Application Security Posture Management (ASPM) is revolutionizing how organizations approach application security. As a cutting-edge AppSec platform, ASPM offers continuous assessment, robust management, and proactive enhancement of modern application security, significantly bolstering an organization’s overall risk posture. By providing comprehensive visibility, intelligent detection, effective correlation, strategic prioritization, and streamlined remediation of security vulnerabilities and defects throughout the Software Development Lifecycle (SDLC), ASPM stands as a critical defense in today’s threat landscape.
ASPM achieves complete code to cloud coverage by aggregating data from diverse sources, including application security testing (AST) tools, repository data, and more. This wealth of information is then intelligently analyzed to pinpoint the most critical risks that could impact the business.
Think of ASPM platforms as a central command center for your security toolkit. They act as a sophisticated management and orchestration layer, empowering you to implement stringent security controls and consistently enforce security policies. By consolidating application security findings into a unified platform, ASPM provides an unparalleled, holistic view of security and risk across the entire organization. This centralized approach not only simplifies management but also significantly streamlines the remediation process for individual vulnerabilities.
ASPM delivers a powerful suite of functionalities, including:
- Code to Cloud Visibility: Gain an end-to-end perspective of your SDLC, encompassing your code, security tools, development processes, and critical data from operational environments like cloud platforms, containerized applications, and physical infrastructure. ASPM continuously monitors and proactively identifies vulnerabilities, potential misconfigurations in security tools, and other lurking weaknesses.
- Vulnerability Scanning: ASPM tools conduct regular and thorough scans of applications to detect known security issues. This involves leveraging a broad spectrum of both native and third-party application security scanning tools, such as advanced secrets scanning, Software Composition Analysis (SCA), and Static Application Security Testing (SAST).
- Prioritization and Risk Management: ASPM empowers organizations to effectively prioritize and manage security risks associated with their applications. By providing a clear risk-based prioritization, ASPM helps security teams make informed decisions regarding which vulnerabilities demand immediate attention based on their potential impact on the organization’s operations and assets.
- Remediation and Mitigation: Once vulnerabilities are detected, ASPM provides actionable guidance on how to effectively remediate or mitigate them. This can include specific code change recommendations, necessary configuration adjustments, or the seamless application of crucial security patches.
- Compliance Reporting: ASPM solutions are instrumental in simplifying compliance reporting, helping organizations adhere to critical security policies, industry standards, and regulatory mandates such as SSDF, SOC 2, and ISO 27001.
- Reporting and Analytics: ASPM tools offer comprehensive reporting and analytics capabilities that provide organizations with valuable insights into the security posture of their applications over time. These insightful reports can be used to meticulously track progress, demonstrate robust compliance, and make data-driven decisions to continuously improve security.
In essence, ASPM platforms are designed to proactively assess and significantly enhance the security of an organization’s applications, all while effectively reducing the often chaotic nature of modern AppSec management. In an era where cyber threats are increasingly sophisticated and application-centric, ASPM is indispensable for robust protection against attacks targeting the application layer.
Why ASPM is Mission-Critical
In today’s digital landscape, every company is, in essence, a software company. Applications have become the primary drivers of growth, and code is the invaluable “crown jewel” of the modern enterprise. This fundamental shift underscores the critical importance of application security.
However, effectively managing the security of code as it traverses complex pipelines and disparate environments is a monumental challenge. Without ASPM, organizations face critical blind spots, severely limited visibility, and a significantly elevated risk of vulnerabilities slipping through the cracks, potentially leading to severe consequences.
ASPM provides the solution, enabling organizations to:
Proactively Stop Code Risks Before They Materialize
Without the vigilance of ASPM, vulnerabilities often remain hidden until it’s devastatingly late, potentially triggering data breaches, costly operational downtime, and lasting reputational damage. ASPM empowers organizations to stop code risks in their tracks, preventing them from escalating into full-blown security incidents.
Minimize Developer Productivity Overhead
ASPM significantly reduces “developer productivity tax” by enabling development teams to concentrate their efforts on the vulnerabilities that truly matter. Instead of being bogged down by minor issues or overwhelmed by false positives, developers can focus on remediating critical risks that pose the greatest threat.
