Keyless entry systems have become a standard feature in modern vehicles, offering convenience and ease of access. However, this technology also introduces potential security vulnerabilities. Understanding how key fobs work and the tools that can interact with them, including automotive scan tools capable of duplicating fobs, is crucial for vehicle owners. This article will delve into the realm of key fob security, exploring both the convenience and the risks associated with these systems.
Modern car security systems rely on radio signals transmitted between the key fob and the vehicle. When you press a button on your fob, it sends a unique code to your car, allowing actions like unlocking doors or starting the engine. However, sophisticated techniques, such as relay attacks and rolljam attacks, exploit these radio signals to compromise vehicle security.
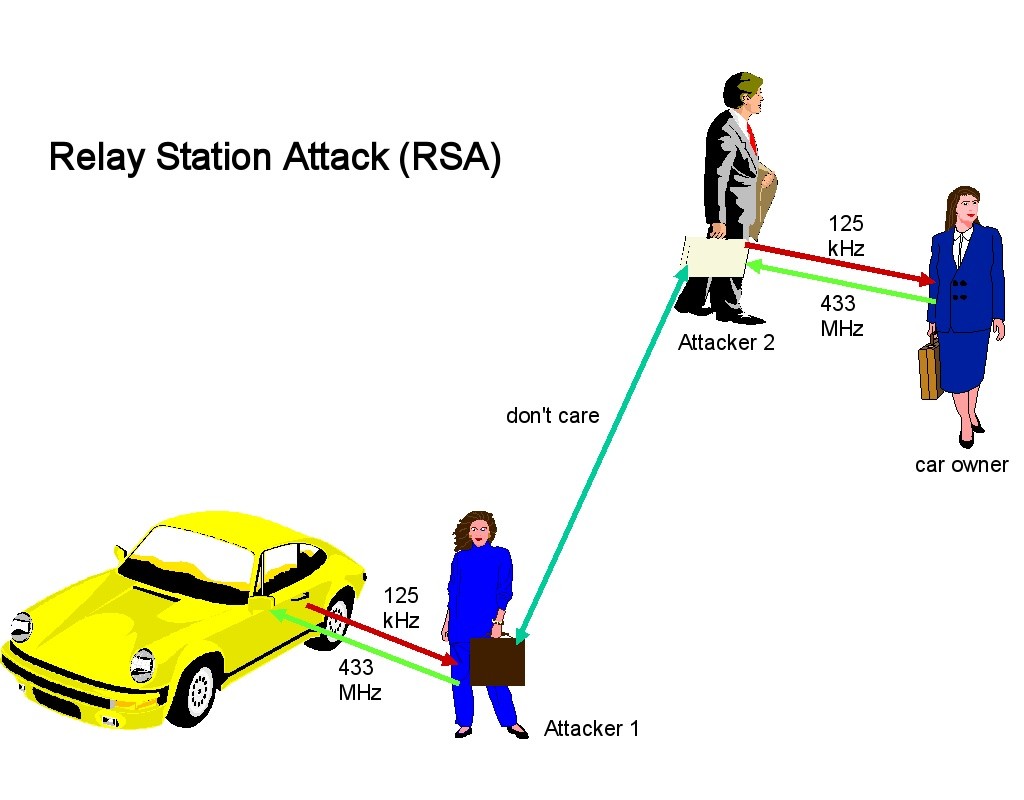
Relay attacks involve an attacker capturing the signal from your key fob and relaying it to another device near your car. This makes your car think the legitimate fob is nearby, enabling unauthorized access. Imagine someone standing close to your house or even in a public place, capturing your fob’s signal and relaying it to a partner near your vehicle. This is essentially how a relay attack unfolds.
Rolljam attacks are slightly different. They involve jamming the signal from your key fob while simultaneously recording it. When you press your fob button to lock or unlock your car, the attacker blocks the signal, making you think it didn’t work. You press the button again, generating a second code, which is also recorded. The attacker then uses the first recorded code to unlock your car, while still retaining the second code for future unauthorized access.
These attack methods highlight a critical aspect of modern vehicle security: the tools used to interact with and program key fobs. Automotive scan tools are essential for dealerships and auto repair shops. These tools are legitimately used for various functions, including diagnosing vehicle issues, reprogramming car computers, and, importantly, duplicating or programming new key fobs.
The same technology that enables legitimate key fob duplication can, unfortunately, be misused. While “automotive scan tool that can make duplicate fobs” are designed for authorized key replacement and maintenance, the underlying capabilities could potentially be exploited for nefarious purposes. This is why understanding these vulnerabilities and taking preventative measures is so important.
Protecting your vehicle from these types of attacks involves simple but effective strategies. For relay attacks, using a faraday cage pouch to store your key fob blocks radio signals, preventing attackers from capturing and relaying the signal. For rolljam attacks, manually verifying that your doors are locked by checking the handle after using the fob can help ensure the locking signal was not jammed.
While technology offers convenience, it’s crucial to be aware of the associated security risks. Understanding how automotive scan tools interact with key fobs and the potential for signal interception can empower vehicle owners to take proactive steps to protect their vehicles from theft. Staying informed and utilizing preventative measures are key to navigating the security landscape of modern automotive technology.