Network security is paramount in today’s digital landscape. Understanding your network’s vulnerabilities is the first step towards robust protection. This comprehensive guide delves into the world of Tools Network Scanning, providing insights into their functionality, benefits, and key considerations for choosing the right solution.
Why Tools Network Scanning is Crucial
Tools network scanning plays a vital role in maintaining a secure and efficient network infrastructure. These tools provide a proactive approach to identifying potential security risks and performance bottlenecks before they escalate into major issues. Here’s why network scanning matters:
- Threat Detection: Uncover hidden vulnerabilities and security loopholes that could be exploited by malicious actors.
- Compliance: Meet industry regulations and security standards by proactively identifying and addressing vulnerabilities.
- Performance Optimization: Identify network bottlenecks and performance issues to ensure optimal network efficiency.
- Cost Savings: Prevent costly security breaches and downtime by addressing vulnerabilities and performance issues early on.
Exploring the Best Tools Network Scanning Solutions
The market offers a diverse range of tools network scanning solutions, each with its own strengths and weaknesses. Let’s examine some of the leading contenders:
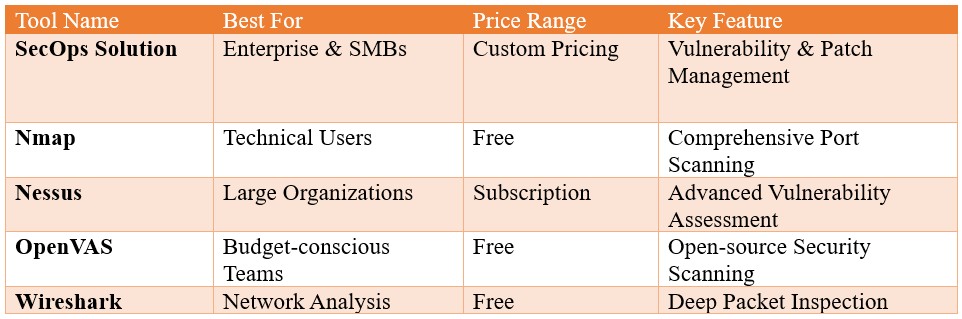
1. SecOps Solution
SecOps Solution is a comprehensive, agentless vulnerability and patch management platform. It enables swift identification, prioritization, and remediation of vulnerabilities across your entire infrastructure. Key features include automated patch management, detailed vulnerability assessments, and flexible deployment options.
 SecOps Solution Interface
SecOps Solution Interface
2. Nmap (Network Mapper)
Nmap, a powerful open-source tool, is a cornerstone in network exploration and security auditing. Its versatility lies in its support for various scan types, ranging from host discovery and port scanning to OS fingerprinting. Nmap’s extensibility through scripting allows for customized functionality.
3. Nessus
Nessus is a widely recognized vulnerability scanner known for its comprehensive security assessments. It provides detailed reports on vulnerabilities, misconfigurations, and malware, enabling effective risk prioritization. Nessus caters to both internal and external scanning needs.
4. OpenVAS (Open Vulnerability Assessment System)
OpenVAS, a free and open-source vulnerability scanner, offers comprehensive security assessments. Its continuously updated vulnerability database ensures accurate and timely results. OpenVAS’s customizability allows for tailored scans based on specific requirements.
5. Wireshark
Wireshark, a renowned network protocol analyzer, captures and analyzes network packets in real-time. This capability empowers network administrators to troubleshoot issues, pinpoint performance bottlenecks, and detect suspicious network activities. Wireshark’s extensive protocol support makes it indispensable for in-depth network analysis.
Selecting the Right Tools Network Scanning Solution
Choosing the optimal tools network scanning solution requires careful consideration of several factors:
- Organization Size and Complexity: Enterprise-grade solutions cater to large, complex networks, while smaller organizations might benefit from more streamlined tools.
- Technical Expertise: Consider the skill level of your team and the learning curve associated with different tools.
- Budget: Evaluate the cost of various solutions, including licensing fees, maintenance, and support. Open-source options provide cost-effective alternatives.
- Specific Requirements: Identify your specific security and performance needs to determine the most suitable tool.
Conclusion
Implementing effective tools network scanning is essential for safeguarding your network infrastructure. By proactively identifying and addressing vulnerabilities, you can strengthen your security posture, optimize network performance, and prevent costly incidents. Choose the solution that best aligns with your organization’s unique requirements and embark on the path to a more secure and efficient network.