Lower Total Cost of Ownership
ASPM consolidates essential application security scanning tools into a cohesive platform, streamlining the entire application security process. By offering the option to replace disparate AppSec point solutions with a unified platform, ASPM demonstrably lowers the total cost of ownership associated with application security.
Simplify Application Security Complexity
Industry data reveals that a remarkable 90% of security professionals using a commercial ASPM platform report that their organizations have established a systematic approach to understanding overall risk and are consistently prioritizing the most critical vulnerabilities. This is because ASPM automates crucial security oversight, removing the burden of manual application security management and ensuring continuous vigilance.
Accelerate Time-to-Remediation
When vulnerabilities are discovered late in the development cycle or are scattered across disconnected tools, the remediation process becomes protracted and exceedingly challenging. ASPM resolves this bottleneck by consolidating all security data into a unified view, dramatically accelerating response times. This streamlined approach minimizes delays that could impact production timelines and significantly reduces the time and resources spent on fixing known issues.
Enable Strategic Resource Allocation
Without ASPM’s intelligent prioritization, security teams can be inundated with a deluge of alerts, leading to wasted resources on less-critical vulnerabilities while potentially neglecting those that pose genuine threats to the business. ASPM’s risk-based prioritization ensures that teams focus their efforts on the vulnerabilities that carry the highest risk, optimizing resource allocation and improving overall efficiency.
Safeguard Business Continuity and Customer Trust
Every undetected vulnerability has the potential to disrupt critical services, compromise sensitive data, and erode hard-earned customer trust. ASPM plays a pivotal role in ensuring that application security is not the weakest link in the organizational defense, ultimately safeguarding business continuity, protecting reputation, and maintaining unwavering customer trust.
ASPM’s Strategic Place in Cybersecurity
ASPM is not merely another security tool; it’s a vital and integral component of a comprehensive cybersecurity strategy.
In a threat landscape characterized by diversity and persistence, ASPM provides a dedicated and laser-focused approach to application security. It comprehensively addresses multiple critical aspects essential for securing the application lifecycle, including:
- Pipeline and Build Security
- Posture Management
- Compliance
- Application Security Testing
While other security layers fortify infrastructure, networks, and endpoints, ASPM zeroes in on application-specific security, delivering the specialized tools required to protect the very foundation of a company’s digital assets – its code.
By strategically integrating ASPM into a broader security framework, organizations gain a highly effective, risk-focused approach that not only enhances application security but also aligns with stringent regulatory requirements and seamlessly complements other cybersecurity initiatives to build a robust and resilient defense-in-depth strategy.
ASPM in Action: Real-World Use Cases
Application Security Posture Management (ASPM) solutions are not theoretical concepts; they deliver tangible value in real-world scenarios. ASPM empowers organizations to proactively manage application security, shrink the attack surface, accelerate Mean Time to Resolution (MTTR), and fundamentally enhance their overall security posture. ASPM represents the next evolution in application security, playing a mission-critical role in modern cybersecurity strategies. Applications are consistently the primary targets of cyberattacks, making their robust security paramount for protecting sensitive data and ensuring uninterrupted business continuity.
