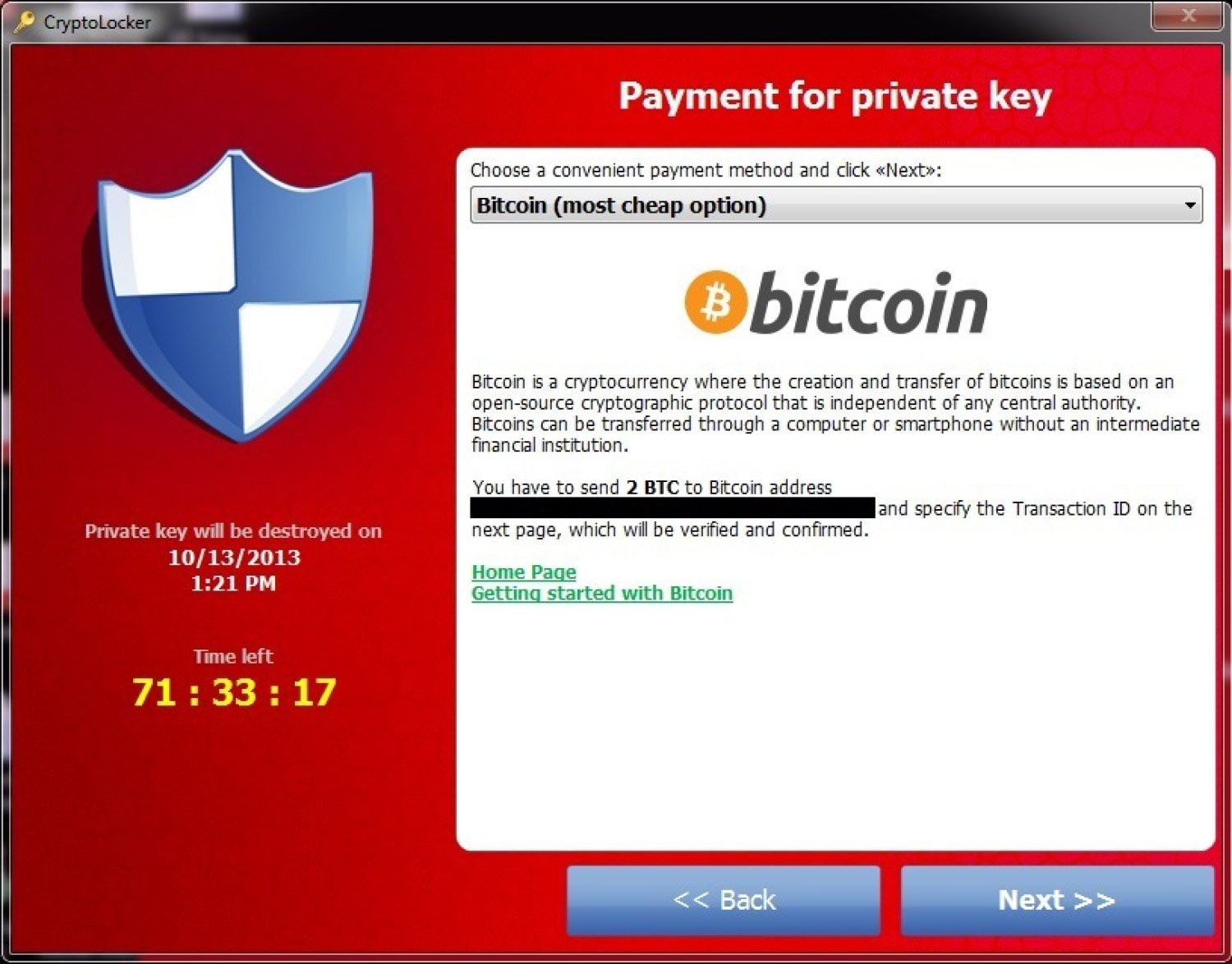
CryptoLocker, a notorious ransomware, inflicted significant damage on organizations reliant on data around 2015. Upon execution, this malware encrypted files on both local machines and shared network drives, effectively holding critical data hostage. Victims attempting to access their files were met with a ransom demand, hence the term “ransomware.”
Malware such as CryptoLocker infiltrated networks through various channels, including email phishing, file-sharing platforms, and malicious downloads. Its sophisticated nature allowed it to circumvent traditional antivirus software and firewall defenses. It was clear that preventative measures alone were insufficient; detective and corrective security controls became vital as a secondary line of defense.
Understanding the Threat Landscape in 2015
It’s important to remember the cybersecurity context of 2015. While ransomware was not a new concept, CryptoLocker and its variants represented a significant escalation in sophistication and impact. Businesses were actively seeking solutions, and the idea of a dedicated “Cryptolocker Scan Tool 2015” was a natural question.
Were there specific tools marketed as “cryptolocker scan tools” in 2015? The answer is nuanced. Dedicated, single-purpose tools specifically labeled “CryptoLocker Scan Tool 2015” were not widely prevalent in the way we might think of antivirus software today. Instead, the approach to detecting and mitigating CryptoLocker in 2015 relied on a combination of strategies and existing security technologies, adapted to address this specific threat.
