Open Source Intelligence (OSINT) is indispensable for navigating the complexities of cybersecurity and understanding your digital footprint. Especially when aiming to minimize your attack surface, OSINT tools are paramount. This importance is reflected in the OSINT market’s significant growth, which is projected to reach $29.19 billion by 2026 from a $5.02 billion valuation in 2018.
This article delves into the crucial role of network scanning tools within OSINT, specifically focusing on the Best Network Scanning Tool That Provides Graphs And Pictures. We will explore how these visual tools enhance intelligence gathering and provide actionable insights.
The Power of Visuals in Network Scanning for OSINT
Open Source Intelligence (OSINT) is fundamentally about:
- Gathering information from publicly accessible sources.
- Transforming raw data into understandable, actionable intelligence.
- Meeting the increasing demand for insights in our expanding digital world.
- Serving both government and commercial sectors for purposes like reconnaissance and improved cyber crime investigations.
- Delivering crucial insights into market dynamics and brand positioning.
OSINT leverages a broad spectrum of publicly available data sources and techniques, including broadcast media, social media platforms, and websites. The data collected spans various formats, from text to video and audio. Modern OSINT tools incorporate advanced technologies such as machine learning and neural networks to efficiently process and analyze this vast amount of data, identifying trends, patterns, and critical information.
In the realm of network scanning within OSINT, the ability to visualize data through graphs and pictures is a game-changer. Instead of sifting through lines of text output, visual representations offer immediate comprehension of network structures, vulnerabilities, and potential attack vectors. This visual approach is particularly beneficial for:
- Rapid Assessment: Quickly understanding the network topology and identifying key components.
- Vulnerability Identification: Spotting open ports, services, and potential weaknesses at a glance.
- Communication of Findings: Clearly presenting complex network data to stakeholders, regardless of their technical expertise.
- Enhanced Analysis: Recognizing patterns and anomalies that might be missed in text-based reports.
The Evolution of Network Scanning in OSINT
Initially, OSINT primarily focused on analyzing traditional media. However, the digital age has shifted the focus to the internet’s vast information resources. Network scanning tools have evolved alongside this shift, moving from basic command-line utilities to sophisticated platforms with graphical user interfaces and visualization capabilities.
Early network scanning tools provided text-based outputs, requiring analysts to manually interpret and visualize the data. Today’s best network scanning tools integrate graphical interfaces that automatically generate graphs and pictures, simplifying the analysis process. This evolution is driven by the increasing complexity of networks and the need for faster, more intuitive intelligence gathering.
The future of network scanning tools in OSINT is strongly influenced by artificial intelligence and machine learning. These technologies promise to further enhance the precision and speed of data processing and analysis, including automated visualization and anomaly detection.
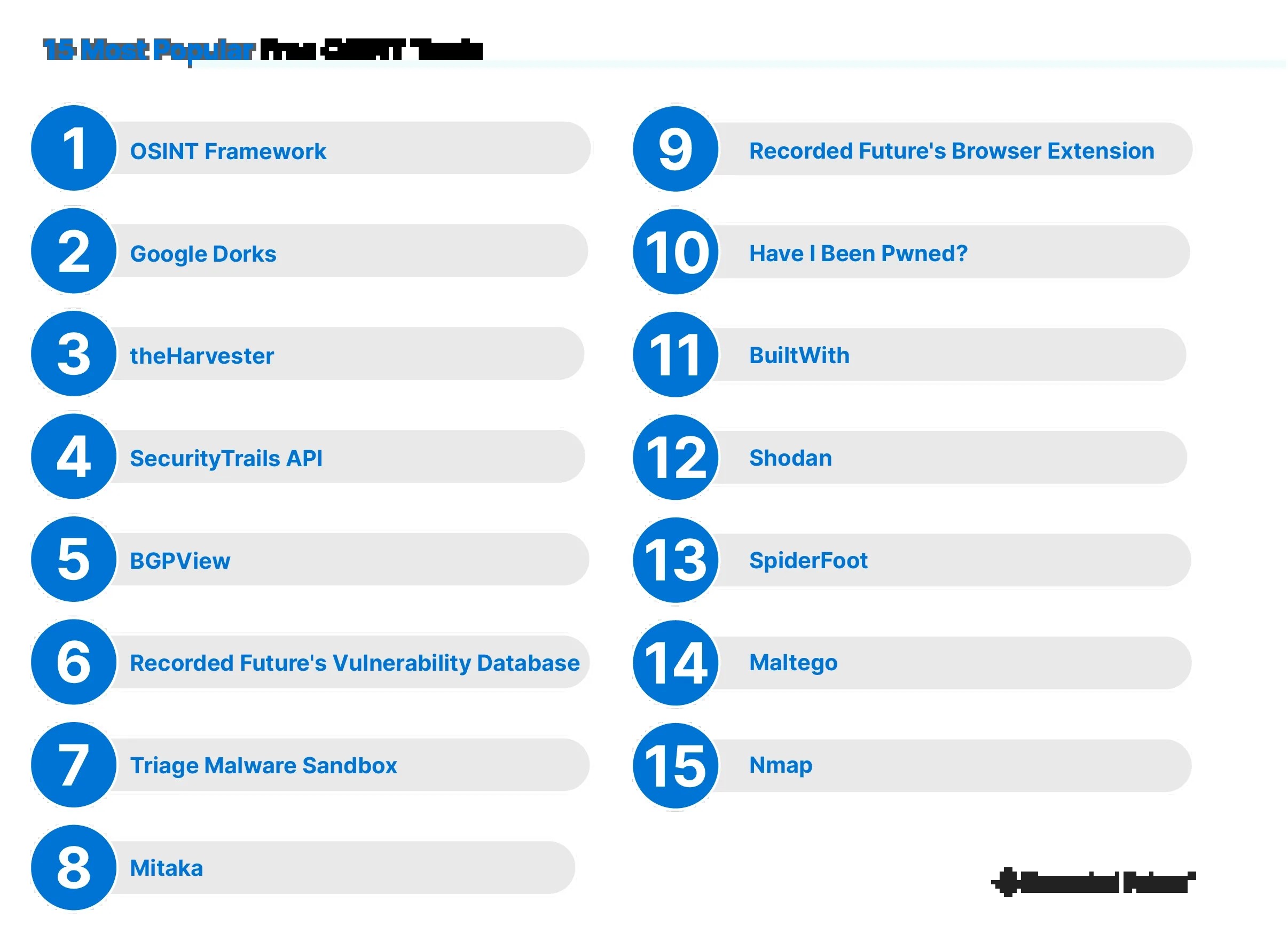
