual representation of Zluri’s risk scopes, illustrating how different SaaS applications pose varying levels of threat within an IT environment.
Security & Compliance Data
Zluri provides comprehensive security and compliance information for every SaaS application within your organization. From tracking critical events to assessing shared data information, Zluri equips your team with the necessary capabilities to maintain robust security.
Alt text: Dashboard view from Zluri showcasing security and compliance data for SaaS applications, including compliance statuses and security event tracking.
Furthermore, compliance and security probes enhance your ability to align your IT infrastructure with industry standards, reducing the risk of regulatory non-compliance.
Moreover, your team can leverage Zluri’s proactive approach to receive real-time alerts about critical applications with high threat levels. This empowers them to take immediate action, preventing potential cyber threats before they escalate. Zluri transforms vulnerability scanning into a proactive, data-driven, and streamlined process by providing a holistic view of the risk landscape.
Book a demo!
14 Vulnerability Scanning Tools
Let’s delve into a detailed examination of 14 prominent vulnerability scanning tools available today.
1. ManageEngine Vulnerability Manager Plus
Alt text: Screenshot of ManageEngine Vulnerability Manager Plus user interface, displaying dashboards and vulnerability data.
ManageEngine Vulnerability Manager Plus is a powerful tool designed to strengthen your organization’s cybersecurity defenses. It offers comprehensive vulnerability scanning, enabling you to scan network devices, servers, endpoints, and applications for potential security weaknesses.
This thorough scanning ensures that no vulnerability is overlooked, allowing your team to address security risks promptly and effectively.
Key Features
-
Automated Patch Management: Vulnerability Manager Plus streamlines patch management with automated patch deployment. This feature automates the distribution of security patches and updates to vulnerable systems, ensuring timely resolution of critical vulnerabilities and reducing the risk of exploitation.
-
Real-time Vulnerability Alerts: The tool provides real-time vulnerability alerts, notifying you of newly discovered vulnerabilities and changes in the security posture of your network infrastructure. This proactive approach keeps you ahead of emerging threats, enabling immediate action to mitigate potential risks.
-
Customizable Scanning Policies: Vulnerability Manager Plus allows for the creation of customizable scanning policies tailored to your organization’s specific needs. Whether defining scan schedules, specifying target assets, or configuring scan parameters, you have the flexibility to align scanning policies with your unique security requirements.
-
Comprehensive Reporting: The platform generates comprehensive reports providing detailed insights into identified vulnerabilities within your network infrastructure. These reports include actionable remediation recommendations, empowering informed decisions on how best to protect your organization’s assets.
Customer Rating
- Capterra: 4.7/5
2. Balbix
Alt text: Balbix vulnerability scanning tool dashboard, highlighting risk scores, vulnerability trends, and security insights.
Balbix’s vulnerability scanning tool is a cutting-edge solution designed to give you control over your organization’s security. With its innovative approach and advanced capabilities, Balbix empowers IT managers and security professionals to proactively identify, prioritize, and remediate security vulnerabilities across their network infrastructure.
Key Features
-
Predictive Risk Analytics: Balbix uses predictive risk analytics to assess the likelihood and impact of potential security vulnerabilities. By analyzing data from network traffic, asset configurations, and threat intelligence feeds, Balbix delivers actionable insights into the vulnerabilities that pose the greatest risk to your organization.
-
Continuous Monitoring: Balbix offers continuous monitoring capabilities, automatically scanning your network for new vulnerabilities and configuration changes. This real-time monitoring ensures you are promptly alerted to emerging threats, enabling immediate action to mitigate risks and strengthen security defenses.
-
Comprehensive Asset Visibility: Balbix provides comprehensive asset visibility, allowing you to identify all devices and systems connected to your network. This complete visibility ensures no device goes unnoticed, allowing you to assess security risks associated with each asset and prioritize remediation efforts effectively.
-
Integration with Security Ecosystem: Balbix seamlessly integrates with existing security tools and platforms, such as SIEMs, firewalls, and endpoint protection systems. This straightforward integration process requires no complex configurations, allowing you to leverage your existing security infrastructure investments without hassle.
