In the realm of network security, vigilance is paramount. Just as a car mechanic uses specialized tools to diagnose vehicle issues, network administrators and security professionals rely on Port Scan Detection Tools to identify potential vulnerabilities and safeguard their systems. Port scanning, while a valuable diagnostic technique, is also a common reconnaissance method used by attackers to discover entry points into your network. Understanding how to detect these scans is crucial for maintaining a robust security posture.
This article delves into the world of port scan detection, exploring:
- What port scanning is and why it’s a concern.
- The techniques attackers use to scan ports.
- Crucial port scan detection tools and methods to protect your network.
How Port Scanning Works: The Basics
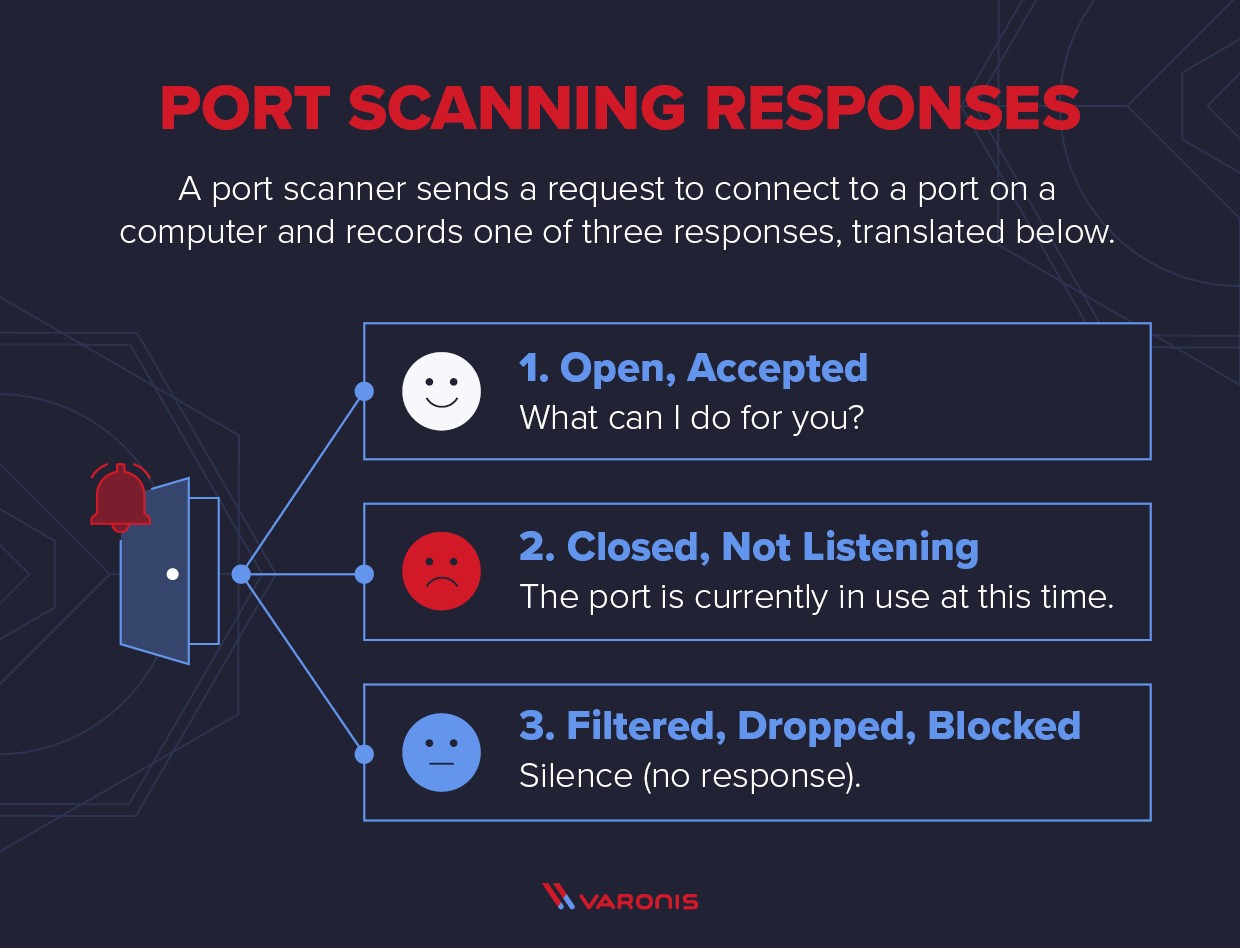
Imagine a vast building with numerous doors (ports), each potentially leading to different services or applications within a computer network. A port scan is like systematically checking each door to see if it’s open, closed, or locked (filtered).
Alt text: Diagram illustrating the three port scanning responses: Open/Accepted showing a computer responding positively, Closed/Not Listening displaying a “port unavailable” message, and Filtered/Dropped/Blocked where there is no response from the computer.
Essentially, a port scanner sends network requests to specific ports (TCP or UDP) on a target system and analyzes the responses. This process helps determine the status of each port, which falls into three categories:
- Open/Accepted: The port is active and listening for connections. This indicates a service is running and potentially accessible.
