In today’s digital landscape, ensuring robust network security is not just an option, but a necessity for businesses of all sizes. From safeguarding sensitive client data in finance and healthcare to protecting critical infrastructure in government and education, the stakes are incredibly high. While large corporations with extensive resources understand the paramount importance of cybersecurity, smaller businesses often struggle to allocate sufficient IT time and resources to this critical area. This is where automated vulnerability management (VM) tools become indispensable, offering a streamlined and efficient approach to identifying and mitigating security risks.
This article delves into the world of vulnerability scanners, exploring both paid and free options available in the market. We’ll examine the capabilities of leading tools and discuss the fundamental aspects of network vulnerability management that every IT professional should grasp to maximize the effectiveness of their chosen scanning solution. While tools like Network Configuration Manager stand out for comprehensive network configuration and remediation, and Wireshark remains a top free choice for network analysis, understanding the core principles of vulnerability management is key to effective security posture.
We will explore the essential elements of vulnerability management, common causes of security weaknesses, methods for evaluating vulnerability risks, and various VM techniques. We will also differentiate between various types of vulnerability scanners and delve into their functionalities. Furthermore, we will analyze whether specific tools, like Retina security scanning tools, can scan databases for vulnerabilities, addressing a critical concern for organizations managing sensitive data.
Vulnerability Management Basics
Common Security Vulnerability Causes
Identify Vulnerability Risks
Vulnerability Management Techniques
Types of Vulnerability Scanners
What Do Vulnerability Scanners Do?
Best Paid Tools
Best Free Tools
Vulnerability Monitoring Issues
The Basics of Vulnerability Management
Is your IT infrastructure truly secure? Superficial indicators like network connectivity and user file access can be misleading. The reality is that every network harbors potential security loopholes that malicious actors or malware could exploit. Vulnerability management is the continuous process of identifying, classifying, remediating, and mitigating these security weaknesses. It’s not a one-time fix but an ongoing commitment, especially considering the dynamic nature of networks and the ever-evolving landscape of cyber threats.
Thinking that antivirus software alone is sufficient for network security is a common misconception. Antivirus is reactive, primarily focused on damage control after an intrusion. A proactive approach, centered on preventative measures, is far more effective in minimizing security risks. Vulnerability scanning tools are crucial components of this proactive strategy.
Vulnerability scanning software empowers IT security administrators by automating several critical tasks:
- Identifying Vulnerabilities: The primary function is to pinpoint security weaknesses across the entire network infrastructure, encompassing workstations, servers, firewalls, and other network devices. Automated tools are essential for comprehensive coverage, especially for businesses of any scale. Manual vulnerability management, even with robust IT resources, becomes increasingly impractical and inefficient as network complexity grows.
- Evaluating Risks: Not all vulnerabilities pose the same level of threat. Scanning tools analyze and categorize identified vulnerabilities based on severity and potential impact. This risk assessment allows administrators to prioritize remediation efforts, focusing on the most critical issues first.
- Addressing Problems: Once high-priority vulnerabilities are identified, the task of remediation can be complex. The right vulnerability management tool can facilitate and even automate the process of patching systems, reconfiguring devices, and implementing necessary security controls.
- Reporting on Security Gaps: Demonstrating compliance with industry regulations and internal security policies requires comprehensive reporting. Vulnerability scanning software can generate detailed reports on network security status, vulnerability trends, and remediation progress, aiding in compliance and audit processes.
What Causes Security Vulnerabilities?
The avenues through which a network can be compromised are vast and constantly evolving. However, certain common security vulnerabilities consistently appear as major points of entry for malicious actors. While no single scanning tool can address every conceivable threat, a robust vulnerability management strategy should prioritize mitigating these common risks.
