In today’s rapidly evolving digital landscape, maintaining robust cybersecurity defenses is paramount for organizations of all sizes. Network scanning tools have emerged as indispensable security solutions, acting as the first line of defense against cyber threats and network vulnerabilities. While traditional network scanning offers valuable insights, the advent of Automated Network Scanning Tools has revolutionized the field, providing enhanced efficiency, accuracy, and continuous protection. This article delves into the world of automated network scanning, exploring its significance, benefits, and the top tools available in the market.
Why Automated Network Scanning is a Game Changer
Automated network scanning takes the fundamental principles of network scanning and elevates them to a new level of effectiveness. The shift towards automation addresses the growing complexity of modern networks and the relentless nature of cyber threats. Here’s why automation is a game-changer in network security:
- Enhanced Threat Detection: Automated tools continuously scan your network, proactively identifying potential security risks and vulnerabilities in real-time. This constant vigilance ensures that threats are detected early, minimizing the window of opportunity for breaches and attacks.
- Streamlined Compliance: Meeting regulatory requirements and security standards often involves regular network assessments. Automated scanning simplifies this process, providing consistent and documented evidence of compliance efforts, reducing manual work and potential oversights.
- Optimized Network Performance: Beyond security, automated scanning tools can monitor network performance metrics. By identifying bottlenecks and inefficiencies automatically, these tools help optimize network operations, ensuring smooth and reliable performance.
- Significant Cost Savings: Preventing security incidents and network downtime is crucial for cost management. Automated scanning reduces the risk of expensive breaches and performance disruptions, leading to substantial long-term cost savings compared to reactive security measures.
- Increased Efficiency and Speed: Manual network scanning is time-consuming and resource-intensive. Automation significantly accelerates the scanning process, freeing up IT staff to focus on strategic tasks while ensuring more frequent and comprehensive scans.
- Reduced Human Error: Manual processes are prone to human error. Automated scanning minimizes this risk by executing scans with precision and consistency, ensuring reliable and accurate results every time.
- Continuous Monitoring and Real-time Insights: Automated tools operate around the clock, providing continuous monitoring and real-time insights into your network’s security posture. This constant vigilance is essential in today’s dynamic threat environment.
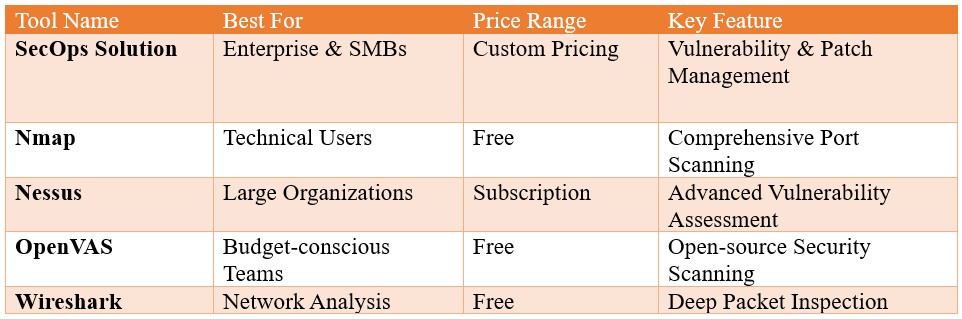 Comparison of network scanning tools features and capabilities, highlighting the importance of automated scanning for comprehensive security.
Comparison of network scanning tools features and capabilities, highlighting the importance of automated scanning for comprehensive security.
Key Features of Automated Network Scanning Tools
To effectively leverage automated network scanning, it’s important to understand the core features that make these tools powerful. Look for these essential functionalities when evaluating automated solutions:
- Automated Vulnerability Scanning: This is the cornerstone of automated network scanning. Tools automatically identify known vulnerabilities across your network infrastructure, including servers, workstations, and network devices.
- Automated Patch Management Integration: Many advanced automated tools integrate with patch management systems. Once vulnerabilities are identified, the tool can automatically initiate or recommend patching processes, streamlining remediation efforts.
- Automated Network Discovery and Mapping: Automated tools can automatically discover all devices connected to your network and create a detailed network map. This provides a comprehensive view of your network assets, crucial for effective security management.
- Customizable Scan Scheduling: Automation allows you to schedule scans to run regularly, whether daily, weekly, or on a custom schedule. This ensures continuous monitoring without manual intervention.
- Automated Reporting and Alerting: Automated tools generate reports on scan results and send alerts for critical vulnerabilities or security issues. This allows security teams to quickly identify and respond to threats.
- Integration with Security Information and Event Management (SIEM) Systems: Integration with SIEM systems enables automated tools to feed scan data into a centralized security management platform, enhancing threat correlation and incident response capabilities.
- Compliance Reporting: Automated scanning tools often include features to generate reports specifically for compliance requirements, such as PCI DSS, HIPAA, or GDPR, simplifying audit processes.
- Prioritization and Risk Scoring: Advanced tools automatically prioritize vulnerabilities based on severity and potential impact, helping security teams focus on the most critical issues first.