To better understand the practical applications of ASPM tools, consider these compelling use cases:
| Use Case | Description | Benefits |
|---|---|---|
| Visibility & Optionality | Aggregates data from diverse security tools (both native and third-party) into a unified, single-pane-of-glass interface | Reduces complexity, enhances operational efficiency, lowers licensing costs by optimizing tool utilization |
| Prioritization and Risk Management | Intelligently prioritizes vulnerabilities based on their potential business impact and exploitability | Focuses remediation efforts on the most critical issues first, significantly enhances risk management effectiveness |
| Enhanced Collaboration | Seamlessly integrates security checks directly into the existing development workflow | Identifies and remediates vulnerabilities earlier in the SDLC, accelerates secure software releases and reduces delays |
| Compliance and Reporting | Automates and streamlines compliance management, generating comprehensive audit reports for various standards | Ensures adherence to regulatory mandates, provides demonstrable evidence of security best practices, simplifies audits |
| Incident Response and Remediation | Provides step-by-step guidance on vulnerability remediation and threat mitigation | Streamlines incident response workflows, minimizes disruption to development cycles, accelerates MTTR |
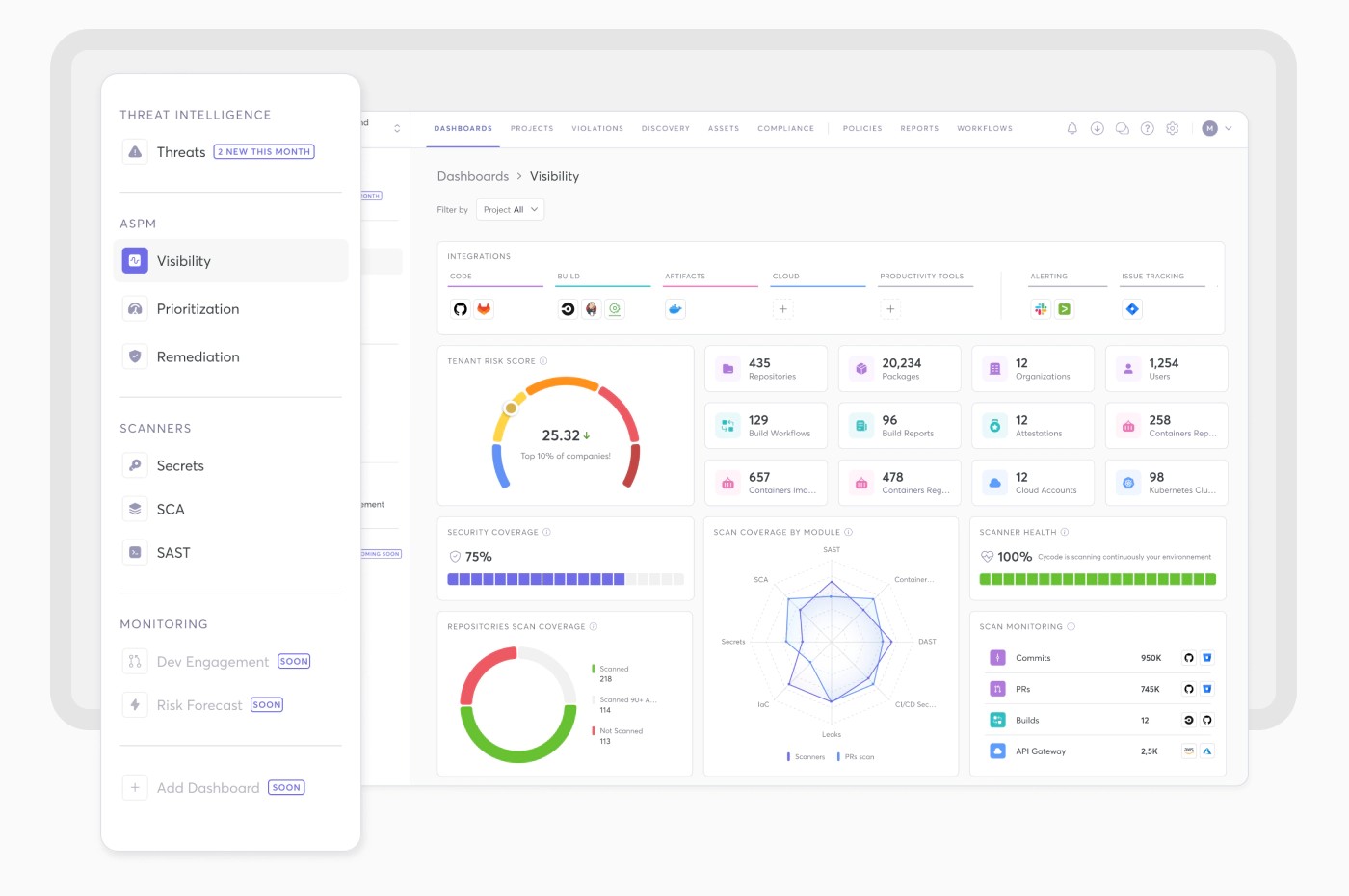




Visibility & Optionality: Breaking Down Tool Silos
Industry research reveals that organizations grapple with an average of 50 AppSec tools, with a staggering 67% of respondents citing tool management as a major challenge. This tool sprawl significantly reduces visibility, creates dangerous blind spots, and hinders effective collaboration between security and development teams.