Visual representation of top OSINT tools for intelligence gathering, highlighting the importance of diverse tools in modern OSINT practices.
Top Network Scanning Tools with Graphs and Pictures
While the term “network scanning tool” might not always be explicitly categorized as OSINT, the information they gather is often publicly accessible and vital for open source intelligence gathering. Several tools offer graphical representations of network scans, enhancing their utility for OSINT professionals. Here are some prominent examples, including a focus on tools that provide visual outputs:
1. Nmap with Zenmap GUI: Nmap (Network Mapper) is a powerful and versatile network scanner. While command-line driven, Nmap’s official GUI, Zenmap, provides a graphical interface to visualize scan results. Zenmap allows users to see network topology, host details, and scan results presented in graphs and charts, making it easier to interpret complex network data. Nmap itself is mentioned in the original article as a key OSINT related tool.
Key Features of Nmap & Zenmap for Visual Network Scanning:
- Service and Version Detection: Nmap identifies services running on open ports, and Zenmap can visualize these services and their versions across the network.
- Operating System Detection: Nmap can fingerprint operating systems, and Zenmap can display OS distribution in a graphical format.
- Topology Visualization: Zenmap can create network topology maps, showing connections between hosts, which is invaluable for understanding network structure.
- Customizable Scans: Both Nmap and Zenmap offer extensive options for customizing scans, allowing users to target specific ports, protocols, and scan types, visualized in real-time or post-scan reports.
2. OpenVAS (Open Vulnerability Assessment System): While primarily a vulnerability scanner, OpenVAS includes network scanning capabilities and features a web-based GUI that provides visualized scan results. OpenVAS presents vulnerability data and network scan information in dashboards and reports with graphs and charts, making it easier to understand vulnerability distributions and network security posture.
Visual Features in OpenVAS:
- Vulnerability Dashboards: OpenVAS dashboards display vulnerability statistics and trends in graphical formats, offering a quick overview of network security.
- Report Generation: OpenVAS generates reports that include charts and graphs illustrating vulnerability severity, distribution, and remediation progress.
- Network Host Views: OpenVAS can visually represent network hosts and their associated vulnerabilities, aiding in targeted remediation efforts.
3. Nessus Professional: Nessus is another leading vulnerability scanner that also incorporates network scanning. Nessus Professional features a user-friendly GUI that provides comprehensive visualization of scan results. It offers customizable dashboards and reports with graphs and charts to represent vulnerabilities, compliance issues, and network configurations.
Visualization Capabilities of Nessus:
- Interactive Dashboards: Nessus dashboards provide real-time visualizations of scan data, allowing users to drill down into specific vulnerabilities and hosts.
- Customizable Reports: Nessus reports can be tailored to include specific graphs and charts that highlight key findings for different audiences.
- Vulnerability Trend Analysis: Nessus can visualize vulnerability trends over time, helping organizations track their security posture improvements or deteriorations.