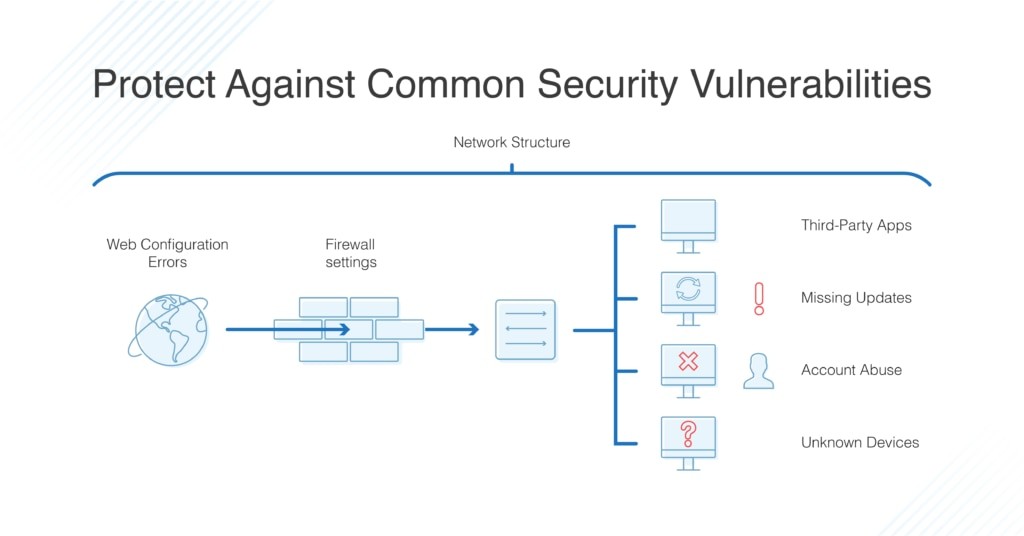
- Network Structure Flaws: Many business networks suffer from overly permissive architectures, often described as “open.” In such setups, once an attacker gains initial access, they can potentially navigate freely across the entire network. Implementing network segmentation and enforcing strict user group privilege management are critical to preventing lateral movement and containing breaches.
- Unknown Devices: Unidentified and unmanaged devices connected to the network represent significant blind spots. Ensuring that only authorized and properly secured devices have network access is crucial. Network access control (NAC) and device discovery tools can help identify and manage all devices on the network.
- Account Abuse: The threat from within should not be underestimated. Insider threats, whether intentional or accidental, can lead to data leaks and security breaches. Misconfigured programs, default credentials, orphaned user accounts, and incorrect privilege assignments all contribute to this risk. Robust identity and access management (IAM) policies and regular security audits are vital.
- Web Configuration Errors: Web application security is paramount for organizations with an online presence. Common web vulnerabilities include Distributed Denial-of-Service (DDoS) attack susceptibility, HTTP misconfigurations, expired SSL/TLS certificates, and insecure coding practices. Web application firewalls (WAFs) and regular web security scans are essential for mitigating these risks.
- Security Feature Misconfigurations: Even well-intentioned security measures can become vulnerabilities if improperly configured. Firewall and operating system misconfigurations are common examples. Regular security audits and configuration management tools can help ensure security features are correctly implemented and maintained.
- Third-Party Applications: Third-party applications often introduce unforeseen security risks, either due to inherent vulnerabilities in their code or insecure implementation practices. Limiting the use of unnecessary third-party applications, rigorously vetting software before deployment, and monitoring for suspicious downloads are crucial steps. Outdated or end-of-life software also poses a significant risk and should be phased out.
- Missing Updates and Patches: One of the most prevalent causes of security breaches is the failure to apply timely software and firmware updates and patches. Hackers actively exploit known vulnerabilities in outdated software. Implementing a robust patch management system is a fundamental security practice.
Evaluating Risks of Vulnerabilities
Vulnerability scanners often generate extensive lists of potential security weaknesses. However, IT teams rarely possess the resources to address every identified vulnerability immediately. Effective vulnerability management requires prioritization. Many automated tools offer risk scoring systems, ranking vulnerabilities based on factors like severity, exploitability, and potential impact.
However, IT administrators should also be equipped to independently assess risks and understand the rationale behind automated threat assessments. This empowers them to make informed decisions and take targeted action. When evaluating a vulnerability, consider:
- Potential Impact: If exploited, what would be the consequences? Would sensitive data be compromised? Would the breach be localized or widespread across the network?
- Likelihood of Exploitation: How likely is it that a malicious actor would exploit this specific vulnerability? Consider factors like exploit availability, attacker motivation, and the vulnerability’s exposure. Internal vulnerabilities may be exploited by employees, while externally facing vulnerabilities are exposed to a broader range of threats.
- False Positives: Always verify vulnerability findings to rule out false positives. Investigating non-existent issues wastes valuable resources.
The primary goal of risk evaluation is to prioritize remediation efforts, focusing on vulnerabilities that pose the most significant and immediate threats. Automated tools can significantly assist in this process, but human oversight and informed decision-making remain essential for effective vulnerability management.