-
Actionable Insights and Recommendations: Based on vulnerability analysis, Balbix generates actionable insights and recommendations. These insights enable informed decisions about prioritizing remediation efforts and allocating resources to effectively mitigate potential risks.
Customer Rating
- G2: 4.5/5
3. Tenable
Alt text: Tenable vulnerability management platform showing vulnerability details, asset information, and security metrics.
Tenable is a leading cybersecurity solution provider, distinguished by unique features that enhance your organization’s security posture. At the heart of Tenable’s offerings is its robust vulnerability scanning tool, a market standout. This tool empowers you to proactively identify, prioritize, and remediate security vulnerabilities across your network infrastructure, setting Tenable apart from competitors.
Key Features
-
Comprehensive Asset Discovery: Tenable’s vulnerability scanning tool offers comprehensive asset discovery, identifying all devices and systems connected to your network. This visibility ensures no device is overlooked, allowing you to assess security risks associated with each asset and prioritize remediation efforts accordingly.
-
Advanced Vulnerability Detection: Tenable employs advanced detection techniques to identify vulnerabilities across a wide range of devices, applications, and operating systems. From known vulnerabilities to zero-day exploits and misconfigurations, Tenable’s scanning capabilities provide a complete view of your organization’s security posture.
-
Continuous Monitoring: Tenable provides continuous monitoring, automatically scanning your network for new vulnerabilities and configuration changes. This real-time monitoring ensures prompt alerts for emerging threats, enabling immediate action to mitigate risks and strengthen security defenses.
-
Risk-Based Prioritization: Tenable prioritizes vulnerabilities based on their severity and potential impact on your organization’s security posture. By focusing on the most critical vulnerabilities first, you can allocate resources more effectively and minimize exploitation risks.
-
Integration with Security Ecosystem: Tenable seamlessly integrates with existing security tools and platforms, allowing you to leverage your security infrastructure investments. Whether SIEM solutions, ticketing systems, or threat intelligence feeds, Tenable’s integration capabilities ensure access to the information needed for effective vulnerability management and security incident response.
Customer Rating
- G2: 4.5/5
- Capterra: 4.7/5
4. Intruder
Alt text: Intruder’s vulnerability scanning interface, showcasing scan results, vulnerability severity, and security recommendations.
Intruder is a proactive vulnerability scanning tool focused on empowering you to strengthen your organization’s cybersecurity defenses. With its intuitive interface and advanced scanning capabilities, Intruder allows you to detect, prioritize, and remediate security vulnerabilities across your network infrastructure, ensuring a resilient security posture. Designed for both seasoned cybersecurity professionals and network administrators with basic security knowledge, Intruder is user-friendly and accessible to all.
Key Features
-
Continuous Monitoring: Intruder’s rapid scanning capabilities provide continuous monitoring, automatically scanning your network for new vulnerabilities and configuration changes. This ensures prompt alerts for emerging threats, allowing for immediate action to mitigate potential risks and strengthen security.
-
Cloud-Based Scanning: Intruder’s cloud-based architecture enables seamless and scalable vulnerability scanning across your organization’s network infrastructure. With no need for on-premises hardware or software installation, you can quickly deploy and manage scans from anywhere, ensuring flexibility and ease of use.
-
Comprehensive Vulnerability Assessment: Intruder conducts thorough vulnerability assessments, scanning network devices, applications, and configurations to identify potential security weaknesses. The tool provides detailed insights into vulnerability nature and severity, empowering you with a comprehensive understanding to prioritize remediation efforts based on organizational risk levels.
-
Real-Time Alerts and Notifications: Intruder offers real-time alerts and notifications, ensuring prompt information about critical vulnerabilities or security incidents. For instance, you might receive an alert for a newly detected vulnerability or a notification when a known vulnerability has been successfully patched. This proactive approach enables quick response to potential threats, minimizing impact on operations and data.
-
Integration with Security Ecosystem: Intruder seamlessly integrates with existing security tools and platforms, allowing you to leverage your security infrastructure investments. This integration, achieved through APIs and connectors, facilitates information exchange between Intruder and your security ecosystem. Whether SIEM solutions, ticketing systems, or threat intelligence feeds, Intruder’s integration ensures access to the information needed for effective vulnerability management and security incident response.
