In today’s interconnected world, ensuring the security and efficiency of your network is paramount. Network scanning tools are indispensable for identifying vulnerabilities, optimizing performance, and maintaining a robust cybersecurity posture. As a content creator at vcdstool.com and an automotive repair expert, I understand the critical role of diagnostics and security in complex systems, whether it’s a vehicle’s network or a corporate IT infrastructure. This guide will explore the Best Network Scanning Tools available, helping you make informed decisions to protect your digital assets.
Why Network Scanning is Crucial
Network scanning is more than just a routine check; it’s a proactive measure to safeguard your operations. Here’s why it matters:
- Proactive Threat Detection: By identifying vulnerabilities before they are exploited, network scanning tools act as an early warning system against potential cyberattacks. This proactive approach is vital in preventing breaches and minimizing damage.
- Compliance and Security Standards: Many industries are subject to regulatory requirements and security standards such as GDPR, HIPAA, or PCI DSS. Regular network scanning helps ensure compliance, avoiding hefty fines and legal repercussions.
- Network Performance Optimization: Scanning tools not only detect security flaws but also monitor network performance. By identifying bottlenecks and inefficiencies, these tools help optimize network speed and reliability.
- Cost-Effective Security: Preventing security incidents and downtime is significantly more cost-effective than dealing with the aftermath of a cyberattack. Network scanning tools provide a cost-efficient way to maintain robust security and prevent expensive disruptions.
Best Network Scanning Tools: A Detailed Comparison
To help you navigate the landscape of network scanning tools, here is a comparison of some of the top solutions available in the market.
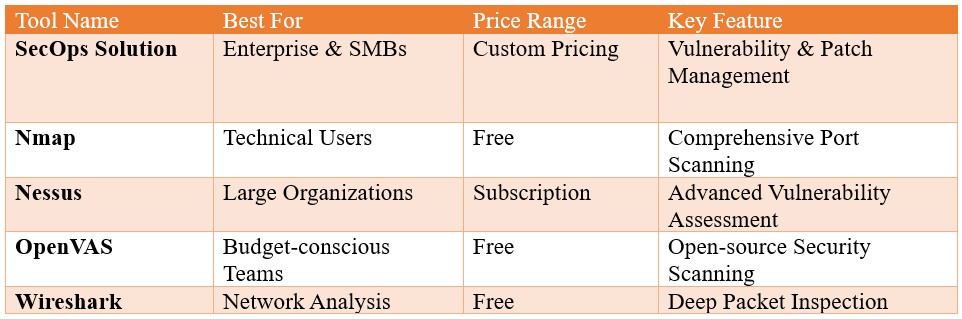
Network Scanning Tools Comparison Chart
Top Network Scanning Tools: In-Depth Reviews
Let’s delve deeper into each of these top network scanning tools, exploring their features, pricing, and ideal use cases.
1. SecOps Solution
SecOps Solution stands out as an advanced, agent-less vulnerability and patch management tool designed to quickly identify, prioritize, and remediate vulnerabilities across your entire IT infrastructure and applications. This comprehensive approach makes it a powerful asset for organizations looking to bolster their cybersecurity defenses.
Key Features:
- Comprehensive Patch Management: SecOps Solution offers robust patch management capabilities, supporting both agent-less and agent-based deployments. It provides real-time status updates for every patch at each stage, ensuring complete monitoring and control over the patching process.
- Customizable Patch Policies: Users can create custom patch policies tailored to their specific needs, along with predefined policies for immediate security enhancements. This flexibility ensures systems are always up-to-date with the necessary security patches.
- Pre-validated and Revertible Patches: The solution offers pre-validated and revertible patches, enabling one-click deployment with minimal operational disruption. This feature is crucial for maintaining system stability while applying critical updates.
- Driver and Offline Patching: SecOps Solution supports driver and offline patching, addressing vulnerabilities even in systems that are not constantly connected to the network.