Top Vulnerability Management Techniques
Vulnerability scanning is a cornerstone of proactive security, but it’s most effective when integrated with other complementary vulnerability management techniques:
- Penetration Testing: Penetration testing, or “pen testing,” involves ethically simulating cyberattacks to identify security weaknesses. By attempting to breach their own systems, organizations can uncover vulnerabilities that automated scanners might miss. Pen testing can be highly effective but is often time-consuming and costly, making it more suitable for larger organizations with dedicated security teams.
- Breach and Attack Simulation (BAS): BAS takes penetration testing a step further by automating and continuously running simulated attacks. This provides ongoing validation of security controls and measures their effectiveness over time. BAS tools are relatively new to the market and often managed by external vendors, requiring careful vendor selection and trust. Accuracy in BAS testing may involve exposing sensitive data or impacting system performance.
- Antivirus Monitoring: Antivirus software plays a crucial role in detecting and removing malware within the network. However, it’s primarily a reactive defense mechanism. While essential, antivirus is less focused on proactively identifying and mitigating underlying network vulnerabilities compared to vulnerability scanners. Antivirus targets specific threats like ransomware, spyware, and Trojans, rather than broad security gaps.
- Web Application Scanning: Web application scanning tools specialize in identifying vulnerabilities within web applications. They can simulate attacks or analyze application code to detect common web vulnerabilities like cross-site scripting (XSS), SQL injection, path traversal, and insecure configurations. These tools operate on similar principles to network vulnerability scanners but are tailored for web application security.
- Configuration Management: Misconfigurations and missing patches are frequently cited as major contributors to security breaches, often exceeding zero-day exploits in real-world impact. Many vulnerabilities persist for extended periods due to unaddressed misconfigurations and delayed patching. Configuration management tools help ensure consistent and secure configurations across systems, even as networks evolve. Regular configuration audits and automated remediation are essential for maintaining a secure baseline and ensuring compliance.
Types of Vulnerability Scanning and Detection
Developing a comprehensive vulnerability scanning strategy involves understanding the different types of scans and their respective strengths. Choosing the right scan types and frequency is crucial for effective security management. Key distinctions include the scan’s location (internal vs. external) and scope (comprehensive vs. limited).
-
Internal vs. External Scanning:
- Internal Network Scan: Performed from within the organization’s intranet, internal scans assess vulnerabilities accessible to users inside the network. This helps identify weaknesses that could be exploited by employees or compromised internal accounts. Scanning as a logged-in user provides insights into privilege-based vulnerabilities.
- External Network Scan: Conducted from the internet, external scans simulate attacks originating from outside the network perimeter. This helps identify vulnerabilities exposed to the external world, reflecting how attackers might attempt to penetrate the network from the internet. Scanning as an unauthenticated intruder reveals externally facing attack surfaces.
-
Comprehensive vs. Limited Scanning:
- Comprehensive Scan: Aims to scan virtually every device and system on the network, including servers, desktops, VMs, laptops, mobile devices, printers, containers, firewalls, and switches. This involves scanning operating systems, installed software, open ports, and user accounts, and detecting unauthorized devices. Comprehensive scans strive for complete vulnerability coverage, leaving no stone unturned.
- Limited Scan: Focuses on specific devices, systems, or applications, providing a more targeted security assessment. Limited scans can be useful for focusing on high-risk areas or for more frequent, less resource-intensive checks.
While comprehensive scans offer greater coverage, they can consume significant network bandwidth and may not be feasible to run frequently. Limited scans provide a balance between resource consumption and targeted security insights. A combination of scan types and frequencies, tailored to the organization’s specific needs and resources, is often the most effective approach.
What Do Vulnerability Scanning and Detection Tools Do?
Given the ever-growing threat landscape targeting networks and web applications, vulnerability detection is a critical function for IT security. Vulnerability scanning tools and related software are designed to automate this process, identifying threats and managing security across devices and applications. When selecting a network vulnerability scanner, consider tools that offer the following core functionalities:
- Weakness Detection: The primary task is to identify security weaknesses across the network. Some tools actively attempt to exploit vulnerabilities during the scan, simulating attack scenarios. This proactive approach helps validate security posture. Other tools focus on detecting missing patches or configuration errors.
- Vulnerability Classification: Once vulnerabilities are detected, they need to be classified and prioritized. Tools often categorize vulnerabilities based on severity, exploitability, and potential impact. Threat prioritization typically considers factors like vulnerability age and calculated risk levels. Many scanners leverage vulnerability databases like the National Vulnerability Database and Common Vulnerabilities and Exposures to enrich vulnerability information and assess known risks.
