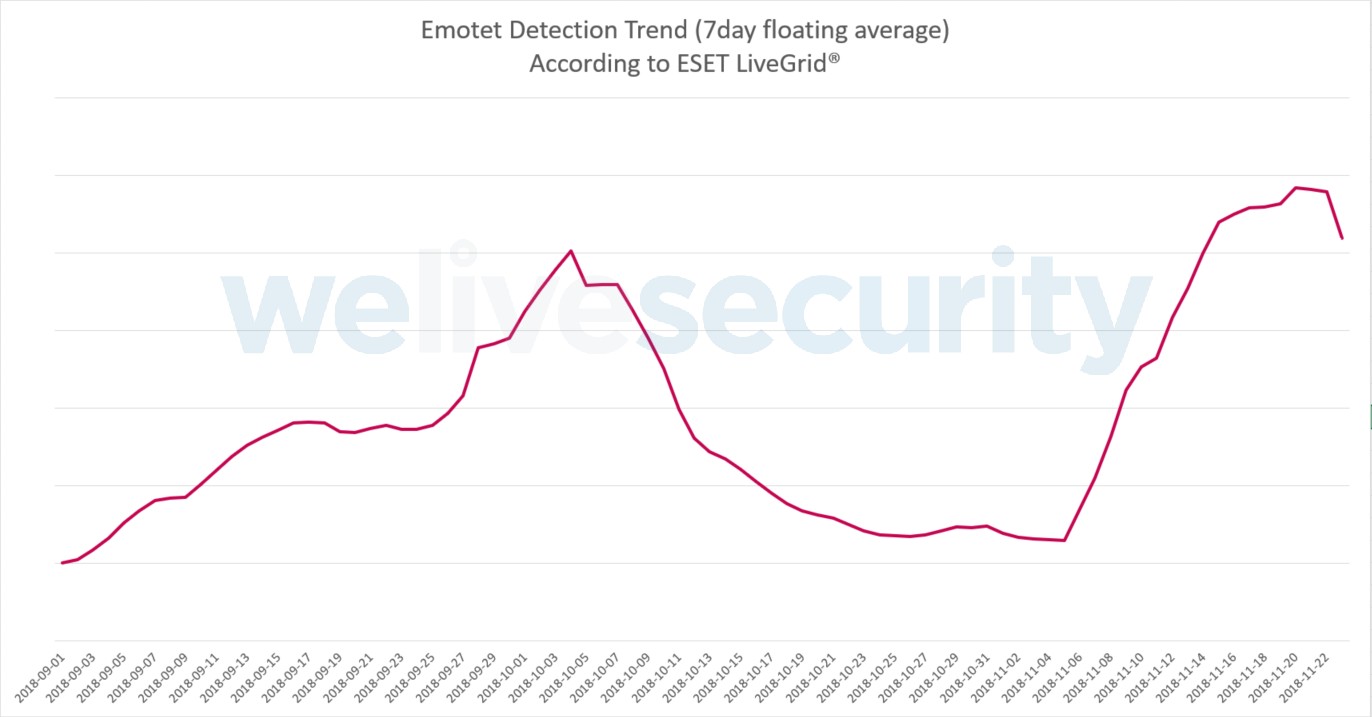
As Black Friday and Cyber Monday approached in 2018, online shoppers weren’t the only ones gearing up for a busy season. Cybercriminals, particularly the operators behind the Emotet malware, were also preparing to capitalize on the increased online activity. ESET researchers detected a significant surge in Emotet spam campaigns coinciding with the Black Friday shopping rush, revealing a shift in tactics and a clear focus on exploiting holiday season vulnerabilities.