- Closed/Not Listening: The port is not in use, and the system actively refuses connections. While closed ports aren’t immediate vulnerabilities, they provide information about the system’s configuration.
- Filtered/Dropped/Blocked: No response is received. This usually means a firewall or other security device is blocking communication, masking the port’s true status.
For network administrators, port scans are invaluable for troubleshooting connectivity issues and verifying that services are running as expected. However, malicious actors exploit port scanning to identify open ports as potential entry points for cyberattacks. They can also deduce the types of devices and applications running on a network, such as firewalls, proxy servers, or VPN servers, which can inform their attack strategies.
Understanding Network Ports: The Gateway to Services
To fully grasp port scanning, it’s essential to understand what a port is. In networking terms, a port is a virtual endpoint for communication. Think of it as a numbered gate on a computer that directs network traffic to specific services or applications. Each computer has 65,536 TCP ports and 65,536 UDP ports, totaling 131,072 potential communication channels.
- TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are the two primary protocols used for internet communication.
Every device on a network has a unique IP address, like a street address for a house. When data packets are sent to an IP address, the port number within the packet header tells the computer which application or service should handle that data. Services needing to be accessible over a network “listen” on specific, designated ports.
The Internet Assigned Numbers Authority (IANA) standardizes port assignments. The first 1023 TCP ports are “well-known ports,” reserved for common applications:
- FTP (File Transfer Protocol): Port 21
- SSH (Secure Shell): Port 22
- HTTP (Hypertext Transfer Protocol): Port 80
- HTTPS (HTTP Secure): Port 443
Ports 1024 to 49151 are “registered ports,” available for various services and applications, and can be registered with IANA for standardization. Ports 49152 and above are “dynamic” or “private ports,” freely available for any use.
Port Scanning Techniques: Different Approaches to Discovery
Attackers employ various port scanning techniques to efficiently and stealthily probe networks. Understanding these methods is vital for choosing the right port scan detection tools and strategies.
Alt text: Diagram outlining five port scanning techniques: Ping Scan showing ICMP requests, TCP Half Open Scan utilizing SYN packets, TCP Connect Scan completing the TCP handshake, UDP Scan sending UDP packets, and Stealth Scanning using FIN, X-MAS, and Null packets.
Here are some common port scanning techniques:
-
Ping Scan (ICMP Scan): While technically not a port scan, ping scans are often the first step in reconnaissance. They send ICMP echo requests to a range of IP addresses to determine which systems are active and responding. Although basic firewalls can block ICMP, it’s still a widely used initial probing method.
-
TCP Half-Open Scan (SYN Scan): This is a popular and stealthier technique. It initiates a TCP connection by sending a SYN (synchronize) packet but doesn’t complete the full three-way handshake. If a SYN-ACK (synchronize-acknowledge) response is received, it indicates an open port. An RST (reset) response signifies a closed port. No response suggests the port is filtered. SYN scans are fast and less likely to be logged compared to full TCP connections. Nmap uses this as its default scan type.
-
TCP Connect Scan: This method completes the full TCP three-way handshake, establishing a full connection with the target port. While reliable, it’s less stealthy than a half-open scan as completed connections are more likely to be logged by intrusion detection systems (IDS) and target systems. It also requires more packets per scan, increasing network traffic. However, TCP connect scans don’t require special privileges to execute, making them accessible to any user.
-
UDP Scan: UDP scans are generally slower and less reliable than TCP scans due to UDP’s connectionless nature. To scan a UDP port, a UDP packet is sent to the target port. If an ICMP “unreachable” response is received, it usually indicates a closed or filtered port. If a UDP response is received, it suggests the port is open. No response could mean either an open port or a filtered port, making interpretation less straightforward. Sending protocol-specific payloads (like DNS requests to port 53) can improve UDP scan accuracy for specific services.
-
Stealth Scans (FIN, X-MAS, NULL Scans): These techniques leverage TCP flags to attempt to evade detection.
- FIN Scan: Sends a FIN (finish) packet. A lack of response suggests an open or filtered port, while an RST response indicates a closed port. Firewalls often don’t monitor FIN packets as closely as SYN packets.
- X-MAS Scan: Sends a packet with FIN, URG (urgent), and PUSH flags set, resembling a “Christmas tree.” The expected responses are similar to a FIN scan: RST for closed, no response for open/filtered.
- NULL Scan: Sends a packet with no TCP flags set. Responses are also RST for closed and no response for open/filtered.
These stealth scans are less likely to be logged by basic systems but are detectable by modern Intrusion Detection Systems (IDS) and network monitoring tools like Wireshark. Notably, on Microsoft Windows systems, these scans may only reliably identify closed ports. Their primary advantage is potential evasion of simpler firewalls.
-
Other Scanning Techniques: Beyond these common methods, more specialized scans exist:
- TCP ACK Scan: Used to map firewall rulesets by determining if ACK packets are filtered or allowed.
- TCP Window Scan: Exploits TCP window size responses to differentiate between open and closed ports, though it’s not universally reliable across all systems.
- Custom Flag Scans (–scanflags in Nmap): Advanced users can craft scans with custom TCP flags for highly specific probing scenarios.
