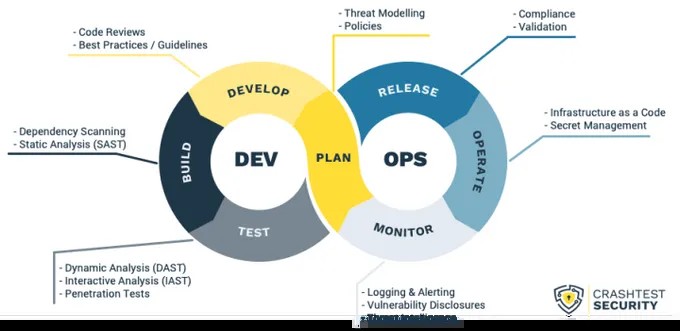
In today’s rapidly evolving digital landscape, ensuring robust security for web applications is paramount. While shifting security left during development is crucial, the vigilance shouldn’t end once an application goes live. Cyber threats are increasingly targeting live websites and applications, making post-production security testing just as vital as pre-deployment measures. Alarmingly, a significant portion of security vulnerabilities often remain undetected by developers before deployment, highlighting the critical need for ongoing security assessment in live environments.
This is where Dynamic Scanning Security Tools come into play. Dynamic scanning security tools, also known as Dynamic Application Security Testing (DAST) tools, offer a proactive approach to security by analyzing applications in their runtime environment. This method ensures that no security gaps are overlooked, providing continuous protection against emerging threats. With a plethora of DAST solutions available, choosing the right one that aligns with your DevOps team’s requirements and seamlessly integrates into your existing infrastructure is crucial. This guide will delve into the world of dynamic scanning security tools, exploring their benefits, essential features, and how they fit into a comprehensive security strategy for 2025 and beyond.
Understanding Dynamic Scanning Security Tools (DAST) and Their Functionality
Dynamic scanning security tools operate on the principle of “black box” testing. This means they analyze an application from an external perspective, simulating real-world attacks without needing access to the source code. By interacting with the application in its running state, DAST tools effectively mimic the techniques a malicious attacker would employ.
Unlike Static Application Security Testing (SAST), which examines the source code and dependencies at rest, DAST tools actively probe the live application.
DAST tools function by sending automated requests and payloads to the application, much like a cybercriminal attempting to exploit vulnerabilities. They then meticulously analyze the application’s responses and behavior to identify potential weaknesses. These weaknesses can range from misconfigurations to vulnerabilities susceptible to common attacks such as SQL injection and cross-site scripting (XSS).
Upon detection of vulnerabilities, dynamic scanning security tools generate detailed reports. These reports typically include a comprehensive overview of the vulnerability type, its severity level, and its location within the application. This detailed information empowers developers to efficiently address the identified security issues. Furthermore, many DAST solutions offer continuous, automated scanning capabilities, aligning with the principles of continuous security monitoring to provide ongoing protection.
Expert Insight: While dynamic scanning security tools are particularly effective for applications in production, their versatility allows for implementation across various stages of the Software Development Life Cycle (SDLC), depending on specific organizational security needs and strategies.
To maximize security effectiveness, consider integrating DAST with other security testing methodologies such as SAST and Software Composition Analysis (SCA). SCA tools, for example, specialize in examining open-source libraries and frameworks used within the application, complementing DAST’s runtime analysis. This layered security approach provides a more robust defense, significantly enhancing application security posture.
Key Advantages of Implementing Dynamic Scanning Security Tools
Integrating dynamic scanning security tools into your security strategy offers numerous compelling benefits:
- Real-World Vulnerability Detection: DAST tools simulate actual attack scenarios, providing invaluable real-time insights into how an application would withstand genuine cyber threats. This realistic testing approach accurately reflects the application’s security posture in a live environment.
- Comprehensive Application Coverage: Dynamic scanning security tools interact with all accessible application interfaces, ensuring thorough security coverage across the entire application footprint. This broad scope minimizes blind spots and reduces the risk of overlooked vulnerabilities.