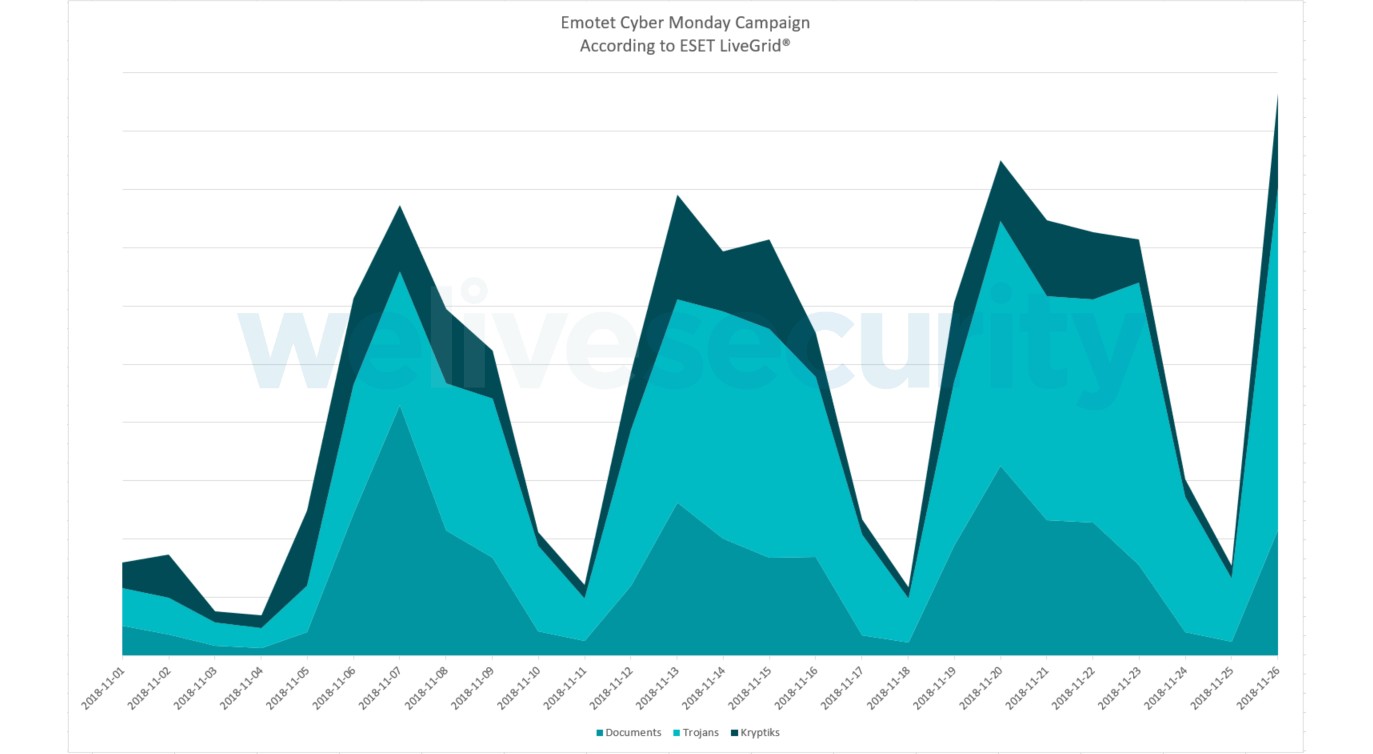
Emotet, known for its widespread and impactful spam operations, launched a massive campaign taking advantage of the heightened email traffic surrounding Black Friday. The malware, typically spread through malicious attachments or links in spam emails, adopted a new technique. Instead of the usual DOC or PDF files, this campaign utilized XML files disguised with a misleading .doc extension. This subtle change likely aimed to bypass some security filters and trick users into opening the infected files.
These seemingly innocuous XML.doc attachments were the gateway to a range of harmful payloads. Emotet served as a delivery mechanism for various banking trojans, including Ursnif, TrickBot, and IcedId, with IcedId being the most prevalent. IcedId, in turn, often downloaded Azorult (detected by ESET as Win32/PSW.Delf.OSF), a notorious information stealer capable of pilfering passwords, credit card details, and cryptocurrency wallet access. TrickBot also expanded its reach, adding more UK and German banks to its target list, aligning with the English and German language themes observed in the spam email subjects and content, as previously highlighted by ESET.
