Wireless networks are essential for modern enterprises, but they also introduce significant security vulnerabilities. The ease of access to hacking tools and the proliferation of wireless devices have made wireless networks prime targets for malicious actors. Understanding and mitigating these threats is crucial for maintaining a secure and reliable network environment. Cisco Meraki’s Air Marshal offers a robust Wireless Intrusion Prevention System (WIPS) that provides comprehensive protection against various wireless threats, including the ability to Block Network Scanning Tools Cisco, ensuring your airspace remains secure.
Understanding Wireless Security Threats in Enterprise Networks
The reliance on WiFi for critical business operations, from point-of-sale systems to corporate communications, has created a vast landscape of sensitive data transmitted wirelessly. This wealth of information attracts cyber threats, and the availability of open-source hacking tools makes it easier than ever to compromise wireless networks. Attackers can impersonate legitimate devices and access points (APs), intercepting sensitive data and disrupting network operations.
Common Wireless Threats Exploited by Network Scanning Tools
Several common threats can be exploited using readily available network scanning tools, highlighting the need for robust security measures to block network scanning tools Cisco and similar threats might employ:
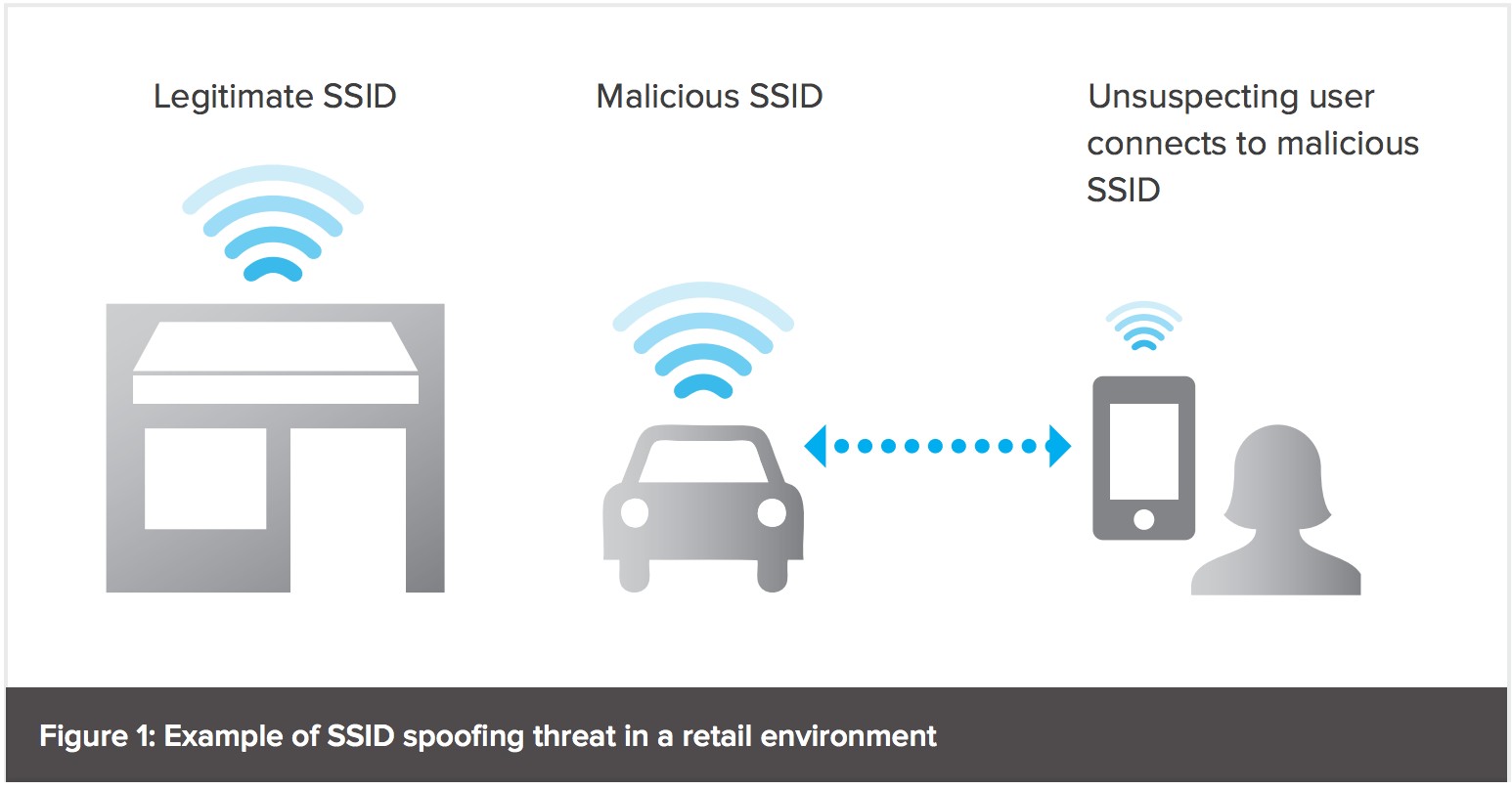
1. Network Impersonation (SSID Spoofing):
Attackers can easily set up a rogue access point mimicking a legitimate SSID. Unsuspecting clients connect to this fake network, unknowingly exposing their data. This technique, known as SSID spoofing, allows attackers to intercept communication and steal sensitive information.
