In today’s rapidly evolving digital landscape, ensuring software security is paramount. Vulnerabilities in software can lead to significant risks, from data breaches to system compromises. This is where Cve Scan Tools become indispensable. These tools are designed to identify known vulnerabilities in your software by leveraging databases of Common Vulnerabilities and Exposures (CVEs). Among the array of options available, the CVE Binary Tool stands out as a robust, free, and open-source solution. This guide provides a comprehensive overview of CVE scan tools, with a deep dive into how to effectively utilize the CVE Binary Tool to enhance your software security posture.
CVE Binary Tool is not just another vulnerability scanner; it’s a versatile instrument for developers, security professionals, and organizations seeking to proactively manage software vulnerabilities. By understanding its capabilities and integrating it into your workflow, you can gain early warnings about potential security issues in your software supply chain and build more resilient applications.
Understanding CVE Scan Tools and the CVE Binary Tool
What is a CVE Scan Tool?
A CVE scan tool, at its core, is a security application designed to scan software components – binaries, libraries, and dependencies – and cross-reference them against databases of known vulnerabilities, specifically the Common Vulnerabilities and Exposures (CVE) list. This list is maintained by MITRE Corporation and serves as a dictionary of publicly known information security vulnerabilities and exposures.
The primary function of a CVE scan tool is to automate the process of vulnerability identification. Instead of manually checking each software component against vulnerability databases, these tools perform scans and generate reports detailing potential CVE matches. This allows security teams and developers to quickly understand their software’s vulnerability landscape and prioritize remediation efforts.
Introducing CVE Binary Tool: An Open-Source Solution
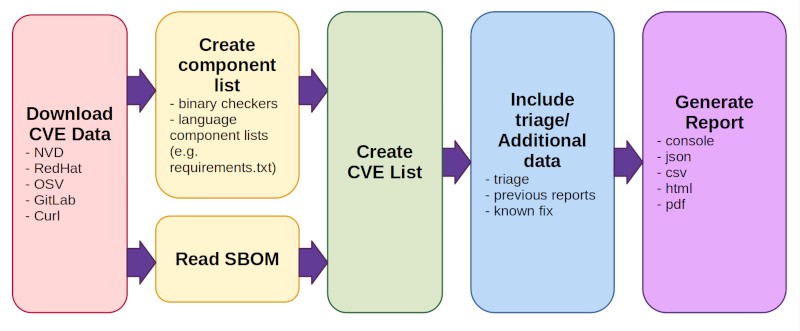
The CVE Binary Tool, developed and maintained by Intel, is a powerful, open-source cve scan tool designed to help you discover known vulnerabilities in your software. It leverages data from various reputable sources, including:
- National Vulnerability Database (NVD): The primary source for CVE information.
- Red Hat Security Data: Vulnerability data specific to Red Hat products.
- Open Source Vulnerability Database (OSV): A comprehensive database for open-source vulnerabilities.
- GitLab Advisory Database (GAD): Vulnerability advisories for GitLab and related projects.
- Curl Vulnerability Data: Vulnerability information specific to the curl project.
Unlike some commercial vulnerability scan tools, CVE Binary Tool is completely free to use and modify, fostering transparency and community contribution. It is designed to be integrated into continuous integration (CI) systems, enabling regular and automated vulnerability scanning as part of the software development lifecycle.
Key Features and Benefits of CVE Binary Tool
CVE Binary Tool offers a range of features that make it an effective cve scan tool:
- Binary Scanning: It can scan binary files and directories to identify potential software packages and components embedded within. This is crucial for understanding the composition of your software, especially when dealing with compiled applications.
- SBOM Scanning: The tool can analyze Software Bill of Materials (SBOMs) in various formats (SPDX, CycloneDX, SWID). SBOMs provide a detailed inventory of software components, and CVE Binary Tool can quickly check these components for known vulnerabilities.
- SBOM Generation: Beyond scanning, CVE Binary Tool can also generate SBOMs, aiding in software transparency and supply chain security.
- VEX Support: It supports the Vulnerability Exploitability eXchange (VEX) format for managing and triaging vulnerabilities. You can import VEX files to incorporate triage data and export VEX files to share vulnerability assessment results.
- Multiple Output Formats: Reports can be generated in various formats including console, CSV, JSON, HTML, and PDF, catering to different reporting needs.
- Offline Operation: CVE Binary Tool can operate offline, making it suitable for secure environments without direct internet access.
- Extensive Checker Library: It boasts a large library of binary checkers (over 380) to detect a wide range of common open-source components.
- Language-Specific Checkers: Supports scanning of language-specific package manifests (e.g.,
requirements.txtfor Python,pom.xmlfor Java) for more accurate dependency analysis. - Continuous Integration Ready: Designed for seamless integration into CI/CD pipelines through command-line interface and a dedicated GitHub Action.