4. Maltego: Maltego (mentioned in the original article) is a powerful OSINT tool focused on link analysis and data visualization. While not strictly a network scanner in itself, Maltego can integrate with network scanning tools or import network scan data to visually represent relationships between network entities. Maltego’s graphical interface excels at illustrating connections between domains, IPs, organizations, and individuals, which can be derived from network scanning activities.
Maltego’s Visual Strengths for Network Data:
- Entity Graph Visualization: Maltego uses graphs to visually represent entities (like domains, IPs) and their relationships, which can be populated with network scan data.
- Transformations for Network Data: Maltego offers “transforms” that can fetch network-related information and visualize it within the graph, extending its visual capabilities to network scanning data.
- Customizable Visual Layouts: Maltego allows users to customize graph layouts and visual elements, making it easier to present network data in a clear and impactful way.
5. SpiderFoot: SpiderFoot (also mentioned in the original article) is an automated OSINT tool that can perform network footprinting and surface network-related information. While SpiderFoot’s primary output is often text-based reports, it can be used in conjunction with visualization tools or custom scripts to generate graphs and pictures from the collected network data.
Leveraging SpiderFoot for Visualizations:
- Data Export: SpiderFoot allows exporting scan data in various formats (e.g., JSON, CSV), which can be imported into visualization tools like Gephi or Cytoscape for graph creation.
- Custom Scripting: Users can write custom scripts to process SpiderFoot’s output and generate visualizations tailored to their specific needs.
- Integration with Visualization Libraries: SpiderFoot could be programmatically integrated with Python libraries like Matplotlib or Seaborn to create graphs and charts directly from scan results.
Visual examples of OSINT tools in action, demonstrating the practical applications of open-source intelligence gathering in real-world scenarios.
Benefits of Using Network Scanning Tools with Graphs and Pictures
Choosing a network scanning tool that provides graphs and pictures offers significant advantages for OSINT professionals:
- Improved Data Comprehension: Visualizations make it easier to grasp complex network data quickly, reducing cognitive load and speeding up analysis.
- Enhanced Pattern Recognition: Graphs and pictures can reveal patterns, anomalies, and relationships in network data that might be missed in text-based reports.
- Effective Communication: Visual reports are more accessible and understandable for non-technical stakeholders, facilitating better communication of findings and recommendations.
- Faster Decision-Making: By providing immediate insights, visual network scanning tools enable faster and more informed decision-making in security assessments and incident response.
- Streamlined Reporting: Tools with built-in visualization features simplify the process of creating comprehensive and visually appealing reports.
Integrating Visual Network Scanning into Your OSINT Workflow
To effectively utilize network scanning tools with graphs and pictures in your OSINT workflow:
- Define Your Objectives: Clearly outline what you want to achieve with network scanning (e.g., vulnerability assessment, network mapping, threat hunting).
- Choose the Right Tool: Select a tool that aligns with your objectives and offers the desired visualization capabilities (consider Nmap/Zenmap, OpenVAS, Nessus, Maltego).
- Customize Your Scans: Configure scans to target specific networks, ports, and protocols relevant to your intelligence gathering efforts.
- Analyze Visual Output: Leverage the graphs and pictures generated by the tool to identify key network characteristics, vulnerabilities, and potential threats.
- Integrate with Other OSINT Data: Combine network scan data with information from other OSINT sources (social media, public records, etc.) for a holistic intelligence picture.
- Generate Visual Reports: Create reports with graphs and pictures to document your findings and communicate them effectively.
- Stay Updated: Keep your network scanning tools updated to benefit from the latest features and vulnerability signatures.
Legal and Ethical Considerations in Network Scanning for OSINT
When using network scanning tools for OSINT, it’s crucial to adhere to legal and ethical guidelines. Network scanning, even of publicly accessible systems, can raise legal and privacy concerns. Key considerations include:
- Compliance with Laws: Understand and comply with relevant laws and regulations, such as GDPR in Europe, which governs data processing and privacy.
- Ethical Data Collection: Focus on collecting publicly available information ethically and transparently.
- Terms of Service: Adhere to the terms of service of websites and online platforms when conducting network scans.
- Avoid Unauthorized Access: Ensure your scanning activities do not involve unauthorized access to private or sensitive data.
- Transparency: Be transparent about your OSINT activities when appropriate and avoid deceptive practices.
Wrapping Up: Visualizing Network Intelligence
The best network scanning tool that provides graphs and pictures significantly enhances the effectiveness of OSINT practices. By leveraging visual representations of network data, analysts can gain deeper insights, communicate findings more effectively, and make faster, more informed decisions. As network complexity grows, the ability to visualize network intelligence will become increasingly crucial for successful OSINT operations. Mastering these visual tools and techniques is essential for any OSINT professional seeking to navigate the intricate landscape of modern cybersecurity and digital intelligence.
To further enhance your OSINT capabilities, consider exploring advanced threat intelligence platforms. Schedule a demo today to discover how integrating OSINT with threat intelligence can provide a comprehensive security advantage.