Figure 1: SSID spoofing can compromise client data in retail and other environments.
2. Wired Network Compromise via Rogue APs:
A malicious actor or even an unaware employee can plug a consumer-grade access point into the wired network. This creates a backdoor, bypassing security measures and exposing the Local Area Network (LAN) to external threats. Such rogue APs become entry points for hackers to access the wired infrastructure.
Figure 2: Rogue APs connected to the wired network can create significant security breaches.
The Role of WIPS and Network Scanning Blockers
To effectively counter these threats and block network scanning tools Cisco, a robust Wireless Intrusion Prevention System (WIPS) is essential. A WIPS should possess powerful wireless intrusion scanning capabilities to detect and classify various threats, including rogue access points and wireless hacking attempts. Furthermore, it should offer automated containment policies for proactive threat mitigation. Upon threat detection, the WIPS platform should initiate policies like intelligent auto-disablement of rogue APs and generate alerts based on threat severity.
Cisco Meraki’s Air Marshal mode is designed to meet these demands. It empowers network administrators to build a secure network architecture with an industry-leading WIPS platform, offering comprehensive airspace protection against wireless attacks.
Deep Dive into Wireless Threats
Understanding the wireless environment is the first step in implementing effective security measures. The accessibility of affordable 802.11 equipment and open-source hacking tools facilitates various threats. Leading WLAN providers like Cisco incorporate built-in WIPS features to detect and remediate these threats, ensuring a secure wireless environment and effectively block network scanning tools Cisco and others may utilize.
Threat Classifications by Cisco Air Marshal
Visibility and classification of wireless threats are critical for securing the network. Cisco Meraki Air Marshal automatically categorizes threats, offering enhanced visibility and network protection, enabling administrators to effectively block network scanning tools Cisco and address other vulnerabilities.
1. Rogue SSIDs:
-
Rogue SSID seen on LAN: These are SSIDs broadcast by unauthorized access points detected on the wired LAN. Their presence can signal a wired network breach.
Note: Air Marshal on Meraki MRs with a scanning radio might not contain Rogue and Other SSIDs on DFS channels due to regulatory scanning time requirements. However, containment is possible on DFS channels if the client-serving radio operates on the same DFS channel as the rogue SSID.
2. Other SSIDs:
- Interfering SSIDs: These wireless networks cause RF interference and can attract clients intended for your network.
- Ad-Hoc SSIDs: Modern devices can rebroadcast SSIDs, acting as wireless bridges. These ad-hoc networks can become gateways for wireless hackers, bypassing security measures and requiring tools to block network scanning tools Cisco and similar threats might leverage through these pathways.
3. Spoofs:
- AP Spoofs: These are access points impersonating your legitimate APs’ SSID and MAC address. AP spoofing is a serious threat indicating a deliberate attempt to mimic your network and should be addressed with high priority.
4. Malicious Broadcasts:
- Denial of Service (DoS) Attacks: DoS attacks aim to disrupt client connections to legitimate APs by overwhelming them with broadcast messages. These attacks can originate from malicious clients, APs, or even other WIPS systems misidentifying your network as a threat.
5. Packet Floods:
- Excessive Packet Transmission: This involves clients or APs sending an unusually high volume of packets. Air Marshal monitors and classifies packets (beacon, authentication, association frames) and flags packet floods, indicating potential malicious activity or misconfigurations that could be exploited by network scanning activities, making it crucial to block network scanning tools Cisco and identify such anomalies.
Containment Strategies with Cisco Air Marshal
Cisco Meraki access points utilize Air Marshal technology to mitigate wireless threats. Air Marshal’s containment capabilities are vital for neutralizing rogue access points that pose a risk to network security.