By leveraging these features, CVE Binary Tool empowers users to proactively identify and manage vulnerabilities, contributing to a more secure software ecosystem.
Getting Started with CVE Binary Tool
Installation Guide
Installing CVE Binary Tool is straightforward using pip, the Python package installer. Open your terminal or command prompt and run the following command:
pip install cve-bin-toolThis command will download and install CVE Binary Tool along with its Python dependencies.
For users who wish to work with the latest development version or contribute to the project, you can install it directly from the GitHub repository:
pip install --user -e .This command installs CVE Binary Tool in editable mode from a local directory, which is useful for development and testing. Refer to the Contributor Documentation for detailed setup instructions for local development.
System Requirements
CVE Binary Tool is primarily written in Python and is cross-platform, running on Linux, macOS, and Windows. While pip handles the Python requirements, certain extraction functionalities rely on system libraries.
Recommended utilities for Linux:
filestringstarunziprpm2cpiocpioarcabextract
Most of these utilities are commonly pre-installed on Linux distributions. However, you might need to install cabextract and rpm2cpio explicitly depending on your system and the archive formats you intend to scan.
Recommended utilities for Windows:
ar7z(7-Zip)Expand(built-in)pdftotext(for testing, optional for basic usage)
Windows users might need to install ar (from MinGW or similar) and 7-Zip. A specific fork of 7-Zip, 7-zip-zstd, is recommended for handling zstd compressed files. Windows build tools might be required if you encounter errors during pip installation related to building libraries.
Initial Setup and Data Download
Upon the first run, and subsequently once a day by default, CVE Binary Tool downloads vulnerability data from configured sources. This initial download can take some time depending on your internet connection speed and the size of the vulnerability databases.
By default, CVE Binary Tool uses a mirror for NVD data (https://cveb.in/) due to reliability concerns with the official NVD API. If you prefer to use the official NVD API directly, you need to provide an NVD API key using the --nvd-api-key option.
For users in environments with restricted internet access or for consistent offline operation, you can configure CVE Binary Tool for offline mode. This involves manually downloading the vulnerability databases and configuring the tool to use local data. Consult the offline how-to guide for detailed instructions on setting up the database for offline use.
Unleashing the Power of CVE Binary Tool: Usage and Applications
CVE Binary Tool provides a versatile command-line interface for various scanning and reporting tasks. Here are some of the most common and powerful usage scenarios.
Binary Scanning for Vulnerability Detection
The most fundamental use case is scanning directories or individual files for known vulnerabilities using binary checkers. To perform a basic binary scan, navigate to your terminal and run the command:
cve-bin-tool <directory/file>Replace <directory/file> with the path to the directory or file you want to scan. CVE Binary Tool will analyze the provided target, identify potential software components using its binary checkers and language-specific checkers, and report any detected vulnerabilities.
This mode is particularly useful for:
- Analyzing compiled applications and firmware images.
- Scanning file systems or directories containing software installations.
- Quickly assessing the vulnerability posture of a software release.
For example, to scan a directory named application_binaries, you would use:
cve-bin-tool application_binariesSBOM Scanning: Analyzing Software Bills of Materials
Software Bill of Materials (SBOMs) are becoming increasingly important for software supply chain transparency and security. CVE Binary Tool excels at scanning SBOM files for vulnerabilities. To scan an SBOM, use the --sbom option along with --sbom-file:
cve-bin-tool --sbom <sbom_filetype> --sbom-file <sbom_filename>Replace <sbom_filetype> with the SBOM format (spdx, cyclonedx, or swid) and <sbom_filename> with the path to your SBOM file.
This functionality is crucial for:
- Organizations receiving software with SBOMs and needing to quickly assess the security risk.
- Validating the security of software components listed in an SBOM.
- Integrating SBOM scanning into security audits and compliance processes.
For instance, to scan a CycloneDX SBOM file named my_sbom.json, the command would be:
cve-bin-tool --sbom cyclonedx --sbom-file my_sbom.jsonGenerating SBOMs for Transparency
CVE Binary Tool can also generate SBOMs from a scan. This is valuable for creating transparency in your own software products and providing SBOMs to customers or for internal documentation. Use the --sbom-type, --sbom-format, and --sbom-output options:
cve-bin-tool --sbom-type <sbom_type> --sbom-format <sbom-format> --sbom-output <sbom_filename> <scan_target>Replace <sbom_type> with the desired SBOM type (spdx or cyclonedx), <sbom-format> with the format (tag, json, or yaml), <sbom_filename> with the output filename, and <scan_target> with the directory or file to scan for component detection.
Generating SBOMs is beneficial for:
- Software vendors aiming to provide transparency about their software composition.
- Organizations implementing SBOM generation as part of their software development best practices.
- Creating documentation for internal security audits and compliance.