The geographical distribution of this Black Friday Emotet campaign revealed a strong concentration in Latin America. Mexico, Ecuador, and Argentina topped the list of affected countries, experiencing hundreds of thousands of detections. The United States also ranked among the top five targeted nations, with the UK and South Africa also featuring in the top ten, indicating a broad and global impact of this holiday-themed cyber threat.
To help security professionals and system administrators identify and mitigate these threats, ESET researchers provided a list of Indicators of Compromise (IoCs) associated with the Emotet payloads used in this Black Friday campaign:
Indicators of Compromise (IoCs)
Emotet payloads
| SHA-1 Hash | Malware Family |
|---|---|
| 02b614654f27b67aa3efcf94dcad3875696315ab | TrickBot |
| cda88d48c26afd383a996fe2c0ef87514389c189 | IcedId |
| 0977692f1accd541dd7c23eb76f5272d4321d868 | IcedId |
| 3b000e5e6de4d91443563792d69caac95b1038f0 | TrickBot |
| 086bc2718521e6e4aead498b57d20d3b2ec812e9 | Ursnif |
| 202604e7dc6c29ae75ad9f707ebbc8bf5367a631 | TrickBot |
| 844e6a4c31ae473702781603d8cdd5f9b3aa63c5 | IcedId |
| 6481172f509f80ee059b7dc20a2bf995b38aafd2 | TrickBot |
| 9e8972dd0130481e1e42504c7fdda1ffa353e473 | IcedId |
| db82d173e5afe207eeebacb65bd76cdbb67b5955 | TrickBot |
| 350e6b2f5728a17578923ab5a7640e0b57101447 | IcedId |
| 638d2c5b3331cdc2267d1036a9ff8e2efd08b316 | IcedId |
| 3c3624bfd75285c0d69f4867cc2adc5fb538888f | IcedId |
| f75e600d29189065208d116602a2a6fccebf1927 | IcedId |
| e38d371e17eeb34b6f94d05a208d0eb8a3b88f37 | IcedId |
| 765c272f914e85332d6e6a16e62645764f417379 | TrickBot |
| ea24d6f25077f8a82c5a09e0b22040293b8a50d6 | IcedId |
| d5d1c5c1af7c4e0346367cc1fdef0e788f25f1a6 | IcedId |


PSW.Delf.OSF – AZORult
| SHA-1 Hash | Malware Detection |
|---|---|
| 3e435f2d58616e28972ad2c422f54e27680fb452 | Win32/GenKryptik.CRSJ trojan |
| f17a455dc012027486ad39c134984cadbe7e31ef | Win32/Kryptik.GMUX trojan |
| 00169e624343cfda397d7a6df77b3e776b54e5ec | Win32/Kryptik.GNEF |
Staying informed about the latest cyber threats is crucial, especially during peak online shopping seasons. Subscribing to newsletters and security updates from reputable sources like ESET can provide valuable insights and proactive protection against evolving malware campaigns.
Related Articles
[ESET Research
DeceptiveDevelopment targets freelance developers
ESET Research
DeceptiveDevelopment targets freelance developers](/en/eset-research/deceptivedevelopment-targets-freelance-developers/ “DeceptiveDevelopment targets freelance developers”)
[ESET Research
PlushDaemon compromises supply chain of Korean VPN service
ESET Research
PlushDaemon compromises supply chain of Korean VPN service](/en/eset-research/plushdaemon-compromises-supply-chain-korean-vpn-service/ “PlushDaemon compromises supply chain of Korean VPN service”)
[ESET Research
Under the cloak of UEFI Secure Boot: Introducing CVE-2024-7344
ESET Research
Under the cloak of UEFI Secure Boot: Introducing CVE-2024-7344](/en/eset-research/under-cloak-uefi-secure-boot-introducing-cve-2024-7344/ “Under the cloak of UEFI Secure Boot: Introducing CVE-2024-7344”)