Overview of Air Marshal Containment
Once rogue access points are identified, Air Marshal can contain them, preventing client connections and disconnecting currently associated clients.
Note: 6 GHz containment is not feasible due to protected management frames in 6 GHz.
Containment is achieved by Meraki APs sending deauthentication packets with the spoofed MAC address of the rogue AP. These packets force clients off the rogue network and prevent new connections.
Figure 3: Air Marshal containment effectively disconnects clients from rogue SSIDs.
Rogue AP Detection Beyond Regulatory Domains
Enhanced rogue AP detection in Air Marshal now extends beyond regulatory domains for Wi-Fi 6 and newer APs (excluding MR28 and MR78 running MR31.x+). Previously, APs only monitored within their regulatory domains, posing a risk in global enterprises where malicious APs could operate on unsupported channels. With MR31.1+, Air Marshal detects rogue APs even on out-of-regulatory domain channels, improving threat visibility and the ability to block network scanning tools Cisco might deploy through these avenues.
Note: Out-of-regulatory domain detection is for alerts and non-containment only. Containment remains limited to regulatory domain channels. Contact Meraki support to enable this feature.
Configuring Cisco Meraki Air Marshal WIDS/WIPS
Meraki APs offer flexible Air Marshal deployment options:
- Dual-radio APs: These APs perform opportunistic wireless scans while serving clients or can be set to dedicated Air Marshal mode. Scheduled mandatory scans can also be configured.
- Dedicated Air Marshal Mode: Dual-radio APs can be configured as dedicated scanners, ceasing client service to focus on scanning both 2.4GHz and 5GHz bands.
- Tri-radio APs: Many Meraki APs feature a third, dedicated scanning radio for continuous Air Marshal scanning without configuration changes, providing constant vigilance and the ability to block network scanning tools Cisco in real-time.
Hybrid vs. Dedicated Scanners
While dual-radio APs offer opportunistic scanning, dedicated scanners are recommended for security-conscious environments. Dedicated scanning ensures real-time security alerts and protection without compromising client-serving performance. Meraki recommends dedicated scanning radios for optimal performance and security.
Figure 4: Meraki Air Marshal configuration interface.
Default LAN Containment Options
Administrators can define default containment behavior for rogue SSIDs:
- Allow devices to connect to rogue SSIDs by default: This provides flexibility but less security. Granular control can be implemented using SSID block lists.
- Block clients from connecting to rogue SSIDs by default: This offers maximum security by automatically containing connections to non-Meraki APs on the wired LAN.
Figure 5: Configuring default rogue SSID containment policies.
SSID Block List, Allow List, and Alerting
-
SSID Block List: Allows defining rules to block specific SSIDs or BSSIDs, even if default containment is disabled. Wildcards are supported for flexible matching. Alerts are generated for blocked SSIDs. Exercise caution when configuring block lists to avoid unintended containment of neighboring networks and potential self-interference.
Figure A: SSID block list policies for enhanced security.
-
SSID Allow List: When default containment is enabled, allow lists specify SSIDs or BSSIDs that should not be contained or generate alerts.
Figure B: SSID allow list exceptions to default containment.
-
SSID Alerting: Rules can be set to trigger alerts (email and syslog) when specific SSIDs are detected, enhancing monitoring capabilities and helping to proactively block network scanning tools Cisco and related threats.
Figure C: SSID alert policy configuration.
Manually Applying Security Policies
Administrators can manually apply security policies to detected SSIDs directly from the Air Marshal dashboard:
- Navigate to Wireless > Monitor > Air Marshal.
- Select SSIDs under Rogue SSIDs or Other SSIDs tabs.
- Choose Edit and select Allow list, Contain, Alert, or Uncontain.
- Apply policy by SSID or BSSID.
Figure D: Selecting an SSID for manual policy application.
Figure E: Choosing a policy action for selected SSIDs.
Containment Types and Status
Air Marshal provides different containment statuses:
- Uncontained: Rogue or other networks not currently contained.
- Contained: Rogue networks actively being contained by Meraki APs.
- Partially Contained: Rogue networks that cannot be fully contained due to channel differences with some rogue APs. Dedicated scanning APs improve partial containment scenarios.
- Allow Listed: Networks exempted from containment and alerts.
- Uncontained Other: Networks detected but not identified as immediate threats.