To generate an SPDX SBOM in JSON format named output_sbom.json from scanning the application_code directory, use:
cve-bin-tool --sbom-type spdx --sbom-format json --sbom-output output_sbom.json application_codeVEX Generation and Vulnerability Triage
CVE Binary Tool supports the Vulnerability Exploitability eXchange (VEX) format for managing vulnerability triage information. You can generate VEX documents using the --vex-type and --vex-output options:
cve-bin-tool --vex-type <vex_type> --vex-output <vex_filename> <scan_target>Replace <vex_type> with the VEX format (cyclonedx, csaf, or openvex), <vex_filename> with the output VEX filename, and <scan_target> with the scan target.
VEX files are used to communicate the exploitability and impact of vulnerabilities within a specific product context. You can also import existing VEX files using the --vex-file option to incorporate triage data into your scans, saving time and ensuring consistency across scans.
Generating VEX documents is useful for:
- Providing vulnerability assessment and triage information to stakeholders.
- Documenting decisions about vulnerability remediation (or non-remediation).
- Sharing triage data across different teams and tools.
To generate a CycloneDX VEX file named triage.json after scanning the firmware directory:
cve-bin-tool --vex-type cyclonedx --vex-output triage.json firmwareSubsequently, to use this triage file in future scans:
cve-bin-tool --vex-file triage.json firmwareOffline Scanning for Secure Environments
For environments with restricted or no internet connectivity, CVE Binary Tool offers an --offline mode. Using the --offline flag prevents the tool from attempting to download vulnerability data or check for updates during scans.
cve-bin-tool --offline <scan_target>Before using offline mode, ensure you have already downloaded and set up the vulnerability databases. Refer to the offline how-to guide for detailed instructions on database setup for offline operation.
Offline scanning is essential for:
- Security audits in air-gapped networks or highly secure environments.
- Consistent and predictable scan results, independent of internet availability.
- Organizations with strict data security policies that limit external network access.
Integration with GitHub Actions for CI/CD
CVE Binary Tool provides an official GitHub Action for seamless integration into your CI/CD pipelines. This action allows you to automate vulnerability scans as part of your development workflow.
You can find the GitHub Action in the GitHub Marketplace and detailed usage instructions in the CVE Binary Tool GitHub Action repository.
Integrating CVE Binary Tool into GitHub Actions enables:
- Automated vulnerability checks on every code commit or pull request.
- Early detection of vulnerabilities in the development lifecycle.
- Security reporting directly within the GitHub Security tab (for supported repositories).
- Enforcing security policies and preventing vulnerable code from being deployed.
Alternatively, you can use the example GitHub Action configuration provided in the CVE Binary Tool repository to customize your CI workflow and generate reports in various formats for evidence lockers or teams without GitHub Security tab access.
Advanced Features and Customization
CVE Binary Tool offers a range of advanced options and customization possibilities to tailor its behavior to specific needs.
Output Options and Reporting Formats
By default, CVE Binary Tool provides console-based output. However, you can specify different output formats and filenames using the --format and --output-file options.
cve-bin-tool --format <format> --output-file <output_filename> <scan_target>Valid formats include:
console(default)csvjsonjson2(more detailed JSON format)htmlpdf(requiresreportlablibrary)
You can specify multiple output formats by separating them with commas (e.g., --format csv,json,html).
For PDF report generation, you need to install the reportlab library separately:
pip install cve-bin-tool[PDF]or
pip install --upgrade reportlabOutput customization is valuable for:
- Generating reports in formats suitable for different audiences (e.g., executive summaries in PDF, detailed data in JSON).
- Integrating scan results into other security tools or dashboards.
- Archiving reports in various formats for compliance and audit trails.
Configuration and Command-Line Interface
CVE Binary Tool is highly configurable through command-line options and configuration files. You can use the --config option to provide a configuration file in YAML or TOML format to manage various settings. Command-line arguments override settings specified in the configuration file.
Configuration files allow you to:
- Manage data source settings and API keys.
- Define exclude paths and skip specific checkers.
- Customize output formats and reporting options.
- Set severity thresholds and filtering criteria.
Refer to the sample configuration files in the test/config directory of the CVE Binary Tool repository for examples and available configuration parameters.
Auto-Detection Capabilities: Binary and Language Checkers
CVE Binary Tool’s strength lies in its auto-detection capabilities, utilizing both binary checkers and language-specific checkers.
Binary Checkers: These checkers are designed to identify specific software components within binary files based on signatures and version patterns. The tool includes a vast library of over 380 binary checkers, covering a wide range of common libraries and applications.
Language-Specific Checkers: These checkers analyze language-specific package manifests and dependency files to identify components and their versions. Supported languages include: Dart, Go, Java, JavaScript, Rust, Ruby, R, Swift, Python, and Perl.