- Advanced Vulnerability Management: Beyond patch management, it provides comprehensive vulnerability scanning, identifying potential weaknesses across your infrastructure.
Pricing: SecOps Solution offers subscription-based pricing models customized to fit the unique requirements and scale of each organization. For detailed pricing information, it’s best to contact their sales team directly.
Best For: SecOps Solution is ideally suited for organizations of all sizes that require a feature-rich and reliable vulnerability scanner and patch management solution. Its comprehensive features and flexible deployment options make it a top choice for businesses prioritizing robust security.
2. Nmap (Network Mapper)
Nmap, or Network Mapper, is a renowned open-source network scanner, widely acclaimed for its versatility and power in network exploration and security auditing. It is a go-to tool for security professionals worldwide.
Key Features:
- Versatile Scanning Capabilities: Nmap supports an extensive range of scan types, including host discovery, port scanning, version detection, and operating system fingerprinting. This breadth of functionality makes it incredibly versatile for various network assessments.
- Scripting Engine for Advanced Functionality: Nmap can be extended using its powerful scripting engine, allowing users to customize and automate complex scanning tasks. This feature enhances its capabilities for specific and advanced network analysis needs.
- Cross-Platform Compatibility: Nmap operates seamlessly across various operating systems, including Windows, Linux, and macOS, making it accessible to a wide range of users.
Pricing: Nmap is completely free and open-source, making it an exceptionally attractive option for individuals and organizations of all sizes, especially those with budget constraints.
Best For: Nmap is best suited for network administrators, cybersecurity professionals, and ethical hackers who need a reliable and adaptable tool for in-depth network scanning and security evaluations.
Drawback: Nmap’s command-line interface can be challenging for beginners, requiring a learning investment to fully leverage its extensive capabilities. However, the wealth of online resources and community support helps mitigate this issue.
3. Nessus
Nessus is a leading vulnerability scanner trusted by organizations globally to identify security vulnerabilities and compliance issues within their network infrastructure. It is known for its comprehensive vulnerability detection and reporting.
Key Features:
- Detailed Vulnerability Reporting: Nessus provides comprehensive reports on vulnerabilities, misconfigurations, and malware. These detailed reports enable organizations to prioritize risks effectively and streamline remediation efforts.
- Internal and External Scanning: Nessus supports both internal and external network scanning, offering a holistic view of an organization’s security posture. This dual capability ensures all potential entry points are assessed.
- Compliance Auditing: Nessus helps businesses meet compliance requirements by scanning against various standards and regulations, simplifying the process of maintaining regulatory adherence.
Pricing: Nessus offers different pricing tiers, including a free version for personal use. However, for professional and enterprise-level features, subscription fees apply. The cost scales with the level of features and support required.
Best For: Nessus is ideal for enterprises and large organizations that require robust vulnerability scanning, compliance management, and thorough risk assessment. Its comprehensive features are designed to meet the demands of complex network environments.
Drawback: The cost of the professional and enterprise editions can be a barrier for small businesses or individual users with limited budgets. However, the free version provides basic scanning capabilities for personal use.
4. OpenVAS (Open Vulnerability Assessment System)
OpenVAS, or Open Vulnerability Assessment System, is a free and open-source vulnerability scanner that offers comprehensive security assessments of networks. It is a community-driven project providing a robust alternative to commercial scanners.
Key Features:
- Continuously Updated Vulnerability Database: OpenVAS features a constantly updated database of network vulnerabilities, ensuring accurate and current scan results. This dynamic database is crucial for identifying the latest threats.
- Highly Customizable Scanning Engine: OpenVAS is highly customizable, allowing users to tailor scans to their specific needs and environments. This flexibility makes it suitable for diverse scanning requirements.
- Active Community Support: Being open-source, OpenVAS benefits from a vibrant community that contributes to its development and support. This community support ensures continuous improvement and readily available assistance.
Pricing: OpenVAS is completely free and open-source, making it accessible to all users without any licensing costs. This cost-effectiveness is a major advantage for budget-conscious organizations.
