Port scanning is a foundational technique in network security, used to probe network ports for their status: open, closed, or filtered. For network administrators and security professionals, port scanners are indispensable for diagnosing network issues and verifying security policies. Conversely, malicious actors utilize them to pinpoint vulnerabilities and potential entry points into systems, identifying running services like firewalls, proxy servers, or VPN servers. This detailed guide will explore the mechanics of port scanners, their operational techniques, and a range of tools available for this critical task.
Understanding How a Port Scanner Operates
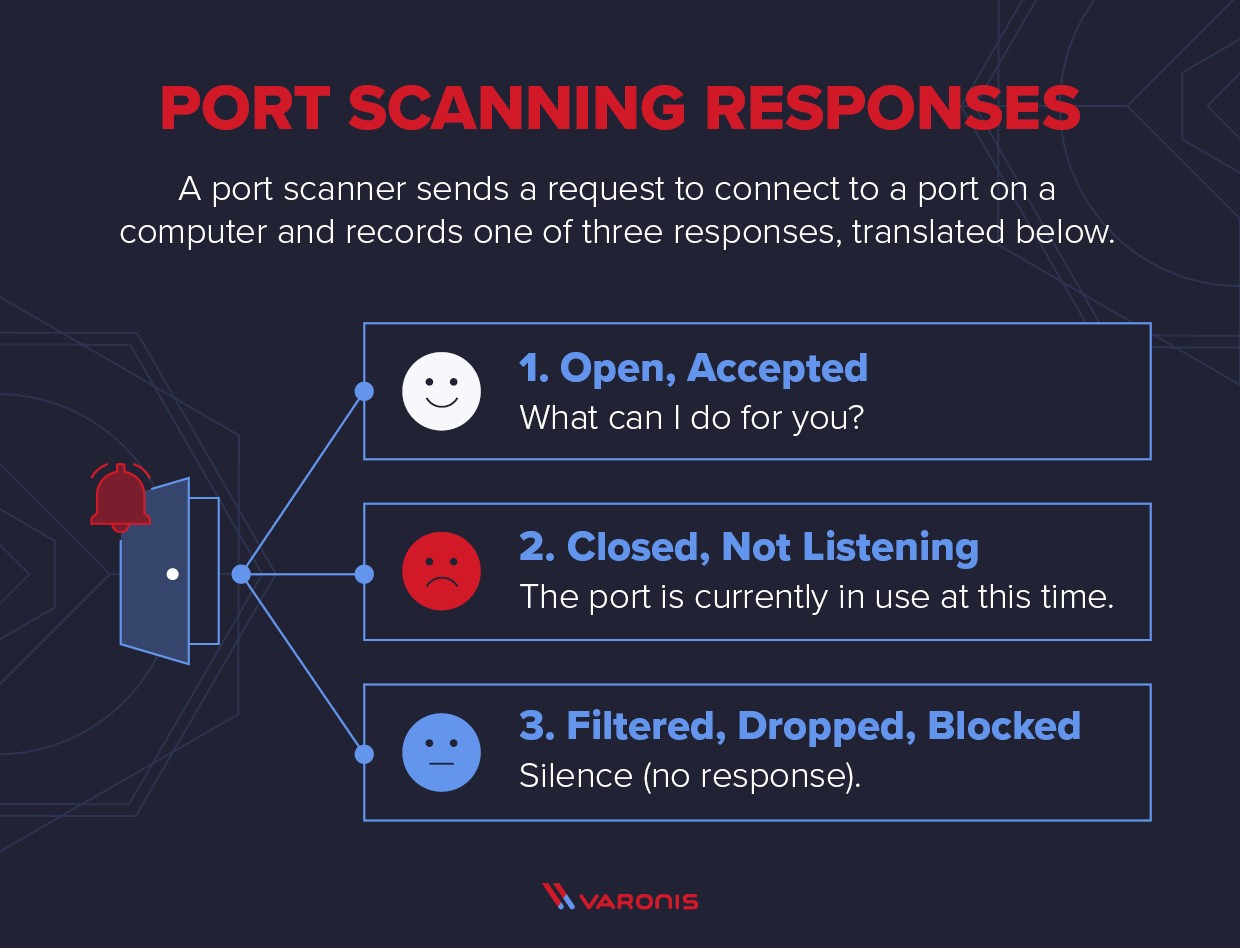
The core function of a port scanner involves sending network requests to specific TCP or UDP ports on a target computer and meticulously recording the responses received.