ASPM platforms address this challenge head-on by unifying disparate security tools and data sources into a centralized interface. This consolidation simplifies management and dramatically enhances visibility across the entire CI/CD pipeline and SDLC.
Crucially, ASPM solutions offer flexibility. They can consolidate existing third-party tools, maximizing current investments, or act as a comprehensive replacement, offering built-in native tools for SAST, SCA, and other essential security scanning capabilities.
The tangible results include reduced complexity, streamlined workflows, improved operational efficiency, and significant cost savings.
Alt text: Centralized threat visibility dashboard in Cycode ASPM platform, showing a unified view of security findings across the application lifecycle.
Prioritization and Risk Management: Cutting Through Alert Noise
A significant 81% of security professionals report that their developer teams are overwhelmed by excessive false positives and debilitating alert fatigue. ASPM directly tackles alert fatigue by intelligently analyzing critical factors such as potential business impact, ease of exploitability, and severity of vulnerabilities. By assigning a risk score to each vulnerability, ASPM provides a data-driven approach to prioritization.
This intelligent prioritization ensures that security teams can strategically focus their limited resources and efforts on the vulnerabilities that present the most significant threat to the organization. By focusing on high-impact risks, ASPM ultimately improves the overall security posture and minimizes potential damage from cyberattacks.
Alt text: Advertisement for a comprehensive buyer’s guide on application security posture management (ASPM) platforms.
Enhanced Collaboration: Bridging Security and Development
ASPM platforms effectively bridge the persistent gap between security and development teams by seamlessly integrating security checks into the SDLC. This early integration empowers developers to identify and remediate vulnerabilities much earlier in the development process, resulting in numerous benefits:
- Reduced Rework: By identifying and addressing vulnerabilities early in the cycle, developers can fix them before code becomes deeply embedded in the codebase. This significantly reduces the need for costly and time-consuming rework later in the development lifecycle.
- Faster Development Cycles: Early vulnerability detection and remediation minimize delays traditionally caused by lengthy security reviews or last-minute bug fixes closer to release deadlines. This translates directly into faster development cycles and accelerated time-to-market for new features and applications.
- Empowered Developers: ASPM integration within developer workflows equips developers with the essential tools and contextual information they need to proactively write secure code from the outset. This fosters a culture of security ownership and shared responsibility within development teams.
- Enhanced Security Posture: By proactively addressing vulnerabilities early and consistently, organizations can significantly improve their overall application security posture and effectively reduce the attack surface exposed to potential threats.
Compliance and Reporting: Streamlined and Automated
ASPM platforms simplify the complexities of compliance management, transforming it into a streamlined and highly efficient process. By automating the generation of comprehensive reports for critical security standards like SOC 2 and ISO 27001, ASPM eliminates the cumbersome manual work that traditionally burdens security teams, freeing up valuable time and resources for more strategic security initiatives.
ASPM’s robust reporting capabilities provide auditors with a clear, comprehensive, and easily digestible view of an organization’s security posture. This streamlined reporting process makes audits smoother, faster, and less disruptive. Ultimately, ASPM ensures that applications consistently adhere to relevant security policies and regulations, mitigating the risk of non-compliance and avoiding potential financial penalties and reputational damage.
Incident Response and Remediation: Accelerating MTTR
A relentless barrage of vulnerability alerts can overwhelm security teams, while slow remediation times leave organizations exposed to potential data breaches and significant financial losses.
ASPM platforms directly address these critical challenges by empowering both security and development teams. ASPM doesn’t just identify vulnerabilities; it provides clear, step-by-step instructions for developers to effectively fix or mitigate threats. Advanced features like bulk remediation enable developers to address vulnerabilities directly within their familiar workflows, minimizing disruption to ongoing development cycles and accelerating remediation.
This collaborative and streamlined approach leads to a substantial reduction in Mean Time to Remediate (MTTR), ensuring that vulnerabilities are addressed swiftly and effectively, minimizing potential impact and risk.
Alt text: Banner advertisement promoting the “State of ASPM 2025” report, highlighting key trends and insights in application security posture management.