Best For: OpenVAS is well-suited for security-focused businesses, penetration testers, and IT professionals seeking a reliable and cost-free vulnerability assessment tool. It provides enterprise-grade features without the financial investment.
Drawback: OpenVAS may occasionally produce false positives, requiring manual verification of some scan results. Additionally, setup and configuration can be more technical compared to commercial solutions, potentially requiring more expertise.
5. Wireshark
Wireshark is a widely recognized and powerful network protocol analyzer that captures and inspects network packets in real-time. It is an essential tool for deep network analysis and troubleshooting.
Key Features:
- Real-time Packet Capture and Analysis: Wireshark captures network traffic in real-time, allowing for immediate analysis of network communications. This real-time capability is invaluable for diagnosing live network issues.
- Extensive Protocol Support: Wireshark supports a vast array of network protocols, making it versatile for analyzing different types of network traffic. Its broad protocol support ensures comprehensive network analysis.
- Detailed Packet Inspection: Wireshark allows for in-depth inspection of individual packets, providing granular details about network communications. This level of detail is crucial for advanced network troubleshooting and security analysis.
Pricing: Wireshark is an open-source tool and is freely available for download and use. Its free availability makes it accessible to anyone needing network protocol analysis capabilities.
Best For: Wireshark is the preferred tool for network engineers, security analysts, and anyone involved in network diagnostics, performance monitoring, and security investigation.
Drawback: Wireshark’s detailed packet-level analysis can be overwhelming for novice users. It is more suited for technically proficient individuals who understand network protocols and packet structures. The learning curve can be steep for beginners.
6. SolarWinds Network Performance Monitor (NPM)
SolarWinds Network Performance Monitor (NPM) is a comprehensive network monitoring and scanning tool that provides real-time insights into network performance and overall health. It is designed for proactive network management and optimization.
Key Features:
- Real-time Network Monitoring: SolarWinds NPM offers real-time monitoring of network performance metrics, providing up-to-the-minute visibility into network operations. This real-time monitoring is essential for proactive issue detection and resolution.
- Customizable Dashboards and Visualizations: The tool provides customizable dashboards and detailed visualizations, making it easy to understand network performance trends and identify potential problems. These visual aids enhance network management efficiency.
- Automated Device Discovery: NPM features automatic device discovery, ensuring new devices are seamlessly identified and added to the monitoring system. This automation simplifies network management and ensures comprehensive coverage.
Pricing: SolarWinds NPM is a commercial product with pricing based on the number of monitored elements. Various pricing plans are available to accommodate different network sizes and monitoring needs.
Best For: SolarWinds NPM is an excellent choice for medium to large enterprises that require extensive network monitoring, performance optimization, and proactive network management capabilities.
Drawback: The cost of SolarWinds NPM can be significant for small businesses and individual users. It is positioned as a premium solution with a price point reflecting its extensive features and enterprise-level capabilities.
7. Zenmap (Nmap GUI)
Zenmap is the official graphical user interface (GUI) for Nmap, designed to make Nmap’s powerful features more accessible and user-friendly. It simplifies network scanning for those who prefer a graphical interface.
Key Features:
- User-Friendly Graphical Interface: Zenmap provides a GUI for Nmap, making it easier to use Nmap’s features without needing to memorize command-line syntax. This graphical interface lowers the barrier to entry for Nmap.
- Interactive Result Visualization: Zenmap allows users to visualize and analyze Nmap scan results with various display filters and output formats. This visual representation aids in understanding and interpreting scan data.
- Profile Saving for Repeat Scans: Users can save scan profiles for frequently used scan configurations, simplifying repetitive tasks and ensuring consistent scans.
Pricing: As a GUI for Nmap, Zenmap is also free and open-source, inheriting Nmap’s cost-free accessibility.
Best For: Zenmap is ideal for users who prefer a GUI over the command line and want to effectively utilize Nmap’s powerful scanning capabilities without command-line complexity.