Imagine needing to verify if a web server is functioning correctly. A port scan directed at port 80 of that server would check if the port is open and actively listening for connections. The status gleaned from such scans is crucial for network engineers troubleshooting connectivity problems or for security experts assessing potential vulnerabilities. Attackers leverage this same information to locate open ports that could be exploited to infiltrate networks.
Delving into Network Ports
A port is essentially a virtual endpoint where network communications begin and terminate. To grasp this fully, some foundational knowledge is necessary. Each computer possesses 65,536 TCP ports and an equal number of UDP ports, totaling 131,072 network ports.
Network communication relies on two primary port types:
- TCP (Transmission Control Protocol): This protocol is connection-oriented, ensuring reliable data transmission.
- UDP (User Datagram Protocol): This protocol is connectionless and faster, prioritizing speed over reliability.
Every computer on a network is assigned a unique Internet Protocol (IP) address, which serves as its network identifier for packet delivery. When data packets are sent to an IP address, the computer uses port numbers to direct the traffic to the correct service or application. Each service running on a computer must “listen” on a designated port to receive incoming requests.
The ports numbered 0 through 1023 are designated as “well-known ports.” These are reserved by the Internet Assigned Numbers Authority (IANA) for standard applications. Examples include FTP (port 21), HTTP (port 80), and SSH (port 22), ensuring standardization across networks.
TCP ports 1024 to 49151 are available for general use by various services and applications. While they can be registered with IANA, this is not mandatory, classifying them as “semi-reserved.” Ports 49152 through 65535 are dynamic or private ports, freely available for any purpose.
Port Scanning Fundamentals
A port scan initiates by sending a network packet, either TCP or UDP, to a target port to determine its current state. The responses fall into three primary categories:
- Open (Accepted): Indicates that the port is active and listening for connections. The target system responds, acknowledging the connection attempt and signaling readiness to communicate.
- Closed (Not Listening): Signifies that the port is accessible, but no application is currently listening on it. The target system responds to indicate that the port is closed and unavailable.
- Filtered (Dropped, Blocked): Implies that a firewall or other network security measure is blocking communication to the port. The target system does not respond, suggesting that traffic is being filtered before reaching the port.
Port scanning typically occurs in the early stages of a cyber attack, specifically during the reconnaissance and intrusion phases of the cyber kill chain. Attackers employ port scans to identify potential targets with open, vulnerable ports that can be exploited for unauthorized access, command and control, data exfiltration, or to discover applications running on a system for vulnerability exploitation.
Port Scanning Techniques Explained
Nmap, short for Network Mapper, is a widely recognized and powerful open-source port scanning tool. It offers a diverse array of port scanning techniques tailored for different network assessment scenarios.
Ping Scan
Ping scans represent the most basic form of network reconnaissance. They operate using Internet Control Message Protocol (ICMP) echo requests, commonly known as “pings.” The objective is to identify active hosts within a network by sending ICMP echo requests and analyzing the responses. Receiving an ICMP echo reply confirms that a target host is online and reachable. While technically not a port scanning technique, ping scans are often the initial step in network probing, providing a preliminary assessment of network topology before more detailed port scans are conducted.
Network administrators often disable ICMP responses on firewalls or routers for external traffic as a security measure, while keeping it active within internal networks for troubleshooting. Disabling ping makes network discovery more challenging for attackers but can also complicate internal network diagnostics.
TCP Half-Open Scan (SYN Scan)
The TCP half-open scan, also known as SYN scan, is a prevalent and stealthy method for identifying open ports. It is favored for its speed and reduced detectability compared to full TCP connect scans.
In a standard TCP communication, a three-way handshake establishes a connection: SYN (synchronize), SYN-ACK (synchronize-acknowledge), and ACK (acknowledge). A SYN scan initiates this handshake by sending a SYN packet to the target port. If the port is open, the target responds with a SYN-ACK packet. However, the scanning tool does not complete the handshake by sending the final ACK packet. Instead, it logs the SYN-ACK response as an indication of an open port and then abruptly terminates the connection, leaving it “half-open.”
Responses to a SYN scan reveal port status:
- SYN-ACK: Indicates the port is likely open.
- RST (Reset): Indicates the port is closed.
- No Response: Suggests the port is filtered, or ICMP is blocked.
TCP half-open scans are the default scan type in Nmap due to their balance of speed and stealth.
TCP Connect Scan
The TCP connect scan mirrors the TCP half-open scan in its objective but differs in execution. Instead of halting the TCP handshake prematurely, a TCP connect scan completes the full three-way handshake, establishing a full TCP connection with the target port.
While functionally similar to SYN scans, TCP connect scans are less favored for a couple of reasons. Firstly, completing the full handshake generates more network traffic and “noise,” increasing the likelihood of detection. Secondly, establishing a full connection may trigger alarms in intrusion detection systems (IDS) that might overlook half-open connections. Target systems are also more likely to log full TCP connections, leaving a more substantial audit trail.