Rogue SSID Detection Logic
Air Marshal classifies SSIDs as ‘Rogue’ or ‘Other’ based on Beacon Frame detection. Rogue SSID identification involves comparing the MAC address of local devices with the BSSID of the broadcasted SSID.
Hidden SSIDs: These are SSIDs without names in beacons and probe responses. They are generally low-risk but can be managed with allow/block/alert rules by selecting the “Hidden” row and applying rules to the Broadcast MAC.
Detailed rogue SSID information, including RSSI, detection time, channels, BSSID, manufacturer, and rogue classification reason, is available by selecting an SSID row.
Rogue SSID detection criteria involve comparing wired MAC addresses with broadcasted BSSID MAC addresses, focusing on the 3rd and 4th bytes and a small bit difference in the remaining bytes.
Air Marshal detects rogues across all VLANs if the Meraki AP connects to a trunk port with all VLANs allowed. Rogue SSID detection empowers administrators to proactively block network scanning tools Cisco and prevent unauthorized network access.
Threat Remediation with Air Marshal: Monitoring, Alerting, and Containment
Air Marshal offers comprehensive threat remediation mechanisms:
1. Monitoring and Alerting:
-
Rogue Access Point Monitoring: Dedicated scanning radios in 802.11ac Meraki APs scan all channels, compiling a list of rogue APs. Wired LAN traffic inspection further identifies rogue APs on the wired network. Email and syslog alerts are triggered based on SSID block list and alert rules, enabling administrators to effectively block network scanning tools Cisco and respond to threats promptly.
Email alerts are configured under Network-wide > Configure > Alerts. Syslog alerting is set up under Network-wide > Configure > General. API access for scan results is available via the
get-network-wireless-air-marshalcall.
2. Remediation Mechanisms:
-
Containment: Air Marshal automatically contains rogue APs based on default settings or configured rules. Containment involves spoofing rogue APs to render them ineffective. Air Marshal uses sophisticated two-way spoofing, targeting both rogue APs and clients attempting to connect, ensuring robust rogue AP shutdown and helping to block network scanning tools Cisco might leverage through compromised connections.
Packet types used during containment:
- 802.11 Broadcast deauthorizations (Source: Rogue AP, Destination: Broadcast).
- 802.11 Deauthorization messages (Source: Rogue AP, Destination: Client MAC).
- 802.11 Deauthorization and disassociate messages (Source: Client, Destination: Rogue AP).
PCI Compliance and WIPS Requirements
PCI DSS compliance mandates specific wireless security measures, aligning with WIPS capabilities:
- Section 9.1.3 Physical Security: Restrict physical access to wireless devices.
- Section 10.5.4 Wireless Logs: Centralized WIPS logging for one year.
- Section 11.1 Quarterly Wireless Scan: Quarterly scans of cardholder data environments (CDEs). WIPS is recommended for large organizations.
- Section 11.4 Monitor Alerts: Automatic WIPS alerts for rogue devices and unauthorized connections.
- Section 12.9 Eliminate Threats: Incident response plan and automatic containment mechanisms to block network scanning tools Cisco and other threats.
Creating a WIPS Response Plan
A robust WIPS response plan involves proactive and reactive monitoring:
- WIPS Plan Creation:
- Configure scanning intervals or dedicated Air Marshal APs.
- Set auto-containment policies for rogue SSIDs.
- Configure WIPS alerts.
- Proactive Air Marshal Monitoring:
- Regularly review the Air Marshal page.
- Manage allow/block lists and alert rules.
- Utilize the API for data warehousing and audits.
- Contain potential rogue threats.
- Reactive Air Marshal Alert Monitoring:
- Respond to alerts by initiating containment and locating/removing rogue devices.
Physical Deployment of Air Marshal APs
Dedicated Air Marshal APs deploy similarly to client-serving APs. Air Marshal APs have a larger coverage radius for threat detection and containment (approximately twice the client coverage radius), requiring fewer dedicated APs for full WIPS coverage (approximately 1:4 ratio of Air Marshal to client-serving APs).
Conclusion: Fortifying Wireless Security with Cisco Air Marshal
Understanding wireless security threats and implementing a comprehensive WIPS response plan is crucial for protecting enterprise networks. Cisco Meraki Air Marshal provides an intuitive and powerful WIPS platform with real-time detection, remediation, and alerting, effectively helping to block network scanning tools Cisco and mitigate various wireless threats. With flexible deployment options and a user-friendly interface, Meraki Air Marshal empowers network administrators to establish robust wireless security policies and create an airtight network environment, ensuring enterprise-grade WLAN security.