What CryptoLocker Did to Systems in 2015
Upon infecting a system, CryptoLocker initiated a scan of mapped network drives accessible to the compromised host, searching for folders and documents. It then proceeded to encrypt files it had permission to modify, based on the user’s access rights. This encryption process involved renaming files and appending extensions like .encrypted, .cryptolocker, or a random set of characters, depending on the specific CryptoLocker variant. A crucial step was the creation of ransom notes within each affected directory, typically named DECRYPT_INSTRUCTION.txt or DECRYPT_INSTRUCTIONS.html, providing payment instructions, often demanding Bitcoin, for file decryption.
Variants like CTB-Locker emerged, creating files named !Decrypt-All-Files-[RANDOM 7 chars].TXT or !Decrypt-All-Files-[RANDOM 7 chars].BMP in the initial encryption directory. Staying informed about these evolving variants was crucial in 2015, and resources like online security communities played a vital role in sharing up-to-date information.
CryptoLocker Prevention Strategies in 2015 (and Still Relevant)
Limiting user access rights was, and remains, a fundamental prevention strategy. The principle is simple: the fewer files a user can access, the less damage ransomware can inflict. Implementing a least privilege model was a key recommendation in 2015, and it continues to be a best practice today. This involves restricting user access to only the data and resources absolutely necessary for their roles, minimizing the potential impact of a ransomware attack.
Quick, impactful steps included removing overly permissive global access groups from access control lists. Groups like “Everyone,” “Authenticated Users,” and “Domain Users,” commonly used on folders and SharePoint sites, created broad vulnerabilities. These “open shares” were easy targets for malware. Identifying and securing these shares was a priority.
While specialized tools for global access group identification existed even in 2015, basic techniques could also be employed. Creating a user account with minimal permissions and using network commands like net view, net use, and dir /s could help identify accessible shares manually. While remediation without dedicated software could be time-consuming, the principle of reducing broad access was paramount in mitigating CryptoLocker risks in 2015. Automated solutions were available then, as they are now, to streamline this process and enforce least privilege more effectively.
Detecting CryptoLocker Activity: What to Look For (Then and Now)
For organizations monitoring file access activity, unusual patterns were a key indicator of CryptoLocker infection. The rapid encryption process generated a surge of file system events – opens, modifications, and creations – in a short timeframe. Automated monitoring solutions were valuable for detecting these anomalies. For instance, a sudden burst of hundreds of file modifications by a single user account within minutes was a strong sign of malicious activity. Configuring monitoring systems to trigger alerts based on such behavior was a crucial detective control in 2015. Solutions like Varonis DatAlert were available to monitor file system behavior specifically for ransomware patterns.
For those without automated monitoring in 2015, enabling native auditing was a less efficient but possible approach. However, native auditing was resource-intensive and produced complex logs. A more targeted manual method involved setting up file share honeypots – decoy file shares containing seemingly valuable but fake files. Any access to these honeypots was suspicious and warranted immediate investigation. Manual detection also involved analyzing security event logs using scripts to identify unusual access patterns related to honeypots or sensitive file areas.
PowerShell scripts were also utilized to combat CryptoLocker. These scripts could check for registry keys associated with CryptoLocker, enabling automated responses like disabling compromised user accounts. This rapid response capability was essential to limit the damage.
Preserving and analyzing file access logs was critical for recovery. These logs provided a record of affected files and user accounts, aiding in restoration from backups or shadow copies. Depending on the CryptoLocker variant, decryption might have been possible, sometimes with specialized tools, though this was not a guaranteed solution.
Was There a Dedicated “CryptoLocker Scan Tool 2015”?
In summary, while a specific product branded as a “cryptolocker scan tool 2015” might not have been widely marketed, the concept of scanning for and detecting CryptoLocker was central to security practices in that era. The “scan tools” of 2015 were more accurately described as methodologies and existing security technologies adapted to identify CryptoLocker activity. These included:
- Antivirus Software: While often bypassed initially, updated antivirus definitions were crucial for catching later stages or less sophisticated variants.
- File Monitoring Solutions: Tools that tracked file access and modifications were key to detecting the rapid encryption process.
- Network Intrusion Detection Systems (IDS): While not solely focused on CryptoLocker, network monitoring could identify suspicious traffic patterns associated with malware distribution.
- Manual Auditing and Scripting: PowerShell and other scripting tools allowed for manual checks and automated responses based on observed system behavior.
- Honeypots: Decoy file shares acted as early warning systems.
The focus in 2015, and continuing today, was on a layered security approach rather than relying on a single “scan tool.”
Ransomware Safety Tips: Timeless Advice from 2015
The ransomware safety tips relevant in 2015 remain remarkably pertinent today:
- Keep Antivirus Updated: Essential for detecting and preventing known ransomware strains.
- Be Vigilant Against Phishing: Phishing emails were and are a primary delivery method for ransomware.
- Maintain Regular Backups: The fastest and most reliable recovery method after a ransomware attack.
- Implement Least Privilege: Limit the potential damage by restricting user access rights.
- Monitor File Activity: Detect and respond to ransomware activity quickly through file system monitoring.
While the threat landscape has evolved since 2015, with ransomware becoming more targeted and sophisticated, the fundamental principles of prevention, detection, and response remain constant. The “cryptolocker scan tool 2015” was, in essence, the broader cybersecurity strategy of that time, utilizing available technologies and best practices to defend against this significant threat. Today, these principles are still foundational in combating modern ransomware attacks.