Network scanning tools are crucial for maintaining a strong security posture and ensuring optimal network performance. These tools provide insights into network vulnerabilities, identify connected devices, and help prevent potential security breaches. This guide explores the various Tools Used For Network Scanning, their features, and how to choose the right one for your needs.
Types of Network Scanning Tools
Network scanning tools can be broadly categorized based on their functionality:
1. Port Scanners
Port scanners are fundamental tools that examine network ports to determine their status (open, closed, filtered). This information helps identify potential vulnerabilities and services running on a network. Popular port scanners include:
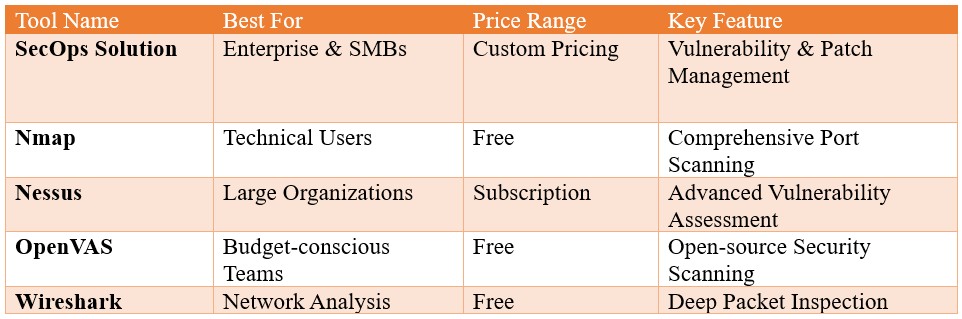
- Nmap (Network Mapper): A powerful and versatile open-source scanner known for its comprehensive scanning capabilities and scripting flexibility.
 Nmap
Nmap - Zenmap: A graphical user interface for Nmap, making it more user-friendly for beginners.
- Angry IP Scanner: A lightweight and cross-platform scanner for quickly identifying live hosts and open ports.
2. Vulnerability Scanners
Vulnerability scanners go beyond port scanning by actively probing for known security weaknesses in systems and applications. They provide detailed reports on vulnerabilities and often offer remediation guidance. Leading vulnerability scanners include:
- Nessus: A widely used commercial scanner known for its comprehensive vulnerability database and accurate results.
- OpenVAS (Open Vulnerability Assessment System): A free and open-source alternative to Nessus, offering robust scanning capabilities.
- Acunetix: A specialized scanner focused on web application vulnerabilities.
3. Network Mappers
Network mappers automatically discover and document network devices and their connections, creating a visual representation of the network topology. Examples include:
- SolarWinds Network Performance Monitor (NPM): A commercial tool offering real-time network monitoring and mapping capabilities.
- Wireshark: A powerful network protocol analyzer that captures and inspects network traffic, aiding in troubleshooting and security analysis.
Choosing the Right Network Scanning Tool
Selecting the appropriate network scanning tool depends on several factors:
- Network Size and Complexity: Larger networks may require more scalable and powerful tools.
- Security Requirements: Organizations with stringent security needs should opt for comprehensive vulnerability scanners.
- Technical Expertise: User-friendly tools with graphical interfaces are suitable for beginners, while command-line tools like Nmap offer greater flexibility for experienced users.
- Budget: Free and open-source tools like Nmap and OpenVAS are excellent options for budget-conscious users, while commercial tools often provide advanced features and support.
Best Practices for Network Scanning
To maximize the effectiveness of network scanning:
- Establish a Regular Scanning Schedule: Frequent scans are essential for detecting new vulnerabilities and maintaining security.
- Ensure Comprehensive Coverage: Scan all network segments and devices to avoid overlooking potential weaknesses.
- Manage False Positives: Properly configure scanning tools to minimize false positive results, which can waste time and resources.
- Develop a Response Plan: Establish procedures for addressing identified vulnerabilities and security incidents.
Conclusion
Network scanning tools are indispensable for maintaining a secure and efficient network environment. By understanding the different types of tools available and following best practices, organizations can proactively identify and mitigate security risks, ensuring the integrity and availability of their network infrastructure. Choosing the right tool and implementing a consistent scanning strategy are crucial steps in building a robust cybersecurity defense.