- Ease of Integration and Use: DAST tools do not require access to the application’s source code, simplifying their deployment and usage. This is especially advantageous when assessing third-party applications where source code access is restricted.
- Runtime Vulnerability Identification: DAST excels at uncovering vulnerabilities that manifest only during runtime, such as authentication flaws, session management issues, and server misconfigurations. These runtime-specific vulnerabilities are often missed by static analysis techniques.
- Scalability for Growing Applications: DAST tools are designed for automation and seamless integration into the SDLC, facilitating scalable security testing across numerous applications. This scalability is crucial for organizations managing a growing portfolio of web applications.
- Compliance with Regulatory Standards: Many industry regulations and compliance frameworks, including HIPAA, GDPR, and SOC 2, mandate dynamic testing methodologies as essential for ensuring data protection and robust application security. DAST tools help organizations meet these stringent compliance requirements.
Essential Features to Look for in Dynamic Scanning Security Tools
When selecting a dynamic scanning security tool, prioritize these key features to ensure optimal effectiveness:
- Complete Automated Scanning Coverage: The tool should provide continuous, automated scanning of all exposed application interfaces to comprehensively identify potential vulnerabilities. Look for features that allow customizable scan schedules and depths to adapt to different application needs.
- Seamless Integration Capabilities: Ensure the DAST tool integrates smoothly into your existing DevSecOps pipeline. Integration with platforms like Jit streamlines security testing workflows, centralizes security management, and automates security processes across your development lifecycle.
- Real-Time, Actionable Insights: The tool should deliver detailed, accurate reports with clear remediation guidance based on real-time scan data. Prioritize tools that offer vulnerability prioritization based on risk and impact, enabling efficient risk mitigation workflows without causing operational disruptions.
- High Accuracy and Comprehensive Data: Opt for a DAST tool known for minimizing false positives and providing accurate, actionable alerts. The tool’s reporting should be comprehensive, offering sufficient detail to understand the vulnerability context, impact, and remediation steps.
Choosing the Right Dynamic Scanning Security Tool for 2025
Selecting the ideal dynamic scanning security tool depends on your organization’s specific needs, technical environment, and security maturity. Consider these factors when making your decision:
- Application Type and Architecture: Evaluate the types of web applications you need to scan (e.g., single-page applications, complex web services) and ensure the tool is compatible with your application architectures.
- Integration with Existing Toolchain: Prioritize tools that integrate seamlessly with your current DevSecOps ecosystem, including CI/CD pipelines, vulnerability management systems, and collaboration platforms.
- Reporting and Remediation Capabilities: Assess the tool’s reporting features, ensuring they provide clear, detailed vulnerability information and actionable remediation advice for developers.
- Scalability and Performance: Consider the tool’s ability to scale with your growing application portfolio and maintain performance without impacting application availability during scans.
- Support and Community: Evaluate the vendor’s support resources, documentation, and community presence. A strong support system and active community can be invaluable for troubleshooting and maximizing tool effectiveness.
For organizations seeking robust open-source options, OWASP ZAP stands out as a powerful and highly customizable dynamic scanning security tool, backed by a large and active community.
For those prioritizing ease of use and rapid deployment, solutions like Jit DAST offer streamlined configuration and comprehensive security coverage within a unified DevSecOps platform.
And for enterprises requiring advanced reporting and comprehensive compliance features, tools like Veracode provide enterprise-grade dynamic scanning security with in-depth insights and regulatory compliance support.
Conclusion: Proactive Security with Dynamic Scanning in 2025
Dynamic scanning security tools are indispensable for a proactive security strategy, particularly in safeguarding web applications against increasingly sophisticated cyberattacks. While crucial for production environments, they are a vital component of a holistic, end-to-end security plan that encompasses every stage of the SDLC.
By integrating dynamic scanning security tools with complementary security practices and technologies, organizations can build a robust security posture, ensuring the resilience and trustworthiness of their web applications in the face of evolving cyber threats. Embracing a comprehensive security approach that includes dynamic scanning is no longer optional but a necessity for navigating the complex security landscape of 2025 and beyond.