Core Components of a Complete ASPM Platform
For an ASPM platform to be truly comprehensive and effective, it must incorporate several essential components. These components should provide robust coverage across pipeline security, application security, and posture management. A complete ASPM solution should offer native scanners while also maintaining the flexibility to integrate seamlessly with third-party scanners that organizations may already utilize. An ASPM platform lacking native scanners or offering limited coverage is considered incomplete or merely a standalone vulnerability aggregator.
Pipeline Security: Securing the Foundation
Development pipelines represent a significant blind spot in traditional AppSec strategies. Securing these pipelines is paramount for safeguarding applications and sensitive data. Given the increasing number of high-profile breaches stemming from exposed secrets or compromised developer accounts, pipeline security must be a fundamental pillar of any robust application security strategy.
Comprehensive pipeline security should encompass the following critical areas:
Application Security: Protecting the Core
For most organizations, applications are the lifeblood of their operations. Protecting these applications is not just a security imperative; it’s a business necessity. Organizations must prioritize delivering innovative and secure software to their customers. Failing to do so exposes them to substantial financial losses, severe reputational damage, and potential legal repercussions.
Complete ASPM solutions should offer a comprehensive suite of native AppSec scanners capable of replacing legacy tooling and point solutions. At a minimum, ASPM should provide native scanning capabilities for:
Application Risk: Flexibility and Integration
For an ASPM solution to be truly effective and adaptable to diverse organizational needs, it must be inherently open and flexible. This necessitates providing both robust native scanners and seamless third-party integrations. This dual approach accommodates organizations that prefer to leverage their existing scanning tools and workflows.
Some organizations may prefer to avoid the time, resources, and effort associated with implementing entirely new scanners. If an organization has already invested in scanners that are finely tuned to meet their specific requirements, they should not be forced to adopt a completely new toolset.
ASPM platforms must possess the capability to seamlessly combine data from both native and third-party scanners, catering to a wide range of organizational preferences and needs. Simultaneously, ASPM solutions should provide a robust set of native scanners to facilitate tool consolidation, reduce redundancy, or address any gaps in scanning coverage that an organization may have.
Key Benefits of ASPM
A complete ASPM platform empowers organizations to strategically select and seamlessly connect the application security scanning tools that best align with their specific needs and risk profile. ASPM also provides the crucial ability to prioritize vulnerabilities based on business risk, potential exploitability, and overall severity. Finally, ASPM significantly improves the management and remediation of security alerts, benefiting both security and development teams in numerous ways.
1. Correlation and Orchestration: Context is King
The true power of an ASPM platform lies in its ability to provide rich context for every identified vulnerability. This contextualization is particularly critical given that industry research consistently highlights visibility into security and risk posture as the number one application security concern among security professionals.
By contextualizing vulnerabilities, ASPM enables organizations to gain deeper, more actionable insights into both individual defects and their overall risk posture.
Correlation and orchestration are paramount in this process because they effectively eliminate false positives, allowing teams to understand when multiple alerts are related to a single root cause. This intelligent correlation, in turn, minimizes alert fatigue, eliminates critical blind spots, and significantly improves vulnerability prioritization and remediation efforts.
2. Tool Consolidation: Streamlining Security Stacks
By centralizing all security tooling and data across the SDLC into a unified platform, organizations can effectively eliminate silos, reduce context switching for security teams, remove blind spots in security coverage, and gain enhanced context into overall risk. This increased visibility and richer context empowers security teams to significantly reduce alert noise by effectively deduplicating redundant alerts. Tool consolidation also delivers tangible cost savings by eliminating redundant point solution license fees and freeing up valuable personnel resources previously dedicated to managing disparate tools.
The operational efficiency gained by leveraging a complete ASPM platform can create the effect of significantly increasing the security-to-developer ratio, potentially reaching ratios as efficient as 1:20, without requiring any expansion of AppSec staff.
3. End-to-End Security: Comprehensive SDLC Protection
Because prioritization, risk management, remediation, and mitigation are core functionalities of robust ASPM platforms, organizations are empowered to reduce alert noise by up to 90% and strategically protect their entire SDLC against the most critical 1% of vulnerabilities that pose the greatest risk.