Customer Rating
- G2: 4.8/5
- Capterra: 5/5
5. Acunetix
Alt text: Acunetix dashboard interface showing web application scan results, vulnerability types, and remediation advice.
Acunetix is a leading vulnerability scanning tool focused on strengthening your organization’s cybersecurity defenses. With its advanced scanning capabilities and user-friendly interface, Acunetix empowers you to proactively identify, prioritize, and remediate security vulnerabilities across your network infrastructure, ensuring a robust security posture.
Key Features
-
Advanced Web Application Scanning: Acunetix specializes in web application scanning, offering advanced capabilities to identify vulnerabilities in web applications, APIs, and single-page applications (SPAs). This focus on web application security ensures effective protection against common web-based attacks, such as SQL injection, cross-site scripting (XSS), and CSRF.
-
Deep Crawl and Scan: Acunetix performs deep crawls of websites and web applications, thoroughly scanning all accessible pages and components for security vulnerabilities. This comprehensive scanning approach ensures no area is overlooked, uncovering hidden vulnerabilities that may be missed by other scanning tools.
-
Comprehensive Reporting: Acunetix generates comprehensive reports providing detailed insights into identified vulnerabilities within your organization’s web applications. These reports include actionable remediation recommendations and insights into emerging threats and trends, enabling informed decisions about protecting your web assets.
-
Integration with Development Tools: Acunetix seamlessly integrates with popular development tools and platforms, allowing you to incorporate vulnerability scanning into the software development lifecycle (SDLC). By integrating with tools like Jenkins, JIRA, and GitHub, Acunetix helps organizations adopt a DevSecOps approach to security, ensuring security is built into the development process from the outset.
Customer Rating
- G2: 4.2/5
- Capterra: 4.5/5
6. GFI LanGuard
Alt text: GFI LanGuard console interface, highlighting network security status, patch management features, and vulnerability scan results.
GFI LanGuard, a robust vulnerability management solution, is designed with an intuitive interface that empowers IT professionals to safeguard their organization’s network infrastructure. Its easily navigable advanced features allow you to confidently identify, prioritize, and remediate security vulnerabilities across your entire network, ensuring a proactive cybersecurity approach.
Key Features
-
Multi-Platform Support: GFI LanGuard provides comprehensive protection across multi-platform environments, supporting vulnerability scanning and management across Windows, macOS, and Linux operating systems. This versatility ensures coverage for all devices within your network, regardless of operating system, providing robust protection against potential security threats.
-
Effortless Patch Management: GFI LanGuard’s automated patch management capabilities streamline the process of deploying security patches and updates to vulnerable systems, saving valuable time. By automating patch deployment, GFI LanGuard significantly reduces exploitation risks, ensuring timely application of critical security updates and freeing up your time for other important tasks.
-
Detailed Vulnerability Assessment: GFI LanGuard conducts thorough vulnerability assessments, scanning network devices, applications, and configurations to identify potential security weaknesses. The tool provides detailed insights into vulnerability nature and severity, allowing you to prioritize remediation efforts based on organizational risk levels.
-
Integration with Third-Party Tools: GFI LanGuard seamlessly integrates with third-party security tools and platforms, allowing you to leverage existing security infrastructure investments. Whether SIEM solutions, ticketing systems, or threat intelligence feeds, GFI LanGuard’s integration capabilities ensure access to the information needed for effective vulnerability management and security incident response.
-
Comprehensive Reporting: GFI LanGuard generates comprehensive reports providing actionable insights into identified vulnerabilities within your network. These reports include detailed remediation recommendations and insights into emerging threats and trends, enabling informed decisions on how best to protect your organization’s assets.
Customer Rating
- G2: 4.2/5
- Capterra: 3.8/5
7. Qualys
Alt text: Qualys vulnerability management platform dashboard, displaying global security posture, vulnerability status, and compliance metrics.
Qualys, a well-known vulnerability scanning tool provider, offers a comprehensive suite of solutions designed to address the evolving threat landscape. Central to its offerings is its powerful vulnerability scanning tool, empowering you to proactively identify and mitigate a wide range of security vulnerabilities, including software weaknesses, misconfigurations, and weak passwords, across your organization’s network infrastructure.