- Agent-based and Agentless Scanning: Depending on your network environment, automated tools may offer both agent-based and agentless scanning options, providing flexibility and comprehensive coverage.
Top Automated Network Scanning Tools: In-Depth Review
Selecting the right automated network scanning tool is crucial for maximizing your cybersecurity posture. Here’s a review of some of the top tools available, highlighting their automated features and capabilities:
1. SecOps Solution
Features: SecOps Solution is a comprehensive, agentless vulnerability and patch management platform with a strong focus on automation. It excels in automated vulnerability identification, prioritization, and remediation. Key automated features include:
- Automated Patch Management: Provides status updates for every patch, customizable patch policies, pre-validated and revertible patches, and support for driver and offline patching, all automated for efficiency.
- Automated Vulnerability Scanning: Offers continuous vulnerability scanning with rapid identification and prioritization of threats across infrastructure and applications.
- Agentless and Agent-based Deployment: Supports both deployment modes, providing flexibility for different network environments while maintaining automated scanning capabilities.
- Customizable Reporting and Alerts: Automated generation of detailed reports and alerts based on scan results, enabling proactive security management.
Pricing: Subscription-based, tailored to organizational needs. Contact SecOps Solution for specific pricing.
Best for: Organizations of all sizes seeking a robust, feature-rich, and highly automated vulnerability and patch management solution.
2. Nmap (Network Mapper)
Features: Nmap, while primarily a command-line tool, offers powerful scripting capabilities that enable automation.
- Scripting Engine (NSE): Nmap’s Scripting Engine allows users to write scripts to automate various scanning tasks, including vulnerability detection, service discovery, and more.
- Scheduled Scans via Cron: Nmap scans can be automated using cron jobs on Linux/Unix systems or Task Scheduler on Windows for regular, scheduled scans.
- Output to Script-Friendly Formats: Nmap can output scan results in formats like XML, making it easy to parse and process data automatically with other scripts or tools.
Pricing: Free and open-source.
Best for: Network administrators and security professionals who are comfortable with scripting and need a highly customizable and powerful automated scanning tool at no cost.
Drawback: Requires technical expertise in scripting to fully leverage its automation capabilities. Command-line interface can be less user-friendly for beginners.
3. Nessus
Features: Nessus is a widely adopted vulnerability scanner known for its comprehensive vulnerability database and user-friendly interface, with significant automation features.
- Scheduled Scans: Easily schedule recurring scans to run automatically at defined intervals, ensuring continuous vulnerability monitoring.
- Policy-Based Scanning: Create and apply scanning policies to automate scan configurations and ensure consistent scanning practices across the organization.
- Automated Reporting and Notifications: Nessus automatically generates reports after each scan and can send email notifications for critical vulnerabilities or scan completion.
- Remediation Tracking: While not fully automated remediation, Nessus helps automate the tracking of remediation efforts by rescanning to verify vulnerability fixes.
Pricing: Offers free version for personal use, with paid subscription plans for professional and enterprise use.
Best for: Enterprises and large organizations requiring robust, user-friendly automated vulnerability scanning and compliance management.
Drawback: Professional and enterprise editions can be costly, potentially less accessible for small businesses.
4. OpenVAS (Open Vulnerability Assessment System)
Features: OpenVAS is a free and open-source vulnerability scanner that provides a strong alternative to commercial tools, with good automation capabilities.
- Scheduled Scans: Supports scheduled scans for automated, regular vulnerability assessments.
- Alerting and Reporting: Offers automated alerting and reporting features to notify users of scan results and identified vulnerabilities.
- Command-Line Interface and API: Provides a command-line interface and API for scripting and automating scan management and data processing.
Pricing: Free and open-source.
Best for: Security-conscious businesses and IT professionals seeking a cost-effective, automated vulnerability assessment tool.
Drawback: May require more technical expertise to set up and manage compared to commercial solutions. Potential for false positives may necessitate manual verification.
5. QualysGuard Vulnerability Management
Features: QualysGuard is a cloud-based vulnerability management platform with a strong emphasis on automation and continuous monitoring.
- Continuous Vulnerability Monitoring: Provides automated, continuous scanning and monitoring of network assets for vulnerabilities.
- Automated Patch Detection: Automatically detects missing patches and can integrate with patch management solutions (though patch deployment is not fully automated within QualysGuard itself).
- Policy Compliance Monitoring: Automates compliance monitoring against various security standards and regulations.
- Automated Reporting and Dashboards: Offers customizable dashboards and automated report generation for real-time visibility and analysis.
Pricing: Subscription-based, tiered pricing depending on the number of assets.
Best for: Enterprises prioritizing cloud-based, comprehensive, and highly automated vulnerability management solutions.
Drawback: Subscription costs can be relatively high for smaller organizations.
6. Acunetix Vulnerability Scanner
Features: Acunetix specializes in web application vulnerability scanning and includes robust automation features.