This comprehensive, end-to-end security approach enables organizations to innovate securely, confidently meet stringent regulatory and compliance requirements, and proactively prevent costly and damaging data breaches.
4. Seamless Security and Development Collaboration
“Shift left” security is a widely adopted but often imperfect practice, frequently creating friction and tension between security and development teams. ASPM effectively reduces this friction by providing developers with the tools and context they need to fix vulnerabilities directly within the development environments they use daily.
In fact, a compelling 97% of security leaders who have consolidated their security tool stack with ASPM have reported a significant improvement in their relationship and collaboration with development teams.
5. Developer-Centric Workflows: Adoption is Key
An application security tool, regardless of its technical sophistication, is fundamentally worthless if developers resist using it. ASPM solutions are no exception. For an organization to realize the full value from its ASPM investment and effectively promote secure coding best practices across development teams, the platform must provide developer-friendly workflows. These workflows should include seamless integrations with IDEs, CLIs, PR scanning processes, and issue tracking systems like Jira.
To successfully shift security left in a controlled and sustainable manner, it’s essential to meet developers where they work and integrate security into their existing workflows. Eliminating context switching and minimizing disruption is key to developer adoption and the successful implementation of ASPM.
Platform Comparison: ASPM vs. Standalone ASPM vs. AST vs. CSPM vs. CNAPP
| Complete Application Security Posture Management (ASPM) Platform | Standalone ASPM or Vulnerability Aggregators | Cloud Security Posture Management (CSPM) | Application Security Testing (AST) |
|---|---|---|---|
| Definition | A Complete ASPM will have native scanning capabilities from code to cloud (Secrets, SAST, SCA, CI/CD, etc.) and the ability to integrate third-party security and developer tools, similar to Cycode’s ConnectorX capabilities. | Standalone ASPMs or vulnerability aggregators ingest vulnerabilities from multiple security tools but lack native scanning, prioritization, or remediation capabilities. | CSPM focuses solely on monitoring and securing cloud environments (not code) for risks, vulnerabilities, and misconfigurations. |
| Visibility & Coverage | Code to Cloud Scanning with comprehensive Native Scanners and seamless integration with 3rd party security and developer tools, providing complete visibility, prioritization, and remediation. | No native scanning capabilities. Relies solely on third-party security connections for vulnerability data ingestion. | Cloud and container security scanning coverage, focused on cloud infrastructure. |
| Focus Area | Code to Cloud Security, providing comprehensive coverage across the entire software supply chain and SDLC. | Primarily Application Security, with limited capabilities beyond vulnerability aggregation. | Exclusively Cloud Security, focused on cloud infrastructure and configurations. |
| Examples | Native scanners for Secrets, SCA, SAST, CI/CD, Code Leaks, IaC, Container Security, and more. | Primarily 3rd party security tool integrations and vulnerability data aggregation. | Cloud security configuration monitoring, compliance checks, cloud misconfiguration detection. |
Complete ASPM vs. Incomplete ASPM (Standalone ASPM)
While numerous vendors claim to offer ASPM platforms, many solutions lack critical core functionalities. Understanding the difference between complete and incomplete ASPM solutions is crucial for making informed security decisions.
A complete ASPM platform is defined by having a comprehensive suite of native application security scanning tools. This suite typically includes:
Complete ASPM platforms also prioritize flexibility, enabling organizations to easily select and connect the third-party tools that best suit their unique ecosystem, existing investments, and specific security requirements.
In contrast, incomplete ASPM solutions, often referred to as standalone ASPM or vulnerability aggregators, typically lack native scanning capabilities. Instead, they are limited to ingesting vulnerability data solely from third-party scanners. Even if they offer limited scanning capabilities, they often lack one or more core AST tools, such as SAST, SCA, or comprehensive CI/CD security scanning.
Organizations relying on incomplete ASPM solutions become dependent on the vendor to provide and maintain accurate and effective integrations with a wide range of third-party tools, similar to the limitations of traditional point solutions.