With its robust feature set and intuitive user-friendly interface, Qualys provides the capabilities needed to strengthen your organization’s security posture and protect against potential threats. The tool is designed for ease of use, even for non-technical users, making it accessible across your organization.
Key Features
-
Global Visibility: Qualys provides global visibility into your organization’s security posture, allowing you to identify vulnerabilities across all network assets, including endpoints, servers, cloud environments, and mobile devices. This comprehensive view enables you to prioritize remediation efforts based on the most critical vulnerabilities, ensuring effective resource allocation.
-
Continuous Monitoring: With Qualys, vulnerability scanning is an ongoing process, not a one-time event. The tool offers continuous monitoring capabilities, automatically scanning your network at regular intervals for new vulnerabilities and configuration changes. This ensures constant awareness of potential security risks, enabling immediate mitigation actions.
-
Comprehensive Reporting: Qualys generates comprehensive reports that not only identify vulnerabilities within your network but also provide detailed insights, actionable remediation recommendations, and insights into emerging threats and trends. This level of detail ensures you are fully informed and in control of your cybersecurity strategy, providing confidence in your decision-making.
-
Integration with Security Ecosystem: Qualys seamlessly integrates with existing security tools and platforms, allowing you to leverage your security infrastructure investments. Whether SIEM solutions, ticketing systems, or threat intelligence feeds, Qualys’ integration capabilities ensure access to the information needed for effective vulnerability management and network protection.
Customer Rating
- G2: 4.4/5
- Capterra: 3.9/5
8. BeSecure
Alt text: BeSecure vulnerability scanning results interface, showing vulnerability severity, affected assets, and remediation steps.
BeSecure, a reliable vulnerability scanning tool, empowers you to protect your network infrastructure from potential security threats. Designed with a deep understanding of the evolving cybersecurity landscape, BeSecure offers comprehensive features for thorough vulnerability detection and proactive risk mitigation. This robust defense mechanism is accessible to organizations of all sizes, ensuring network security is within your control.
Key Features
-
Comprehensive Scanning Capabilities: BeSecure’s scanning capabilities are comprehensive, thoroughly examining your network infrastructure. From endpoints to servers, databases, and cloud environments, BeSecure’s holistic approach ensures identification of vulnerabilities across all network aspects. This thoroughness allows for targeted remediation, providing a strong sense of security.
-
Automated Vulnerability Assessment: BeSecure automates the vulnerability assessment process, minimizing manual effort and streamlining security operations. With automated scanning schedules and real-time updates, you can stay ahead of potential threats and ensure your networks remain secure against emerging vulnerabilities.
-
Prioritization of Vulnerabilities: BeSecure prioritizes vulnerabilities based on their severity and potential impact on your organization’s security posture. It uses a proprietary algorithm considering factors like vulnerability exploitability, potential damage, and remediation ease. This prioritization enables focused attention and resources on critical vulnerabilities, reducing exploitation likelihood and minimizing overall risk.
-
Customizable Reporting: BeSecure’s reporting features are detailed and customizable. They provide insights into identified vulnerabilities within your network, tailored to meet specific compliance requirements or organizational needs. This reporting flexibility empowers informed decisions and ensures transparency across your organization, giving full control over network security.
-
Integration with Security Ecosystem: BeSecure seamlessly integrates with existing security tools and platforms, enhancing overall security effectiveness. This integration reduces manual data entry, improves data accuracy, and allows for centralized management of security operations. Whether SIEM solutions, ticketing systems, or threat intelligence feeds, BeSecure’s integration capabilities ensure cohesive security ecosystem operation, enabling timely threat detection and response.
Customer Rating
- G2: 3/5
9. Nexpose
Alt text: Nexpose vulnerability management tool interface, showing real-time risk scores, asset vulnerabilities, and security trends.
Nexpose, developed by Rapid7, is a comprehensive vulnerability management tool. It aids in identifying, assessing, and addressing security vulnerabilities across your network environments. As your organization grows and adapts, dynamic security solutions become essential. Nexpose meets this need by providing comprehensive scanning across physical, virtual, cloud, and mobile environments, ensuring a holistic security approach.