The primary advantage of TCP connect scans is that they do not require special privileges to execute. They utilize standard system calls for establishing connections, making them accessible to any user, unlike SYN scans which often require root privileges.
UDP Scan
UDP scans are generally slower and less reliable than TCP scans due to the connectionless nature of UDP. However, they are essential for identifying open UDP ports, which can host exploitable services, such as DNS. Security measures must protect UDP ports as diligently as TCP ports.
Effective UDP scanning often involves sending protocol-specific payloads. For instance, to check a DNS server, a DNS query is sent to UDP port 53. For generic UDP port scanning, an empty packet is typically transmitted. Responses vary:
- ICMP “Port Unreachable” Error: Indicates the port is closed.
- UDP Response: Suggests the port is open.
- No Response: Could mean the port is either open or filtered, requiring further investigation.
Using UDP scans to probe for specific services, like sending a DNS request to port 53, can effectively identify active services. Nmap incorporates pre-configured probes for numerous standard UDP services to streamline this process.
TCP vs UDP Protocol Differences
TCP and UDP are the two predominant protocols in IP networks. TCP is a connection-oriented protocol, emphasizing reliability. It ensures ordered packet delivery, error checking, and uses a three-way handshake for connection establishment and data integrity.
UDP, in contrast, is a connectionless protocol prioritizing speed over reliability. It lacks error checking and packet ordering, making it faster but less reliable for critical data transmission. Applications like live streaming and online gaming often utilize UDP for its speed advantages, where occasional packet loss is tolerable. UDP simply sends data without guaranteeing delivery or order.
Stealth Scan Techniques
Certain port scanning methods are designed to be less conspicuous, aiming to evade detection by security systems. These techniques manipulate TCP flags to achieve stealth.
-
FIN Scan: Sends TCP packets with only the FIN (finish) flag set. The expectation is that a closed port will respond with an RST (reset) packet, while an open port will likely ignore the FIN packet, resulting in no response. Firewalls configured to primarily monitor SYN packets might overlook FIN scans.
-
Xmas Scan: Sends packets with the FIN, URG (urgent), and PSH (push) flags set, resembling a “Christmas tree” in packet flags. Like FIN scans, the expected responses are RST for closed ports and no response for open ports. While less practically useful, it’s another technique to potentially bypass basic firewall filters.
-
Null Scan: Sends packets with no TCP flags set. The expected responses are similar to FIN and Xmas scans: RST for closed ports and no response for open ports.
The advantage of these stealth scans is their potential to bypass simple firewall rules and evade basic logging mechanisms. However, modern Intrusion Detection Systems (IDS) and network analysis tools like Wireshark are capable of detecting these scans. A limitation is that on Microsoft Windows systems, these scans typically only reliably identify closed ports; open ports may not be accurately reported. Nevertheless, if an open port is detected using these stealth methods, it often indicates a non-Windows target system.
Additional Port Scanning Techniques
Beyond the common techniques, several specialized scans serve specific purposes:
- TCP ACK Scan: Primarily used to map firewall rule sets by determining if ACK packets are filtered or allowed.
- TCP Window Scan: Can differentiate between open and closed ports in some systems by analyzing the TCP window size in responses, but its reliability varies across operating systems.
- Custom Scan (using
--scanflagsin Nmap): Allows advanced users to craft and send packets with arbitrary combinations of TCP flags for highly customized scans.
Essential Port Scanning Tools
Choosing the right port scanning tool depends on the specific needs and technical expertise of the user. Here are some notable tools:
-
Nmap (Network Mapper): As mentioned earlier, Nmap is the industry-standard, open-source port scanner. It’s incredibly versatile, supporting a wide range of scanning techniques (TCP SYN, UDP, FIN, Xmas, etc.), host discovery, OS detection, and scriptable interaction using NSE (Nmap Scripting Engine). Nmap is suitable for both beginners and advanced users due to its command-line interface and extensive documentation. It’s available on virtually all operating systems.
-
Zenmap: This is the official GUI for Nmap, making it more accessible to users who prefer a graphical interface. Zenmap provides all the power of Nmap with a visual representation of network scans and results, simplifying usage and analysis.
-
Angry IP Scanner: A lightweight and user-friendly IP address and port scanner. It is designed for speed and simplicity, scanning IP ranges and ports quickly. While less feature-rich than Nmap, it’s excellent for quick network checks and basic port scanning. It’s open-source and cross-platform.