ASPM vs. AST: Beyond Point Solutions
Application Security Testing (AST) tools are a subset within the broader category of ASPM. AST tools are specifically designed to scan code and pinpoint security vulnerabilities. Static Application Security Testing (SAST), Software Composition Analysis (SCA), Dynamic Analysis (DAST), and Infrastructure as Code (IaC) scanning all fall under the umbrella of AST. While these point solutions provide valuable vulnerability data within their specific domains, they generally lack the sophisticated context, correlation, and comprehensive visibility offered by a complete ASPM platform.
Complete ASPM, on the other hand, consolidates the findings from these disparate AST point solutions, providing a holistic, organization-wide view of application security risk. ASPM intelligently analyzes findings from various scanning tools, then prioritizes them based on risk, effectively identifying the critical 1% of vulnerabilities that truly impact an organization’s business risk.
The enhanced context delivered by ASPM empowers developers to focus their remediation efforts on true positives that have the most significant impact on reducing overall risk. ASPM also provides security teams with centralized visibility and robust controls to consistently enforce security policies across the entire application portfolio.
ASPM vs. CSPM: Addressing Different Security Domains
Cloud Security Posture Management (CSPM) focuses on securing cloud infrastructure. This encompasses Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS) environments. CSPM tools scan cloud configurations for common misconfigurations, compliance violations, and security weaknesses to establish a secure cloud-based infrastructure for application deployment.
In contrast, ASPM is specifically designed to secure applications throughout the entire Software Development Lifecycle (SDLC), from code to cloud deployment. ASPM helps organizations proactively identify, intelligently prioritize, and efficiently remediate security risks associated with their applications across all environments. Complete ASPM platforms monitor and identify security risks in applications deployed in both on-premises and cloud-based environments, leveraging a powerful combination of automation, intelligent data correlation, and risk assessment to provide organizations with a comprehensive, unified view of their application security posture.
ASPM vs. CNAPP: Scope and Functionality
ASPM and Cloud Native Application Protection Platform (CNAPP) both play critical roles in enhancing the security of modern applications. However, they differ significantly in their scope, core functionality, and integration capabilities.
CNAPP primarily focuses on securing cloud-native applications. CNAPP provides tailored protections specifically designed for containerized workloads, microservices architectures, and APIs operating within dynamic cloud environments. CNAPP’s capabilities include container image scanning, runtime protection for containers, and API security controls specifically tailored to cloud-native architectures.
CNAPPs are generally tightly integrated with container orchestration platforms like Kubernetes and various cloud services, providing security controls that seamlessly align with the dynamic and ephemeral nature of cloud-native deployments.
Complete ASPM platforms, in contrast, assess and manage the overall security posture of applications across diverse environments, delivering a holistic view of vulnerabilities that spans from code development to cloud deployment. ASPM platforms are designed to integrate with a wide range of security tools and address security concerns throughout the entire application lifecycle, providing a broader and more comprehensive approach to application security management.
Evaluating and Selecting an ASPM Platform
ASPM empowers organizations to unify security findings across disparate tools, gain comprehensive visibility into application risk, and drive significant efficiency improvements in threat prioritization and remediation workflows.
Because ASPM is a relatively new category of security tooling, security teams may be unsure how to effectively evaluate and select the right solution for their specific needs.
Choosing the Right ASPM Solution
When evaluating a complete ASPM platform, consider these 10 critical questions before making a purchasing decision:
- Integration Capabilities: Does the ASPM platform seamlessly integrate with the existing tools you currently utilize, including AppSec scanners, ticketing systems, and CI/CD tools? Does it offer the flexibility to integrate with future tools and emerging technologies?
- Native AppSec Scanners: Does the platform provide its own suite of high-quality, native AppSec scanners for essential security testing capabilities like Secrets detection, Software Composition Analysis (SCA), Static Application Security Testing (SAST), CI/CD security, Infrastructure as Code (IaC) scanning, and more?
- Visibility, Prioritization, and Remediation: Does the platform provide comprehensive visibility into application security risk, intelligent vulnerability prioritization based on business impact, and streamlined remediation workflows? Can you easily create custom security policies and tailor workflows to your organization’s specific needs?
- Automation and Orchestration: How sophisticated and robust are the platform’s automation and orchestration capabilities? Can it automate key security processes and orchestrate complex remediation workflows?
- Accuracy and Alert Management: How accurate is the platform in identifying true positives and minimizing false positives/false negatives? Does it effectively deduplicate alerts to reduce noise and alert fatigue?