- Countermeasure Implementation: Not all vulnerability tools simply identify issues; some offer remediation capabilities. While some tools are purely monitoring-focused, others provide automated or guided remediation features. These tools may assist in patching systems, reconfiguring devices, and applying security controls, potentially automating responses across numerous devices simultaneously, saving significant administrative effort.
10 Best Paid Tools for Vulnerability Scanning and Detection
For organizations seeking robust and comprehensive vulnerability management solutions, paid tools offer advanced features, automation, and support. Here are ten of the best paid vulnerability scanning and detection tools available:
If you are seeking a proactive solution to prevent security breaches, SolarWinds® Network Configuration Manager (NCM) is highly recommended. While not strictly a traditional vulnerability scanner, NCM excels at automatically detecting configuration discrepancies across multi-vendor network devices and efficiently deploying firmware updates to a large number of devices.
NCM simplifies the management of device settings known to introduce vulnerabilities. It even allows users to create custom remediation scripts to maintain device compliance. Given that configuration errors and missing patches are major sources of security breaches, NCM provides a practical and actionable approach to preventing attacks, making it an integral component of a comprehensive vulnerability management strategy.
NCM offers core vulnerability scanner functionalities, integrating with the National Vulnerability Database and the Common Vulnerabilities and Exposures database to prioritize Cisco firmware vulnerabilities and other critical issues. It also enhances administrative efficiency through automated firewall management, insights into device lifecycles, and robust reporting features for effective vulnerability management. NCM provides a full network inventory, tracks configuration changes, monitors compliance status, and generates reports to aid in security planning.
A 30-day fully functional free trial of NCM is available for evaluation. Considering its comprehensive capabilities, NCM offers excellent value. Furthermore, seamless integration with other SolarWinds products allows for scalability and expansion of IT management capabilities.
ManageEngine Vulnerability Manager Plus provides valuable vulnerability assessment capabilities, scanning devices, Windows systems, and select third-party applications. It offers immediate vulnerability ranking based on age and severity, employing an anomaly-based detection approach in addition to database correlation.
This tool delivers a broad spectrum of features, including antivirus management, identification of risky software and suspicious ports, and detection of configuration issues. ManageEngine also incorporates management tools for configuration deployment and patch management, along with zero-day vulnerability detection and pre-built mitigation scripts. While feature-rich, ManageEngine remains user-friendly, though potentially complex for very small environments. A free version is available for up to 25 computers.
Paessler PRTG offers comprehensive infrastructure monitoring, encompassing networks, applications, servers, and more. It tracks device status changes and alerts administrators to unusual activity that may indicate intrusions. PRTG utilizes packet sniffing to analyze SNMP trap data and port activity.
PRTG is primarily a monitoring tool and does not provide automated remediation features. It is free for up to 100 sensors and offers a 30-day free trial with unlimited sensors for full feature evaluation.
BeyondTrust Retina Network Security Scanner stands out for its broad scanning scope, encompassing networks, web services, containers, databases, virtual environments, and even IoT devices. Its built-in IoT support and auditing capabilities are not universally found in other scanners, making it an excellent choice for organizations managing diverse device ecosystems. Retina is designed to scan without impacting system performance or availability, utilizing vulnerability database comparisons rather than anomaly detection.
Regarding the critical question of “Can Retina Security Scanning Tools Scan Databases,” the answer is a definitive yes. BeyondTrust Retina is explicitly designed to scan databases for vulnerabilities. It can assess database configurations, identify missing patches, and detect known database-specific vulnerabilities, providing crucial security insights for database infrastructure.
Retina primarily focuses on monitoring and vulnerability assessment rather than automated remediation. While user-friendly and effective for security visibility, integration with the more comprehensive BeyondTrust Enterprise Vulnerability Management tool is needed for broader management capabilities.
Rapid7 Nexpose is an on-premises vulnerability management tool offering a solid foundation for security scanning. Nexpose employs a unique risk scoring system ranging from 1 to 1000, providing granular risk assessment based on vulnerability age and exploit kit availability. It also offers step-by-step guidance for aligning systems with common policy standards for compliance. While lacking full management features, Nexpose provides an open API for integration with other security tools.
Tripwire IP360 is an enterprise-grade vulnerability scanner designed for comprehensive network coverage, including on-premises, cloud, and container environments. It identifies devices and programs, including previously undetected agents, and automates vulnerability remediation prioritization based on impact, age, and exploitability. Similar to Nexpose, IP360 offers an open API for integration with broader management solutions, functioning primarily as a robust vulnerability scanner.