Drawback: Zenmap might have some limitations compared to using Nmap directly via the command line. Certain advanced functionalities and customizations may be less readily accessible through the GUI.
8. Acunetix Vulnerability Scanner
Acunetix Vulnerability Scanner is specifically designed for web application security, focusing on detecting and prioritizing vulnerabilities in web applications and APIs. It is a specialized tool for web security.
Key Features:
- Web Application and API Scanning: Acunetix specializes in scanning web applications and APIs for vulnerabilities like SQL injection, Cross-Site Scripting (XSS), and security misconfigurations.
- Comprehensive Vulnerability Detection: It scans for a wide range of web application vulnerabilities, ensuring thorough security assessments.
- Detailed Remediation Guidance: Acunetix provides detailed reports and remediation guidelines, helping developers and security teams address identified vulnerabilities effectively and efficiently.
Pricing: Acunetix offers various licensing options, including both on-premises and cloud-based plans, to suit different deployment preferences. Pricing varies based on the chosen plan and features.
Best For: Acunetix is an excellent choice for businesses and developers focused on securing web applications and APIs. It is particularly valuable for organizations with a strong web presence or those developing web-based services.
Drawback: Acunetix pricing can be a limiting factor for smaller organizations or individuals seeking a free or lower-cost solution. It is a premium tool focused on web application security.
9. Angry IP Scanner
Angry IP Scanner is a lightweight and cross-platform network scanner known for its speed and simplicity in detecting live hosts and open ports. It is a straightforward tool for basic network discovery.
Key Features:
- Fast IP Address and Port Scanning: Angry IP Scanner quickly scans IP addresses and ports, efficiently identifying live hosts and open services on a network.
- Cross-Platform Compatibility: It operates on Windows, Linux, and macOS, providing broad accessibility across different operating systems.
- Exportable Scan Results: Users can export scan results to various formats for further analysis or reporting, enhancing its utility for network documentation and auditing.
Pricing: Angry IP Scanner is an open-source tool and is free to use, making it a highly accessible option for basic network scanning needs.
Best For: Angry IP Scanner is best suited for small to medium-sized businesses and home users who need a simple, fast, and free network scanning solution for basic network discovery and troubleshooting.
Drawback: While effective for basic scanning, Angry IP Scanner lacks some of the advanced features found in more comprehensive network scanning tools. It is not designed for in-depth vulnerability analysis or advanced security assessments.
10. QualysGuard Vulnerability Management
QualysGuard Vulnerability Management is a cloud-based platform that offers continuous monitoring and assessment of network security. It provides a scalable and comprehensive solution for vulnerability management.
Key Features:
- Cloud-Based Vulnerability Management: QualysGuard is a fully cloud-based platform, offering ease of deployment and scalability without the need for on-premises infrastructure.
- Continuous Monitoring and Assessment: It provides continuous monitoring and assessment of network security, ensuring ongoing visibility into vulnerability status.
- Extensive Vulnerability Knowledge Base: QualysGuard includes a vast knowledge base of vulnerabilities and compliance standards, enhancing the accuracy and relevance of scan results.
Pricing: QualysGuard uses a subscription-based pricing model, with different tiers based on the number of assets to be scanned. This model allows organizations to scale their subscription according to their needs.
Best For: QualysGuard is ideal for enterprises and businesses that prioritize cloud-based solutions for vulnerability management and network scanning. Its scalability and comprehensive features make it suitable for large and distributed networks.
Drawback: The subscription-based pricing of QualysGuard can be relatively expensive for smaller organizations, especially those with limited budgets or smaller networks.
Choosing the Right Network Scanning Tool
Selecting the best network scanning tool depends on various factors specific to your organization’s needs and resources.
Key Considerations:
-
Organization Size:
- Enterprise Requirements: Large enterprises typically need comprehensive, scalable solutions like SecOps Solution, Nessus, or QualysGuard, which offer advanced features and robust support.