- User Interface and Reporting: Is the user interface intuitive, user-friendly, and easy to navigate for both security and development teams? Are the reporting dashboards comprehensive yet easy to understand and use for various stakeholders?
- Developer Workflow Integration: Does the platform seamlessly integrate with developer workflows to identify and address security defects early in the SDLC, minimizing disruption and friction?
- Governance and Compliance: Does the platform provide the necessary features and reporting capabilities to satisfy relevant governance and compliance requirements, such as SOC 2, ISO 27001, and others?
- Security and Development Collaboration: Does the platform facilitate and enhance collaboration between security teams and developers, fostering a shared responsibility for application security?
- AI and Advanced Capabilities: Does the platform leverage Artificial Intelligence (AI) or other advanced technologies to improve the overall efficacy and accuracy of the tool? For example, does it utilize AI for fine-tuning scan results, providing contextual insights, or enabling users to build queries using natural language?
Measuring ASPM Program Success
Alt text: Advertisement for a book providing insights on the future of code resilience and application security posture management.
The following Key Performance Indicators (KPIs) are valuable for measuring the success and effectiveness of your ASPM program. These KPIs provide insights into an organization’s overall security posture, operational efficiency metrics, and the developer experience:
- Vulnerability detection rate (effectiveness in identifying vulnerabilities)
- False positive rate (accuracy of vulnerability findings)
- Mean time to remediate (MTTR – speed of vulnerability remediation)
- Coverage of application portfolio (breadth of security coverage)
- Compliance adherence (level of compliance with security standards)
- Number of high-risk vulnerabilities (reduction in critical vulnerabilities)
- Incident response time (speed of response to security incidents)
- Cost of remediation (efficiency of remediation processes)
- Developer feedback on tool usability (developer satisfaction and adoption)
- Incident response collaboration (effectiveness of security and development teamwork)
Organizations aiming to improve these key metrics should consider implementing a complete ASPM solution. Innovative, software-driven companies like PayPal, Solaris, and Rapyd have already successfully implemented Cycode’s complete ASPM platform, achieving significant improvements in their application security posture.
Explore Complete ASPM Further
Cycode is at the forefront of the ASPM conversation, committed to empowering security professionals with the knowledge and resources they need to build successful, cross-functional security strategies. Cycode consistently leverages first-hand insights and learnings from industry experts at leading global organizations. Learning from peers in the industry is invaluable. Explore these free resources to advance your ASPM knowledge:
Alt text: Image promoting ASPM resources and educational materials, inviting users to learn more about application security posture management.
Achieve Peace of Mind with Cycode’s Complete ASPM
Cycode is the leading Application Security Posture Management (ASPM) platform, delivering peace of mind to its customers. Cycode’s complete ASPM platform enables organizations to scale and standardize developer security without hindering business agility, resulting in safer code delivered faster. Cycode can replace existing application security testing tools or seamlessly integrate with them, providing unparalleled cyber resilience through unmatched visibility, risk-driven prioritization, and just-in-time remediation of code vulnerabilities at scale. Cycode’s Risk Intelligence Graph (RIG), the intelligent engine powering the platform, provides end-to-end traceability across the entire SDLC using natural language queries.
Here’s what distinguishes Cycode:
- Flexibility: Cycode allows you to utilize its native scanners or seamlessly connect your existing third-party scanners, maximizing your current security investments.
- Risk Intelligence Graph (RIG): Our proprietary Risk Intelligence Graph delivers unmatched visibility, accuracy, prioritization, and end-to-end traceability across the entire SDLC, providing unparalleled context and insights.
- Developer-Centric Approach: Cycode was founded by developers and is the only ASPM platform that truly bridges the gap between security and development teams, fostering collaboration and shared responsibility.
- Proactive Threat Intelligence: Our world-class research team provides timely security notifications on zero-day threats directly within the platform, enabling proactive defense against emerging vulnerabilities.
Want to delve deeper into Cycode’s complete ASPM platform? Book a demo today to discover how Cycode can help you achieve faster time to value, significantly reduce critical vulnerabilities, and accelerate remediation timelines, strengthening your overall application security posture.
Originally published: November 2, 2023