Key Features
-
Real-Time Risk Scoring: Nexpose excels with its real-time risk scoring system, updating as new vulnerabilities are discovered and network configurations change. This feature ensures you have the most current information regarding your security posture, enabling prompt and informed decision-making.
-
Live Monitoring of the Network: Unlike tools that scan periodically, Nexpose offers continuous monitoring, constantly checking for new devices, changes, and emerging threats. This capability ensures surveillance of all network aspects and immediate detection of any new risks.
-
Integrated Threat Feeds: Nexpose integrates live threat feeds to ensure vulnerability checks are up-to-date with the latest threat intelligence. This integration helps anticipate potential attacks based on recent trends and known vulnerabilities, enhancing the proactive capabilities of your security strategies.
-
Automated Compliance Assessments: For organizations with regulatory requirements, Nexpose simplifies compliance by providing automated assessments against standards like PCI-DSS, HIPAA, and more. This reduces compliance burden and helps maintain a clear view of compliance status at all times.
-
Actionable Reporting: The tool generates detailed reports that not only identify vulnerabilities but also provide actionable insights and remediation recommendations. These customizable reports can be tailored to different stakeholder needs, from technical teams to executive management, ensuring all relevant parties are informed and equipped to act.
Customer Rating
- G2: 4.4/5
- Capterra: 4.5/5
10. Wiz
Alt text: Wiz cloud security platform dashboard, showing cloud environment vulnerabilities, misconfigurations, and compliance status.
Wiz is a cutting-edge vulnerability scanning tool, addressing the complex security needs of modern IT infrastructures. As cloud environments become more prevalent, tools providing comprehensive insights into both cloud-based and on-premise systems are increasingly sought after. Wiz stands out by offering deep visibility into the security health of entire networks, making it essential for proactive security management.
Key Features
-
Deep Security Insights: Wiz distinguishes itself by providing deep insights into security vulnerabilities across your entire network. By scanning and analyzing both cloud configurations and on-premises systems, Wiz ensures no infrastructure component is overlooked, from virtual machines to containerized applications.
-
Context-Aware Risk Assessment: Wiz’s context-aware risk assessment capability sets it apart. It not only identifies vulnerabilities but also understands their context. This means you receive actionable intelligence about the most critical vulnerabilities, based on specific system usage and configuration.
-
Continuous Monitoring: This feature is crucial for real-time vulnerability detection, especially in dynamic cloud environments with frequent and rapid changes. Continuous monitoring empowers you to stay ahead of potential threats by providing immediate alerts about new risks.
-
Seamless Integration: Wiz seamlessly integrates with your existing tools and workflows. Whether CI/CD pipelines, identity management systems, or other security platforms, Wiz enhances overall security measures by working in tandem with these tools, extending your security reach without adding complexity.
-
Automated Compliance Checks: This feature simplifies ensuring your environment adheres to standards like GDPR, HIPAA, and PCI DSS. Automated reports provide detailed insights and recommendations, making compliance management more straightforward and less prone to errors.
Customer Rating
- G2: 4.7/5
11. Greenbone Vulnerability Management/OpenVAS
Alt text: Greenbone Security Manager interface, displaying vulnerability scan results, security alerts, and compliance information.
OpenVAS, the scanner component of Greenbone vulnerability management, is a prominent open-source vulnerability scanning and management tool. Originally forked from the popular Nessus scanner, OpenVAS has evolved into a robust, standalone vulnerability scanner that is both powerful and freely available. For IT managers aiming to enhance organizational security without significant commercial software investments, OpenVAS offers a cost-effective solution.
Key Features
-
Comprehensive Scanning Capabilities: OpenVAS is known for its extensive scanning capabilities, covering a wide range of vulnerabilities across various systems and applications. The tool regularly updates its vulnerability tests from a central feed, ensuring detection of the latest security threats, including those in new software releases and emerging exploits.
-
High Configurability: OpenVAS stands out for its adaptability. You can customize the scanning process to meet specific organizational requirements, deciding scan targets, depth, and frequency. This versatility simplifies aligning security measures with organizational policies and compliance mandates.