-
Masscan: As the name suggests, Masscan is designed for extremely rapid scanning of large IP address ranges. It can transmit SYN packets asynchronously, achieving scan rates of millions of packets per second. Masscan is ideal for large-scale network surveys but may be less accurate than Nmap for detailed port status determination.
-
Unicornscan: Another high-performance scanner focused on speed and scalability. Unicornscan is designed for fast TCP/IP reconnaissance and correlation. It supports asynchronous stateless TCP scanning, UDP scanning, and TCP banner grabbing.
-
Netcat (nc): A versatile command-line utility often referred to as the “Swiss Army knife” of networking. Netcat can perform basic port scanning, but its capabilities extend far beyond that. It can be used for network debugging, data transfer, port listening, and as a backend tool in scripts. While not primarily a port scanner, its port scanning functionality is useful for quick checks.
-
Hping: A command-line oriented TCP/IP packet assembler/analyzer. Hping is more advanced than basic ping, capable of sending custom TCP, UDP, and ICMP packets. It can be used for port scanning, OS fingerprinting, and network testing. Hping is powerful for crafting specific network probes.
-
Metasploit Framework: While primarily a penetration testing framework, Metasploit includes robust port scanning capabilities as modules. It can leverage Nmap and its own scanning modules for vulnerability assessment and exploitation. Metasploit is for advanced security professionals conducting comprehensive security assessments.
Detecting Port Scanning Activities
Identifying port scanning attempts is crucial for proactive network defense. Several methods and tools can be employed:
-
Dedicated Port Scan Detectors: Specialized software applications like PortSentry and Scanlogd are designed specifically to monitor network traffic for patterns indicative of port scans. These tools often work by detecting multiple connection attempts to different ports from the same source IP address within a short timeframe.
-
Intrusion Detection Systems (IDS): Modern Intrusion Detection Systems are equipped to detect various types of port scans. Effective IDS solutions utilize a broad set of rules and signatures to identify different scanning techniques, not just relying on simple threshold-based detection. They can recognize stealth scans and more sophisticated scanning patterns.
-
Firewall Logs: Firewalls log network activity, and examining firewall logs can reveal port scanning attempts. Analyzing logs for denied connection attempts to multiple ports from a single source can indicate a port scan.
-
Security Information and Event Management (SIEM) Systems: SIEM systems aggregate logs and security events from various sources across the network, including firewalls, IDS, and servers. SIEM platforms can correlate events and identify port scanning activities by analyzing patterns across different log sources, providing a centralized view of security threats.
-
Host-Based Intrusion Detection Systems (HIDS): HIDS software installed on individual servers or endpoints can monitor local network connections and detect port scanning attempts targeting that specific host.
Why Perform Port Scans?
Proactive port scanning is a vital security practice. Regularly scanning your own networks allows you to:
- Identify Open Ports: Discover all open ports on your systems, which is essential for understanding your attack surface.
- Verify Security Posture: Confirm that only necessary ports are open and that services are running as expected.
- Detect Misconfigurations: Find unintended open ports that could represent vulnerabilities due to misconfigurations.
- Audit Security Controls: Test the effectiveness of firewalls and intrusion detection systems by simulating scanning attacks.
- Vulnerability Management: Identify potential vulnerabilities associated with running services on open ports and prioritize remediation efforts.
Regular, scheduled port scans should be part of a routine security assessment program. Furthermore, auditing open ports to ensure they are legitimate, necessary, and securely configured is paramount. Applications utilizing open ports must be hardened and protected against known vulnerabilities.
Considerations When Running Port Scans
While port scanning is a valuable security practice, be aware of potential implications:
-
Service Disruption: In rare cases, particularly with older or poorly configured systems, aggressive port scanning could potentially cause service disruptions or system instability, especially on internal networks. Exercise caution and consider the potential impact, especially in production environments.
-
Legal and Ethical Considerations: Performing port scans without authorization is illegal and unethical. Always ensure you have explicit permission to scan networks, especially if they are not under your direct control. Unauthorized scanning can be misconstrued as malicious activity.
Port scanning is a critical component of a robust cybersecurity strategy. By proactively identifying and mitigating potential vulnerabilities, organizations can significantly enhance their defenses against cyberattacks. Understanding port scanning techniques, utilizing appropriate tools, and implementing detection measures are essential skills for network administrators and security professionals dedicated to safeguarding digital assets.
Protecting network perimeters is just one aspect of comprehensive security. Equally important is securing the data itself. Solutions like Varonis Data Security Platform offer internal defenses to protect sensitive data and monitor activity to prevent data breaches.
To see data security in action against cyber threats, explore the Live Cyber Attack lab.