ImmuniWeb is an AI-driven platform offering multiple vulnerability scanning tools, including ImmuniWeb Continuous for penetration testing and ImmuniWeb Discovery for asset discovery and hackability scoring. It leverages machine learning for rapid risk detection and claims zero false positives, incorporating human pen testers for accuracy validation. While potentially costly and specialized for many organizations, ImmuniWeb may be suitable for DevOps teams requiring advanced AI-powered security assessments.
Netsparker specializes in web application security, utilizing proprietary Proof-Based-Scanning technology to minimize false positives, a critical advantage for large-scale deployments. Netsparker integrates with other management systems to automate vulnerability workflows. This tool emphasizes automation and accuracy, and is used by organizations like the U.S. Department of Homeland Security for web vulnerability assessment.
Acunetix is another dedicated website security scanner, excelling in detecting over 4,500 vulnerabilities in custom, commercial, and open-source web applications with a low false-positive rate. It provides line-of-code visibility, detailed reports for easier remediation, and customizable workflows within a user-friendly visual interface. Acunetix offers flexible and powerful web security scanning for website-centric teams.
Intruder is a cloud-based vulnerability scanner focused on streamlined risk detection. It checks configurations, identifies web application bugs, detects missing patches, and aims to reduce false positives. Intruder integrates with cloud providers for scanning external IPs and DNS hostnames, offering notifications via Slack, Jira, and email. While potentially simplistic for very in-depth analysis, its approachable pricing and ease of use make it attractive to many teams.
5 Best Free Vulnerability Scanners
For organizations with limited budgets or those seeking entry-level vulnerability scanning capabilities, free tools offer valuable functionalities. Here are five of the best free vulnerability scanners:
Wireshark is a renowned open-source network protocol analyzer that aids in vulnerability scanning tasks. It uses packet sniffing to analyze network traffic, enabling administrators to design effective countermeasures. Wireshark can detect suspicious traffic patterns, categorize attacks, and implement network protection rules. While powerful, Wireshark requires configuration expertise and is not as user-friendly as commercial tools.
Nmap is a classic open-source tool widely used for basic manual vulnerability management. It sends packets and analyzes responses to discover hosts and services on a network, including host discovery, port scanning, version detection, and OS detection. Scripting capabilities allow for advanced vulnerability detection. Nmap is command-line driven and lacks a graphical interface, making it suitable for experienced users comfortable with command-line operations.
Open Vulnerability Assessment System (OpenVAS) is a comprehensive open-source vulnerability management framework maintained by Greenbone Networks. It features a daily updated security feed with over 50,000 vulnerability tests. Designed for Linux environments, OpenVAS is suitable for targeted scans and penetration testing by experienced users. Installation and usage involve a significant learning curve, making it less accessible to general network administrators. Greenbone also offers a paid commercial product with enhanced support and features.
Qualys Community Edition is a free cloud-based service offering a limited version of the Qualys Cloud Platform, suitable for small organizations. It provides unlimited scanning for 16 internal assets, three external assets, and one URL, leveraging data from billions of annual vulnerability scans. Qualys Community Edition offers search functionality within scan results and flexible reporting, with a user-friendly interface.
Burp Suite Community Edition is a free version of a web vulnerability assessment tool, also available in Enterprise and Professional editions. It offers manual control over web vulnerability scanning, allowing users to manage requests and responses, annotate items, and apply custom modifications. Burp Suite provides granular control over rules, site map insights, statistical analysis charts, and community extensions, making it a powerful free option for web security testing.
Issues With Vulnerability Monitoring
While vulnerability scanning tools are invaluable for proactive security, it’s important to acknowledge potential issues associated with their use. Scanners interact with running code on target devices, which can sometimes lead to errors or system reboots. On some networks, scans can consume significant bandwidth and impact overall performance. Therefore, scheduling scans during off-peak hours is often recommended to minimize user impact. Some scanners are designed to mitigate performance issues, utilizing endpoint agents to push information to the platform, reducing the load during scheduled scans.
Adaptive scanning is another technique that can minimize performance impact. Adaptive scanners detect network changes, such as newly added devices, and immediately scan only those new systems. This incremental approach avoids lengthy, full network scans, optimizing resource utilization.
In conclusion, vulnerability scanning software is a vital component of a robust security strategy, providing a critical first step towards protecting networks and reducing manual vulnerability management burdens. Tools like Network Configuration Manager offer comprehensive solutions to streamline vulnerability detection and enhance overall network security posture.