-
Automated Scanning and Reporting: OpenVAS automates both scanning and detailed report generation. This automation saves valuable time and resources, allowing focus on analyzing and responding to threats rather than managing the scanning process itself. Customizable reports provide detailed insights into detected vulnerabilities, helping prioritize remediation based on risk.
-
Wide Community Support: As an open-source platform, OpenVAS benefits from robust community support. Users and developers actively contribute to its vulnerability database and offer troubleshooting assistance via forums and channels. This community-driven approach ensures the tool remains current and effective against a wide range of vulnerabilities, providing security and reliability.
-
Integration with Third-Party Tools: Despite being open-source, OpenVAS offers good integration capabilities with other security tools. This interoperability is crucial for building a cohesive security infrastructure where different components work together seamlessly for enhanced protection.
Customer Rating
- G2: 4.4/5
- Capterra: 4.1/5
12. Cisco Vulnerability Management
Alt text: Cisco Vulnerability Management dashboard, displaying network vulnerability status, threat analysis, and security recommendations.
Cisco offers a robust vulnerability management solution tailored to the dynamic needs of modern enterprises. Cisco’s solution is designed to strengthen networks by identifying, analyzing, and mitigating a wide range of vulnerabilities, including software weaknesses, misconfigurations, and weak passwords. This enhances security posture and minimizes risks in an increasingly threat-prone digital environment.
Cisco’s vulnerability management solution seamlessly integrates with other Cisco security products, providing a unified security posture. This integration allows information and threat intelligence sharing across platforms, enhancing overall security operation effectiveness and giving you control.
Key Features
-
Advanced Vulnerability Scanning: Cisco’s tool uses advanced scanning technology to thoroughly examine network devices, systems, and applications for security vulnerabilities. This comprehensive scanning not only detects known vulnerabilities but also anticipates potential future threats based on system behaviors and configurations, providing robust protection.
-
Continuous Monitoring and Protection: Cisco excels in continuous monitoring. Unlike periodic scans offering snapshots, Cisco provides real-time monitoring, ensuring immediate detection of new threats or vulnerabilities as they arise. This ongoing vigilance includes monitoring for known vulnerabilities, emerging threats, and zero-day vulnerabilities, helping maintain a consistently secure environment.
-
Prioritization of Threats: With vast data from scanning, Cisco helps prioritize vulnerabilities. It assesses the potential impact and exploitability of each vulnerability, enabling your team to address the most critical issues first, optimizing resource use and ensuring efficient risk management.
-
Customizable Reporting: Cisco understands diverse organizational reporting needs. Their vulnerability management tools offer customizable reporting, allowing you to generate detailed reports based on specific compliance requirements or security protocols. These reports can include vulnerability assessments, trend analyses, and executive summaries, providing necessary insights for audits and informed security decisions.
Customer Rating
- G2: 4.3/5
13. McAfee Vulnerability Manager
Alt text: McAfee Vulnerability Manager user interface, displaying vulnerability status, risk levels, and remediation options.
McAfee Vulnerability Manager, a robust security solution, empowers your organization to protect its networks from security threats. It simplifies identifying, categorizing, and managing vulnerabilities within your IT infrastructure. This user-friendly tool is essential for organizations aiming to maintain a secure network environment, reducing unauthorized access and data breach risks.
Key Features
-
Comprehensive Vulnerability Scanning: McAfee Vulnerability Manager offers thorough scanning capabilities, detecting security weaknesses across your entire network. By scanning operating systems, applications, and network devices, it identifies exploitable vulnerabilities. This ensures all potential threats are identified and addressed, providing robust defense against security breaches.
-
Real-Time Threat Intelligence: McAfee Vulnerability Manager proactively leverages real-time threat intelligence to stay updated on the latest vulnerabilities and exploits. This reassures you that the tool is always prepared to take immediate action on emerging threats, ensuring constant network protection against the latest security risks.
-
Prioritization and Risk Assessment: A standout feature of McAfee Vulnerability Manager is its ability to prioritize vulnerabilities based on risk level. This allows you to focus efforts on mitigating the most critical vulnerabilities first, optimizing resource allocation for maximum security impact.