Port Scanning Tools: Weapons for Both Offense and Defense
Port scanning tools are software applications designed to perform network port scans. While attackers use them for malicious reconnaissance, security professionals and network administrators utilize them for vulnerability assessments and security audits. Effective port scan detection tools are crucial for recognizing and mitigating both types of scans.
Popular port scanning tools include:
-
Nmap (Network Mapper): The industry-standard, open-source port scanner. Nmap is incredibly versatile, supporting a wide range of scanning techniques (TCP, UDP, SYN, FIN, XMAS, etc.), operating system detection, version detection, and scripting. It’s available for virtually all operating systems and is a powerful tool for both offensive and defensive security tasks.
-
Netcat: A command-line utility often referred to as the “Swiss Army knife” of networking. Netcat can perform basic port scanning, but its capabilities extend far beyond. It can create network connections over TCP or UDP, act as a listener, transfer files, and even be used to set up simple chat servers. Its flexibility makes it useful for various network troubleshooting and security tasks.
-
Hping: Another command-line oriented network tool, Hping excels at crafting custom TCP/IP packets. It’s particularly useful for advanced port scanning and network probing scenarios where precise control over packet headers and flags is needed. Hping can perform various scan types, including SYN, UDP, ICMP, and others.
-
Masscan: As the name suggests, Masscan is designed for extremely fast scanning of large IP address ranges. It can scan the entire internet in minutes, making it suitable for large-scale network discovery. However, its speed comes with trade-offs in terms of stealth and feature richness compared to Nmap.
-
Angry IP Scanner: A user-friendly, cross-platform IP address and port scanner with a graphical interface. It’s easy to use for quickly scanning local networks and identifying active hosts and open ports. While less feature-rich than Nmap, its simplicity makes it a good choice for basic scanning tasks.
How to Detect a Port Scan: Fortifying Your Defenses with Detection Tools
Recognizing port scan attempts is critical for proactive network security. Several port scan detection tools and methods can help identify suspicious scanning activity:
Alt text: Diagram showing four port scanning detection methods: Port Scan Detector Software, Intrusion Detection Systems (IDS), Firewall Logs, and Security Information and Event Management (SIEM) systems, each with brief descriptions.
-
Dedicated Port Scan Detector Software: Specialized applications are designed specifically to monitor network traffic and detect port scanning patterns. Examples include:
- PortSentry: A host-based intrusion detection system focused on port scan detection. It monitors ports and can take actions like blocking the source IP address when a scan is detected.
- Scanlogd: Another lightweight port scan detector that logs scan attempts. It’s designed to be efficient and provide clear logs of scanning activity.
-
Intrusion Detection Systems (IDS): Network-based or host-based IDSs analyze network traffic for malicious activity, including port scans. Modern IDSs employ rule-based detection, anomaly detection, and signature-based detection to identify various scanning techniques, not just simple threshold-based alerts. Look for IDSs that can recognize SYN scans, stealth scans, UDP scans, and other advanced techniques.
-
Firewall Logs: Firewalls are the first line of defense and often log connection attempts, including those from port scans. Analyzing firewall logs can reveal patterns indicative of scanning activity. Look for logs showing numerous connection attempts to different ports from the same source IP address within a short timeframe.
-
Security Information and Event Management (SIEM) Systems: SIEM systems aggregate logs and security events from various sources across your infrastructure, including firewalls, IDSs, servers, and applications. They provide a centralized platform for security monitoring and analysis. SIEMs can correlate events and identify port scan patterns that might be missed by individual systems, offering a comprehensive view of security threats.
Why Proactive Port Scanning is Essential for Security
While detecting external port scans is crucial, organizations should also conduct proactive internal port scans as a vital part of their security strategy. Regular internal scans help:
- Identify Open and Unnecessary Ports: Discovering open ports that are not required for legitimate business operations allows you to close them, reducing the attack surface.
- Verify Security Controls: Ensure that firewalls and other security devices are correctly configured and effectively blocking unauthorized access.
- Audit Open Services: Regularly review services running on open ports to confirm they are necessary, securely configured, and patched against known vulnerabilities.
- Maintain a Secure Baseline: Proactive scanning establishes a baseline of expected open ports, making it easier to detect unauthorized changes or newly opened ports that could indicate a compromise.
However, be mindful of the implications of running port scans:
- Potential Service Disruption: In rare cases, aggressive port scans might cause older or poorly configured systems to malfunction, especially within internal networks.
- Authorization is Key: Always ensure you have proper authorization before scanning any network, especially if it’s not your own. Unauthorized port scanning can be considered illegal and unethical.
In conclusion, understanding port scanning and utilizing effective port scan detection tools are fundamental aspects of modern cybersecurity. By proactively scanning your own networks, diligently monitoring for external scan attempts, and implementing robust detection mechanisms, you can significantly enhance your network security posture and stay one step ahead of potential attackers. Just as a mechanic relies on diagnostic tools to maintain a vehicle’s health, network defenders must leverage port scan detection tools to ensure the ongoing security and resilience of their digital infrastructure.