Application Security Posture Management (ASPM) is a hot topic in cybersecurity, but its definition remains somewhat nebulous. While some consider it a sophisticated form of vulnerability management, others view it as a comprehensive code scanning solution. This article argues that a truly effective ASPM system functions as an all-in-one application security scanning tool, encompassing various code readers and scan tools انواع.
The Need for ASPM: Streamlining Application Security
DevSecOps is crucial for rapid product development while maintaining security and compliance. Protecting customer data and preserving consumer trust requires thorough application scanning for misconfigurations. Modern application security demands fast, in-pipeline scanning with actionable results that guide developers toward efficient remediation.
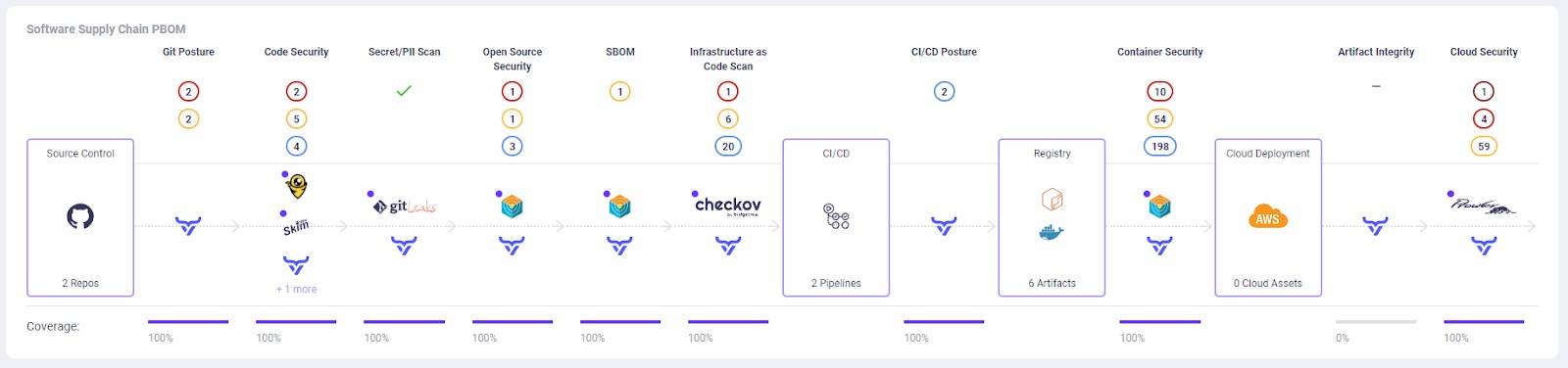
The proliferation of DevSecOps point solutions has created a complex landscape. Key scanning categories include:
- SDLC: Analyzing Git settings for vulnerabilities.
- SCA: Assessing open-source dependencies.
- SAST: Scanning code for exploitable vulnerabilities.
- IaC: Examining infrastructure-as-code deployments (e.g., Terraform, Kubernetes).
- Container Scanning: Inspecting Dockerfiles and runtime environments.
- Secret Scanning: Identifying exposed secrets.
- DAST: Analyzing running code for vulnerabilities.
- CSPM: Evaluating cloud environment security.
While excellent point solutions exist for each category, managing numerous tools, each generating thousands of findings, overwhelms security teams. This complexity led to the emergence of Application Security Orchestration and Correlation (ASOC) to manage these tools across the codebase. However, ASPM aims to address this challenge differently.
Beyond Gartner’s Definition: Consolidating Security Tools
ASOC aimed to correlate findings from various tools into a single dashboard. However, platforms like Snyk gained traction by offering multiple scanning capabilities (SCA, SAST, IaC, Container) within a single platform. This consolidated approach proved more valuable than managing separate tools and an orchestration layer.
Gartner defines ASPM as continuously managing application risk through the collection, analysis, and prioritization of security issues across the software lifecycle. However, this definition overlooks the crucial trend of consolidating scanning tools. ASPM, in its ideal form, should minimize the need for multiple tools by providing comprehensive scanning capabilities.
The Ideal ASPM: A Comprehensive Solution
A complete ASPM solution should offer:
- Code-to-Production Visibility: Tracing code from commit to deployment, identifying vulnerabilities and their remediation points within the codebase.
- Comprehensive Scanning: Covering all eight key scanning categories (SDLC, SCA, SAST, IaC, Container Scanning, Secret Scanning, DAST, CSPM) with best-in-class features.
- Flexible Workflow Automation: Providing customizable workflows alongside pre-defined templates for common scenarios, facilitating efficient vulnerability management.
- Third-Party Tool Integration: Enriching findings from external scanners with application context.
- Remediation Focus: Guiding developers with precise code changes to fix vulnerabilities effectively.
A concise definition of ASPM: Application Security Posture Management provides comprehensive vulnerability scanning and remediation capabilities across the SDLC, integrating results and automating workflows.
The Future of ASPM: Towards Unified Security Posture Management
The future of ASPM lies in its convergence with CSPM, creating a unified Security Posture Management (SPM) solution that provides holistic visibility and control over both application and cloud security. This evolution will empower organizations to proactively manage and mitigate risks across their entire technology stack. The ideal ASPM is not just a management platform but a powerful engine driving proactive security measures throughout the software development lifecycle.