- Automated Web Application Scanning: Automatically crawls and scans web applications and APIs for a wide range of vulnerabilities, including SQL injection and XSS.
- Scheduled Scans: Allows scheduling of automated scans to regularly assess web application security.
- Integration with CI/CD Pipelines: Can be integrated into CI/CD pipelines to automate security testing during the development lifecycle.
- Automated Reporting and Issue Tracking: Generates detailed reports and can integrate with issue tracking systems to automate vulnerability remediation workflows.
Pricing: Various licensing options, including on-premises and cloud-based plans.
Best for: Businesses and developers focused on securing web applications and APIs with automated vulnerability scanning.
Drawback: Pricing may be a barrier for smaller organizations or individuals needing a lower-cost solution.
Choosing the Right Automated Scanning Tool for Your Needs
Selecting the optimal automated network scanning tool requires careful consideration of your organization’s specific needs and resources. Focus on these key factors:
-
Organization Size and Complexity:
- Enterprise Requirements: Large, complex networks often benefit from comprehensive, enterprise-grade solutions like SecOps Solution or QualysGuard, which offer extensive automation and scalability.
- SMB Needs: Smaller businesses may find cost-effective and user-friendly options like Nessus or OpenVAS suitable, especially if they have in-house technical expertise to manage automation features.
- Resource Availability: Consider your IT team’s size and expertise. Fully automated tools can reduce the workload on IT staff, while tools requiring scripting may need dedicated personnel.
-
Technical Expertise:
- Team Capabilities: Evaluate your team’s technical skills. Some tools, like Nmap, require scripting knowledge for advanced automation, while others offer more user-friendly, GUI-based automation features.
- Learning Curve: Consider the learning curve associated with each tool. Some tools are more intuitive and easier to set up and automate than others.
- Support Requirements: Assess the level of vendor support needed. Commercial solutions typically offer dedicated support, while open-source tools rely on community support.
-
Budget Constraints:
- Free vs. Paid Options: Open-source tools like Nmap and OpenVAS are free, but may require more technical effort to automate. Commercial tools offer more features and user-friendliness but come with subscription costs.
- ROI Considerations: Evaluate the return on investment (ROI) for each tool. Consider the potential cost savings from preventing security breaches and improving network efficiency through automation.
- Scalability Costs: If your organization is growing, consider the scalability of the tool and how pricing scales with increased network size.
Best Practices for Automated Network Scanning
To maximize the effectiveness of automated network scanning tools, implement these best practices:
- Establish a Regular Automated Scanning Schedule: Automate scans to run daily for critical systems and weekly for comprehensive network assessments. Regular scans ensure continuous monitoring and timely detection of new vulnerabilities.
- Ensure Comprehensive Automated Coverage: Configure your automated tools to scan all critical network segments, devices, and applications. Comprehensive coverage is essential to identify vulnerabilities across your entire attack surface.
- Implement Automated False Positive Management: Configure your tools to minimize false positives through proper tuning and exception handling. Establish a process for reviewing and verifying scan results to differentiate between true vulnerabilities and false positives.
- Develop an Automated Response Planning Framework: Integrate automated scanning with your incident response plan. Define automated workflows for vulnerability remediation, such as automated patching or alerting relevant teams upon detection of critical vulnerabilities.
- Provide Team Training on Automated Scanning Tools: Ensure your security team is properly trained on how to use and manage automated scanning tools effectively. Training should cover tool configuration, scan scheduling, report analysis, and automated response procedures.
FAQ
What is the best free automated network scanning tool?
Nmap, with its scripting engine, is the best free automated network scanning tool for technically proficient users. It offers extensive customization and automation capabilities through scripting, making it a powerful option at no cost.
How often should I run automated network scans?
For critical systems and internet-facing applications, daily automated scans are recommended. Weekly comprehensive scans of the entire network are a best practice for most organizations to maintain a strong security posture.
Can automated network scanning tools impact performance?
Modern automated network scanning tools, especially solutions like SecOps Solution, are designed to minimize network impact. They use techniques to optimize scanning speed and reduce resource consumption, ensuring minimal disruption to network performance while maintaining comprehensive coverage. Choosing tools with efficient scanning engines and configurable scan intensity is crucial.
Conclusion
Automated network scanning tools are indispensable for modern cybersecurity, providing proactive threat detection, streamlined compliance, and optimized network performance. While free tools like Nmap offer robust automation capabilities for those with technical expertise, enterprise solutions like SecOps Solution and QualysGuard provide comprehensive, user-friendly, and highly automated platforms for organizations of all sizes. By carefully considering your organization’s needs, technical expertise, and budget, and by implementing best practices for automated scanning, you can significantly enhance your security posture and stay ahead of evolving cyber threats.
SecOps Solution is a Full-stack Patch and Vulnerability Management Platform that helps organizations identify, prioritize, and remediate security vulnerabilities and misconfigurations in seconds through automation.
To learn more about leveraging automated scanning for your organization, get in touch with SecOps Solution today.