-
Automated Compliance Reports: For businesses concerned with regulatory compliance, McAfee Vulnerability Manager automates compliance report generation, saving time and effort. These reports help demonstrate compliance with various security standards, ensuring your business meets required security protocols without audit hassles.
-
Integration Capabilities: McAfee Vulnerability Manager seamlessly integrates with other security tools and systems. This integration enhances your organization’s security posture by enabling coordinated threat responses and streamlined security operations management.
Customer Rating
- G2: 4.3/5
- Capterra: 4.8/5
14. Aikido
Alt text: Aikido vulnerability scanning platform interface, showcasing vulnerability prioritization, threat intelligence integration, and remediation workflows.
Aikido, a recognized cybersecurity leader, offers a robust vulnerability scanning solution. This tool effectively addresses the challenge of safeguarding your systems from cyberattacks. Understanding Aikido’s vulnerability scanning tool features and capabilities can help enhance your security posture and mitigate potential risks.
Key Features
-
Adaptive Scanning Algorithms: Aikido uses adaptive scanning algorithms to intelligently identify and prioritize vulnerabilities based on their severity and potential impact on your organization’s security posture. This ensures focused resource allocation on addressing the most critical vulnerabilities first, minimizing exploitation risks.
-
Real-time Threat Intelligence: Aikido integrates real-time threat intelligence feeds to provide up-to-date information about emerging threats and vulnerabilities. By leveraging this intelligence, Aikido enables proactive threat detection and response, ensuring you stay ahead of evolving cyber threats and take immediate action to mitigate potential risks.
-
Automated Remediation Workflows: Aikido offers automated remediation workflows to streamline the process of addressing security vulnerabilities. You can automate the deployment of security patches and updates to vulnerable systems, reducing remediation time and effort and minimizing exposure windows.
-
Scalable Architecture: Aikido features a scalable architecture, allowing you to easily scale vulnerability scanning operations to meet your organization’s needs. Whether scanning small networks or large enterprise environments, Aikido adapts to organizational scale, ensuring no vulnerabilities are overlooked.
-
Comprehensive Reporting and Analytics: Aikido generates comprehensive reports and analytics providing detailed insights into identified vulnerabilities within your network infrastructure. These reports help you make informed decisions on how best to protect your organization’s assets.
Customer Rating
- G2: 4.7/5
- Capterra: 4.6/5
Enhancing Security Through Informed Decision-Making
For IT managers, exploring multiple vulnerability scanning solutions provides invaluable insights into the diverse options available. This process not only helps select the most suitable tool for your organization but also broadens your understanding of the cybersecurity landscape.
Each organization has unique requirements and infrastructure complexities, necessitating a tailored cybersecurity approach. By exploring various vulnerability scanning solutions, you conduct a thorough evaluation of features, functionalities, and compatibility factors. This ensures the selected tool aligns optimally with your organization’s specific needs. When considering vulnerability scanning tools, many organizations look to industry-recognized evaluations like the Gartner Magic Quadrant for Vulnerability Assessment. These evaluations provide a comparative analysis of vendor strengths and capabilities, aiding in strategic decision-making and ensuring alignment with industry best practices.
Frequently Asked Questions (FAQs)
1: Which vulnerability scanning tool is also known as a sniffer?
Wireshark, commonly known as a sniffer, network analyzer, or network protocol analyzer, is a versatile tool. It is invaluable for businesses requiring robust network management and security analysis. It is also a leading open-source solution for network traffic profiling and packet analysis.
2: What are the types of vulnerability scanning tools?
Here are several types of vulnerability scanning tools:
- Web application vulnerability scanning tool
- Network vulnerability scanning tool
- Cloud vulnerability scanning tool
- Database vulnerability scanning tool
- Security vulnerability scanning tool
- Open source vulnerability scanning tool
3: What is penetration testing?
Penetration testing, or pen testing, is a strategic security practice involving cybersecurity experts seeking out and exploiting vulnerabilities within computer systems. Through simulated attacks, the primary aim is to uncover potential weak points in a system’s defenses, strengthening it against real-world threats.