- SMB Needs: Small to medium-sized businesses might find open-source tools like Nmap, OpenVAS, or simpler tools like Angry IP Scanner sufficient, especially if budget is a constraint.
- Resource Availability: Consider the available IT staff and their expertise. Complex tools may require dedicated personnel, while user-friendly tools can be managed by a broader team.
-
Technical Expertise:
- Team Capabilities: Evaluate your team’s technical skills. Command-line tools like Nmap require more technical proficiency, while GUI-based tools like Zenmap or commercial solutions with user-friendly interfaces may be easier to manage.
- Learning Curve: Some tools have a steeper learning curve than others. Consider the time and resources needed for training and onboarding.
- Support Requirements: Determine the level of support you require. Commercial tools often come with dedicated support, while open-source tools rely on community support.
-
Budget Constraints:
- Free vs. Paid Options: Open-source tools like Nmap, OpenVAS, Wireshark, Zenmap, and Angry IP Scanner are free, making them attractive for organizations with limited budgets. Commercial tools offer more features and support but come at a cost.
- ROI Considerations: Evaluate the return on investment for paid tools. Consider the potential cost savings from preventing security breaches and optimizing network performance.
- Scalability Costs: Understand how pricing scales as your network grows. Some tools may become expensive as you add more devices or require more features.
Expert Tips for Effective Network Scanning
To maximize the benefits of network scanning, consider these best practices:
Best Practices for Network Scanning:
-
Establish a Regular Scanning Schedule:
- Implement daily automated scans for critical systems to continuously monitor for new vulnerabilities.
- Conduct weekly comprehensive scans of the entire network to ensure broad coverage and detect less immediate threats.
-
Ensure Comprehensive Coverage:
- Scan all parts of your network, including servers, workstations, and network devices.
- Include both internal and external scans to assess your security posture from all angles.
-
Implement False Positive Management:
- Develop a process for verifying scan results to differentiate between true vulnerabilities and false positives.
- Fine-tune scanning tools to reduce false positives and improve accuracy.
-
Develop a Robust Response Planning:
- Create a clear plan for responding to identified vulnerabilities, including patching, mitigation, and remediation steps.
- Prioritize vulnerabilities based on severity and potential impact on your organization.
-
Invest in Team Training:
- Provide adequate training for your IT and security teams on how to use network scanning tools effectively.
- Ensure they understand how to interpret scan results and implement appropriate responses.
FAQ: Network Scanning Tools
What is the best free network scanning tool?
Nmap is widely regarded as the best free network scanning tool. It offers a comprehensive suite of features comparable to professional-grade tools, making it an excellent choice for users seeking powerful capabilities without cost.
How often should I scan my network for vulnerabilities?
For optimal security, it is recommended to perform daily automated scans for critical systems and weekly comprehensive scans for the entire network. This frequency ensures timely detection and mitigation of vulnerabilities.
Can network scanning tools negatively impact network performance?
Modern network scanning tools, especially solutions like SecOps Solution, are designed to minimize network impact. They use efficient scanning techniques to ensure comprehensive coverage without causing significant performance degradation. However, it’s important to configure scans appropriately to avoid overwhelming network resources, particularly during peak usage times.
Conclusion: Choosing the Best Network Scanning Tool for Your Needs
Selecting the right network scanning tool is a critical decision for maintaining a strong security posture and optimizing network performance. While free tools like Nmap offer exceptional capabilities, enterprise-grade solutions such as SecOps Solution provide more comprehensive coverage and advanced features tailored for complex organizational needs. By carefully considering your specific requirements, budget, and technical expertise, you can choose the best network scanning tool to protect your network effectively in 2024 and beyond.
SecOps Solution is a Full-stack Patch and Vulnerability Management Platform designed to help organizations efficiently identify, prioritize, and remediate security vulnerabilities and misconfigurations in seconds.
To discover how SecOps Solution can enhance your network security, get in touch today.