These auto-detection mechanisms enable CVE Binary Tool to effectively identify components even without explicit SBOMs, making it a powerful tool for analyzing software of unknown or partially known composition.
Supported Archive Formats for Deep Scanning
CVE Binary Tool’s auto-extractor can unpack and scan components within various archive formats. Supported archive formats include:
zip(.zip, .exe, .jar, .msi, .egg, .whl, .war, .ear).aartar(.tar, .tgz, .tar.gz, .tar.xz, .tar.bz2)deb(.deb, .ipk)rpm(.rpm)cab(.cab)apk(.apk)zst(.zst)pkg(.pkg)
This archive extraction capability allows CVE Binary Tool to perform deep scans, analyzing components nested within archives and providing a more comprehensive vulnerability assessment. The --extract option can be used to explicitly enable auto-extraction, although it is enabled by default.
Maximizing Efficiency and Accuracy with CVE Scan Tools
To leverage CVE scan tools like CVE Binary Tool effectively, it’s important to understand best practices, limitations, and how to interpret and act upon scan results.
Best Practices for Using CVE Scan Tools
- Integrate into CI/CD: Automate CVE scans as part of your continuous integration and continuous delivery pipelines to catch vulnerabilities early in the development cycle.
- Regularly Update Databases: Ensure that your CVE database is updated regularly to include the latest vulnerability information. CVE Binary Tool automatically updates daily by default, but you can adjust the update schedule.
- Use SBOMs When Available: Utilize SBOMs for scanning whenever possible to provide a precise inventory of software components and improve scan accuracy.
- Implement VEX for Triage: Use VEX files to manage and document vulnerability triage decisions, improving efficiency and consistency across scans.
- Customize Configuration: Tailor CVE Binary Tool’s configuration to your specific needs, including output formats, severity thresholds, and excluded paths.
- Combine with Other Security Tools: CVE scan tools are part of a broader security toolkit. Integrate them with other security testing methods like static analysis, dynamic analysis, and penetration testing for a comprehensive security approach.
- Prioritize Remediation: Focus on remediating critical and high-severity vulnerabilities first, based on CVSS scores and exploitability metrics.
- Educate Developers: Train developers on secure coding practices and the importance of addressing vulnerabilities identified by CVE scan tools.
Understanding Limitations and Triage
CVE scan tools, including CVE Binary Tool, are valuable but not infallible. It’s crucial to understand their limitations:
- Signature-Based Detection: They primarily rely on signatures and version numbers, meaning they may not detect backported fixes or obfuscated components.
- False Positives: Scans can sometimes produce false positives, reporting vulnerabilities that are not actually exploitable in the specific context of your software.
- Incomplete Vulnerability Coverage: No single CVE database is exhaustive. CVE Binary Tool relies on several reputable sources, but there might be vulnerabilities not yet included in these databases.
- Exploitability Assessment: CVE scan tools generally do not assess exploitability. They identify potential vulnerabilities but don’t confirm if they are actually exploitable in a given system.
Triage is the process of reviewing and validating scan results, addressing false positives, and prioritizing remediation efforts. VEX files are designed to support effective triage workflows. When triaging vulnerabilities, consider:
- Context: Is the vulnerable component actually used in your software and in an exploitable way?
- Severity and Exploitability: Assess the CVSS score, exploitability metrics (like EPSS), and potential impact of the vulnerability.
- Mitigation Strategies: Are there configuration changes or usage patterns that mitigate the risk even if a patch is not immediately available?
- Available Fixes: Check for patches or updated versions of the vulnerable component.
Community and Support: Feedback and Contributions
CVE Binary Tool is an open-source project that thrives on community involvement. You can contribute to the project and get support through various channels:
- GitHub Issues: Report bugs, suggest feature requests, and ask questions via GitHub issues in the CVE Binary Tool repository.
- Pull Requests: Contribute code improvements, new checkers, or documentation updates via pull requests.
- Gitter Community: Engage with the community and developers in the Gitter chat room.
- Security Issue Reporting: Report security vulnerabilities in the tool itself to Intel’s security incident response team via https://intel.com/security.
By participating in the CVE Binary Tool community, you can help improve the tool, share your experiences, and contribute to a more secure software ecosystem.
Conclusion: Enhancing Software Security with CVE Scan Tools
CVE scan tools are essential instruments in the modern software security landscape. They provide automated vulnerability detection, enabling organizations and developers to proactively manage security risks. CVE Binary Tool, as a free, open-source, and feature-rich cve scan tool, offers a compelling solution for vulnerability scanning, SBOM analysis, and VEX-based triage.
By integrating CVE Binary Tool into your development workflows, understanding its capabilities and limitations, and actively participating in the community, you can significantly enhance your software security posture and build more resilient applications. Embrace the power of cve scan tools and make vulnerability detection an integral part of your software development lifecycle.